IoMT Security Threat Detection and Incident Response
Many clinical engineers focus their daily activities on identifying a medical device’s serial number, MAC address, and IP address so they can install patches. However, as threat actors increasingly target Internet of Medical Things (IoMT) devices, the clinical engineer’s role takes on a new, important cybersecurity role.
To reduce the likelihood of a cyberattack and recovery costs, HDOs need robust IoMT security threat detection, business continuity, and disaster recovery plans incorporating IoMT documentation and monitoring.
In a connected world, healthcare delivery organizations (HDOs) deal with a barrage of attacks and rising data breach costs. According to the 2023 Protenus Breach Barometer Report:
- 75% of all reported incidents in 2023 were caused by hacking
- 86% of all breached patient records in 2023 were caused by hacking
Contemporaneously, the 2023 IBM Cost of a Data Breach Report noted that the healthcare industry recorded the most expensive data breaches at an average cost of $10.93 million. For HDOs, data breach costs increase exponentially because their lack of an incident response infrastructure means they need to spend money engaging in a post-attack forensic review to determine tactics and techniques by:
- Harvesting RAM
- Reviewing CED log
- Tracing network activity
The Complexity of IoMT Security Risk Management
HDOs manage systems engaging in complex tasks but often lack the complex infrastructure to support these operations. Additionally, the traditional solutions that enable them to manage business IT assets fail to respond to the unique risks that IoMT presents.
So Many Devices, So Many Vulnerabilities
The average HDO manages between 2.2 and 4 million medical devices. Further, the current reporting method for vulnerabilities, the Common Vulnerabilities and Exposure (CVE) list identifies tens of thousands of security issues across this medical device inventory. By the raw numbers, vulnerability and patch management become overwhelming.
Unique Lifecycles
While enterprise IT investments typically have a 3-5-year lifespan, medical devices persist for decades, especially since HDOs gain pure profit from their use every year past the depreciation threshold. The vulnerability reporting and risk metrics that enable enterprise IT security fail to respond to medical device lifecycles. For example, HDOs will continue to use medical devices running Windows XP until those technologies are no longer medically operationally capable. However, these twenty- or thirty-year-old devices were created before ipv6, meaning they never intended to respond to the evolving threats that connectivity created.
Large, Disconnected Group of Stakeholders
As HDOs incorporated new technologies, the number of individuals who help manage security expanded. At a high level, most HDOs have the following roles:
- CISO/ Information Security
- Compliance/ Privacy
- Supply Chain/ Vendor/ Manufacturer
- Information Technology
- Legal
- Healthcare Technology Management/ CE/ Biomed
- Corporate Communications/ Public Relations
- Emergency Management
- Clinical Risk Management
- Nursing/ Physician Leadership
In the organizational context, each stakeholder has job-related responsibilities often disconnected from security. However, each department touches upon security in an attack’s aftermath. Since their daily duties don’t overlap, they may not have clearly defined security incident responsibilities.
Where Current Security & Incident Response Tools Fail
The organization’s enterprise IT security team often has access to various monitoring tools and data feeds. Unfortunately, these resources fail to respond to the unique cybersecurity risks arising from threats targeting medical devices.
When reviewing the available resources, HDOs should understand what they are and why they may not be effective when applied to IoMT security. For example, some typical resources include:
- Common Vulnerability and Exposures (CVE) List: A list of known vulnerabilities that lack an understanding of the HDO environment’s context
- Common Vulnerability Scoring System (CVSS): Visibility into vulnerability’s impact on enterprise IT security but fail to reflect the clinical environment and potential patient safety impact
- Threat feeds: Visibility into attacker activity but focused on enterprise IT exploits with disparate information
- Endpoint detection and response: Agents for enterprise IT devices but unable to install on medical devices
- Vulnerability scanners: Identification of CVEs on enterprise IT devices but disrupt IoMT network connectivity
Network and IP scanners: Tracking network activity but fail to trigger packet capture during an attack to collect IoMT forensic data
Responding to Challenges: MITRE, MDS2s & SBOMs
Public and private sector organizations recognize HDOs’ challenges and look to reduce these burdens.
MITRE ATT&CK Framework
The MITRE ATT&CK outlines the tactics, techniques, and procedures (TTPs) that threat actors use during an attack across the following vectors:
- Adversarial: Threat Attackers and Hackers
- Tactics: The exploits they use
- Techniques: How they use those exploits
- Common Knowledge: Data and reports open to the public on adversary groups
Working with the US Food and Drug Administration (FDA), MITRE developed a risk rubric, now called the Medical Device Development Tool (MDDT). The MDDT enables analysts to incorporate CVSS scores into medical device risk.
