What You Should Know about NIST CSF 2.0
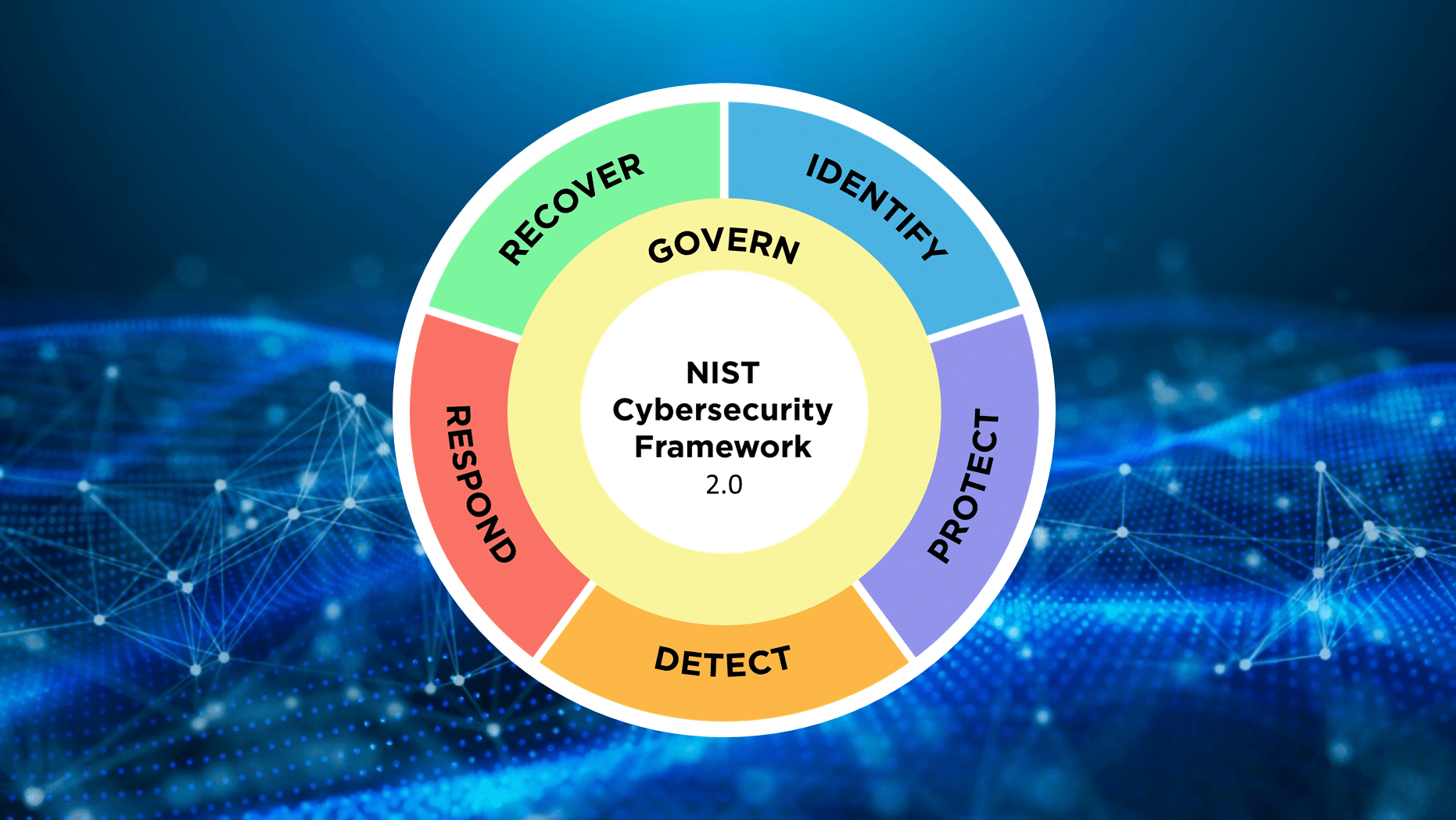
On February 26, 2024, the National Institute of Standards and Technology (NIST) released the long-awaited publication The NIST Cybersecurity Framework (CSF) 2.0. Although the news of the second version sounds highly overwhelming, comparing version 1.1 with 2.0 shows that many of the changes to the CSF expand and explain previously existing categories and subcategories.
