COMPLIANCE FRAMEWORK
HIPAA Compliance
Healthcare delivery organizations are subject to the Health Insurance Portability and Accountability Act (HIPAA), a US law that protects patient records. HIPAA-covered entities are required to notify authorities of breaches of unsecured protected health information (PHI) and are subject to fines for HIPAA violations.
Get a Demo
Ensure HIPAA Compliance
What are the HIPAA Compliance Requirements?
HIPAA compliance and cybersecurity are two concepts that work in parallel with each other. Cybersecurity is covered by the Security Rule which falls uner HIPAA’s Title II. Cybersecurity measures protect PHI from unauthorized access, disclosure, or destruction. All organizations handling PHI must have security measures in place that will fulfill HIPAA’s four major rules for compliance. They are ensuring the confidentiality, integrity, and availability of e-PHI; identify and protect against threats; protect against misuse of information; and ensure workforce compliance.
Understand
Improve your understanding of current security risks and prioritization of critical activities
Protect
Identification of mitigation strategies and evaluation of potential tools and processes
Respond
Define the process for identifying, responding to, and mitigating the impact of cybersecurity incidents.
IoT Device Security in 2024:
The High Cost of Doing Nothing
Protecting the growing IoT architecture
in a complicated security environment
Safe, Comprehensive, Categorized
How Asimily Supports HIPAA Compliance
Asimily adopts a risk-oriented approach to vulnerability management, empowering customers with the ability to determine how likely it is for a threat actor to exploit a given vulnerability. This informs risk-based prioritization and streamlines resolving business-critical weaknesses in your IoT devices.
Continuous Threat Detection
Asimily empowers you to stay one step ahead of cybercriminals and others who benefit from taking down high-profile targets. With cutting-edge threat detection systems, we provide real-time visibility into your IoT device fleet, enabling rapid response to emerging threats.
Incident Response
Asimily integrates with common network access control (NAC) and firewall solutions. Administrators can quarantine devices, preventing them from communicating with other machines on the network, without interrupting their investigation. During an attack, time is of the essence and responding quickly can prevent an incursion from spreading laterally and causing serious damage.
Disaster Recovery
Asimily baselines optimal performance state with a snapshot to replicate device configurations. Having this snapshot can allow organizations to retain the optimal configuration, saving a tremendous amount of time and providing peace of mind.
HHS Office for Civil Rights Proposes Significant Expansion of HIPAA Security Rule to Encompass Medical Devices
The latest proposed updates to HIPAA serve as a crucial pulse check for IoMT security, raising the bar for healthcare organizations. Understand the key takeaways from the recent NPRM and learn how to stay compliant in 2025.
Learn How
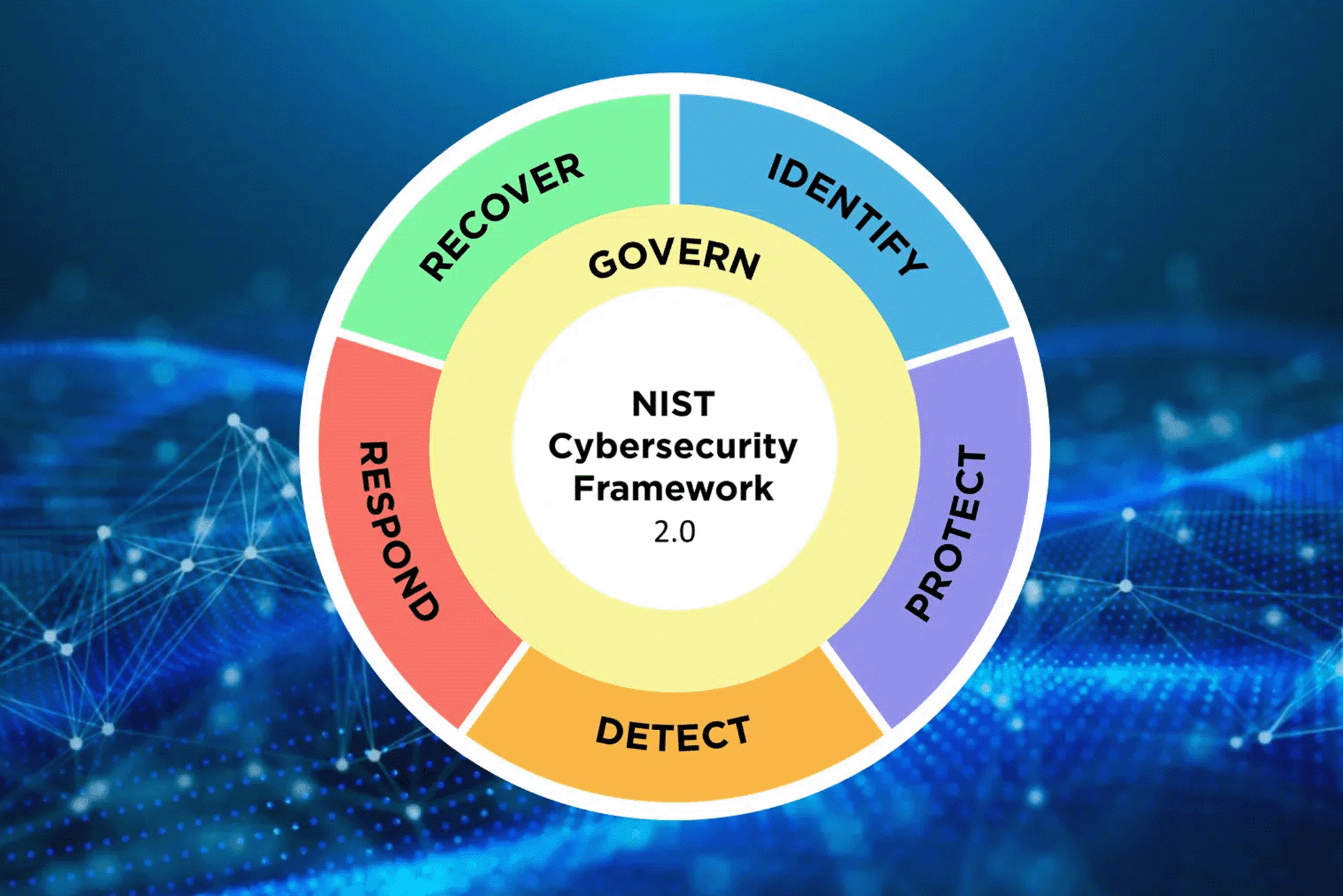
What You Should Know about NIST CSF 2.0
Stay ahead of the game by checking out our latest blog post where we break down the recent updates of the NIST CSF 2.0 pivotal framework.
Dive Deeper