Manufacturer Disclosure Statement for Medical Device Security (MDS2)
The MDS2 is a form that HDOs can request from IoMT manufacturers. These documents provide information about a device’s capabilities and internal configurations, including:
- How to patch them
- Whether patches can be applied remotely or not
- Whether operators can install patches themselves
- Whether devices store or transmit Protected Health Information (PHI)
- Measures that HDOs can take to protect PHI
- Whether devices have anti-malware or can have it installed
- Built-in security safeguards, like encryption, auto-logoff, malware detection, physical locks
The MDS2 enables HDOs to securely implement and deploy medical devices, often offering clinically sound vulnerability remediation suggestions.
Software Bill of Materials (SBOM)
An SBOM is lists all the software components within a given device, including:
- Drivers
- Licenses
- Operating systems
- Open-source code
SBOMs provide insight into the different technologies that the device incorporates, giving HDOs a way to track new vulnerabilities. For example, SBOMs would provide insight into whether devices run Apache 3.16, making it easier for the HDO to identify potential Log4J-based vulnerabilities and risks.
Threat Detection and Incident Response with Asimily
Your incident response plan (IRP) and incident response team (IRT) are critical when a security incident occurs. However, your IRP and IRT should be the last line of defense within a broader medical device security program.
To protect yourself from a data breach, you need a proactive plan that mitigates risks and detects threats arising from difficult-to-manage yet critical-to-patient-care IoMT.
Build a Team of Internal Stakeholders
With IoMT touching nearly all parts of your HDO, you need to identify key stakeholders and meet regularly so that everyone understands their role and responsibilities before an incident occurs.
For example, IRT includes representation from:
- Biomedical department
- Firewall team
- Vendors
- Network team
- Server team
With Asimily, you create a single source of information across these diverse team members, enabling collaboration and informed decision-making.
Identify Medical Devices
Identifying your HDO’s medical devices is the first step to understanding risk and building an incident response plan. Asimily’s passive scanning technology enables you to identify all devices connected to your networks without disrupting functionality or patient care.
Asimily identifies and classifies every connected device on your network down to the specific model, operating system, and software version. We define where they are on the network, what departments they are in, and track them as they move throughout your campus so you can build accurate device profiles that include the following for each device connected to their networks:
- Operating system
- IP address
- MAC address
- Port numbers
- Hostname
- Version number
Assess IoMT Risk
Every medical device will have a vulnerability, but attackers won’t be able to exploit every vulnerability. When assessing IoMT risk, you need visibility into how threat actors can use that vulnerability in their attack plans.
Asimily identifies where exploitable vulnerabilities are in your environment. We include device and manufacturer information using MDS2s and SBOMs for each specific device. We then prioritize vulnerabilities based on real-time exploitability, so you don’t have to sift through them manually and provide specific recommendations to mitigate the risk. Using Asimily, you can report on all known published vulnerabilities (CVEs) across your detected inventory.
Since Asimily’s Proactive provides visibility into all medical device data, an HDO can engage in due diligence before purchasing a device. For example, they might consider purchasing a Pyxis medical dispenser running the 1.4 firmware. HDOs can identify the deployment configuration to achieve the lowest Risk Score and which end-of-life (EoL) operating systems could potentially be upgraded to a supportable OS. With Asimily, HDOs can review different ways other HDOs had deployed the devices and the impact the deployments had on the risk scores. Using Aimily’s deployment guides, they secured their entire Pyxis fleet.