As organizations across various industries implement the framework to identify and mitigate risks, understanding NIST CSF 2.0 is critical to achieving security and compliance initiatives.
Why did NIST update the CSF?
NIST recognizes that cybersecurity risks continuously evolve, meaning that ways of managing them need to shift. The CSF maintains its flexibility by responding to the various differences across organizations, including their:
- Common and unique risks
- Varying risk appetites and tolerances
- Specific missions
- Objectives to achieve missions
To achieve these, CSF 2.0 incorporates new features specifically related to governance and supply chain, paying attention to the differing needs of larger and smaller organizations. To enable these various users, CSF 2.0 incorporates Implementation Examples and Informative References.
Further, NIST CSF 2.0 attempts to more fully address the overlap between cybersecurity and privacy risks related to privacy events, better aligning its Cybersecurity and Privacy frameworks.
What to know about changes to NIST CSF
The new publication primarily expands activity descriptions and offers examples for how to implement these activities. Fundamentally, the CSF 2.0 Core retains the same basic organization as the previous version with
- Functions: highest level of organization for cybersecurity outcomes
- Categories: groups of security activities across the cybersecurity risk management life cycle of Govern, Identify, Protect, Detect, Respond, Recover
- Subcategories: individual risk mitigation activities
While language has been updated from 1.1 to 2.0, many of the pre-existing or new Subcategories remain essentially the same.
A review of the Informative References for the Risk Assessment Category within the Identify Function provides insight when:
| CSF 2.0 | Informative References to CSF 1.1 |
| ID.RA-01: Vulnerabilities in assets are identified, validated, and recorded | ID.RA-1: Asset vulnerabilities are identified and documentedPR.IP-2: A System Development Life Cycle to manage systems is implemented DE.CM-8: Vulnerability scans are performed |
| ID.RA-05: Threats, vulnerabilities, likelihoods, and impacts are used to understand inherent risk and inform risk response prioritization | ID.RA-5: Threats, vulnerabilities, likelihoods, and impacts are used to determine risk |
| ID.RA-08: Processes for receiving, analyzing, and responding to vulnerability disclosures are established | RS.AN-5: Processes are established to receive, analyze and respond to vulnerabilities disclosed to the organization from internal and external sources (e.g. internal testing, security bulletins, or security researchers) |
| ID.RA-09: The authenticity and integrity of hardware and software are assessed prior to acquisition and use | PR.DS-8: Integrity checking mechanisms are used to verify hardware integrity |
| ID.RA-10: Critical suppliers are assessed prior to acquisition | ID.SC-2: Suppliers and third party partners of information systems, components, and services are identified, prioritized, and assessed using a cyber supply chain risk assessment process ID.SC-4: Suppliers and third-party partners are routinely assessed using audits, test results, or other forms of evaluations to confirm they are meeting their contractual obligations. |
CSF 2.0 focuses on the same types of risk mitigation activities, but it consolidates and reorganizes them in a way that makes more sense.
The Governance Function
Although the new Governance Function garnered a lot of media interest and industry speculation, all of the Categories and most of the Subcategories existed in CSF version 1.1. Most of the Governance Subcategories were embedded as activities across the Identify, Protect, Detect, Respond, and Recover Categories.
NIST CSF 2.0 defines the Governance function as:
The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
Within this new Function, it lists the following Categories:
- Organizational Context (GV.OC): mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements around the risk management decisions
- Risk Management Strategy (GV.RM): priorities, constraints, risk tolerance and appetite statements, and assumptions that support risk decisions
- Roles, Responsibilities, and Authorities (GV.RR): roles, responsibilities, and authorities for accountability, performance assessment, and continuous improvement
- Policy (GV.PO): cybersecurity policy established, communicated, and enforced
- Oversight (GV.OV): risk management activities and performance used to adjust strategy
- Cybersecurity Supply Chain Risk Management (GV.SC): supply chain risk management processes implemented and approved
Across the Governance Function’s 31 Subcategories, the following are not included in any of the references to CSF version 1.1:
- GV.RM-07: Strategic opportunities (i.e., positive risks) are characterized and are included in organizational cybersecurity risk discussions
- GV.RR-01: Organizational leadership is responsible and accountable for cybersecurity risk and fosters a culture that is risk-aware, ethical, and continually improving
- GV.OV-01: Cybersecurity risk management strategy outcomes are reviewed to inform and adjust strategy and direction
- GV.OV-02: The cybersecurity risk management strategy is reviewed and adjusted to ensure coverage of organizational requirements and risks
- GV.OV-03: Organizational cybersecurity risk management performance is evaluated and reviewed for adjustments needed
While NIST notes that CSF 2.0 places more attention on Cybersecurity Supply Chain Risk Management, the newly titled Category was previously under the Identify Function in CSF 1.1 under Supply Chain Risk Management (ID.SC). CSF 2.0 expands upon the original five Subcategories, creating ten overall. However, most of these changes are more detailed explanations of the previous activities.
Additional New Subcategories
Across the revision, NIST included the following new Subcategories that have no Informative Reference to NIST CSF 1.1:
| Function and Category | Subcategory |
| Identify: Asset Management | ID.AM-07: Inventories of data and corresponding metadata for designated data types are maintained |
| Identify: Improvement | ID.IM-01: Improvements are identified from evaluations |
| Protect: Identity Management, Authentication, and Access Control | PR.AA-04: Identity assertions are protected, conveyed, and verified |
| Protect: Platform Security | PR.PS-05: Installation and execution of unauthorized software are prevented |
| Respond: Incident Management | RS.MA-05: The criteria for initiating incident recovery are applied |
| Respond: Incident Analysis | RS.AN-07: Incident data and metadata are collected, and their integrity and provenance are preserved |
| Respond: Incident Analysis | RS.AN-08: An incident’s magnitude is estimated and validated |
| Recover: Incident Recovery Plan Execution | RC.RP-03: The integrity of backups and other restoration assets is verified before using them for restoration |
| Recover: Incident Recovery Plan Execution | RC.RP-04: Critical mission functions and cybersecurity risk management are considered to establish post-incident operational norms |
| Recover: Incident Recovery Plan Execution | RC.RP-05: The integrity of restored assets is verified, systems and services are restored, and normal operating status is confirmed |
| Recover: Incident Recovery Plan Execution | RC.RP-06: The end of incident recovery is declared based on criteria, and incident-related documentation is completed |
Asimily: Internet of Things (IoT) Risk Management Aligned to NIST CSF
Asimily’s IoT risk management platform creates a complete IoT inventory so organizations can identify vulnerabilities and prioritize remediation actions, enabling them to mitigate risks in a way that aligns to the NIST CSF. The platform conducts a full flow analysis for each device, recording all communication patterns across the network so organizations can calculate risk, giving them the ability to set policies, monitor accepted risks, and proactively identify suspicious activity.
Asimily enables organizations to implement Incident Response Plans and workflows that incorporate the typically difficult-to-manage IoT devices by automating packet capture for forensic analysis of any IoT device, supporting root cause analysis.
As organizations adopt new IoT devices, they can engage in pre-procurement risk assessments that enable them to more accurately identify cybersecurity supply chain risks and implement appropriate mitigation actions.
To find out how Asimily can help manage the security risk of connected devices for your business, download our white paper: IoT Device Security in 2024: The High Cost of Doing Nothing whitepaper.

Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