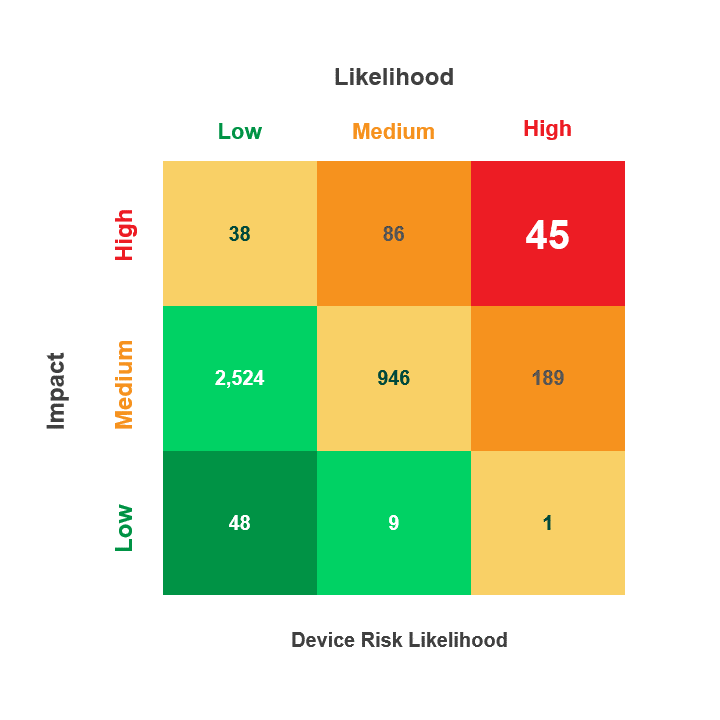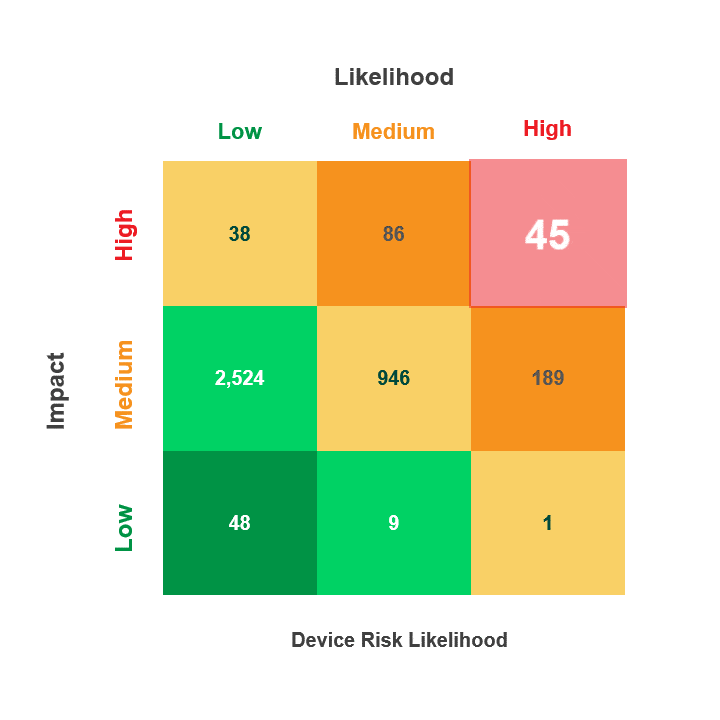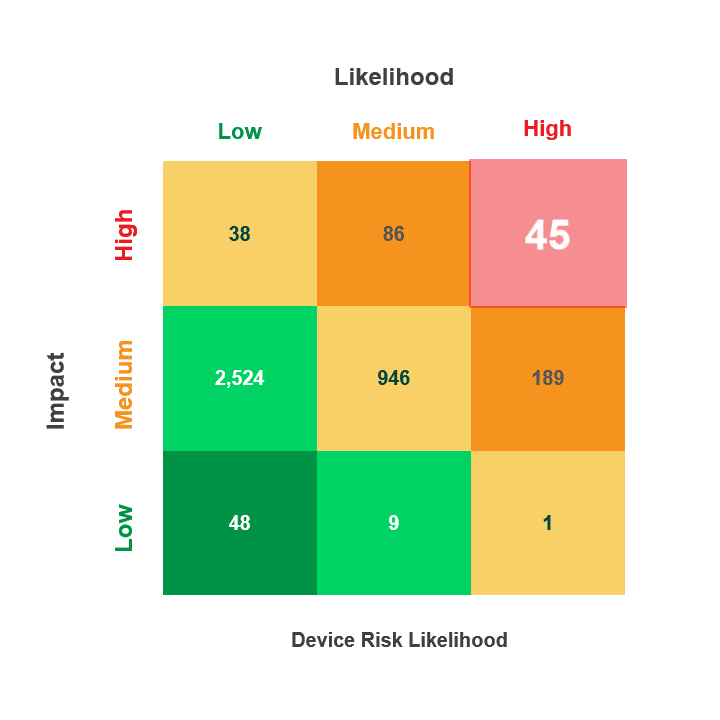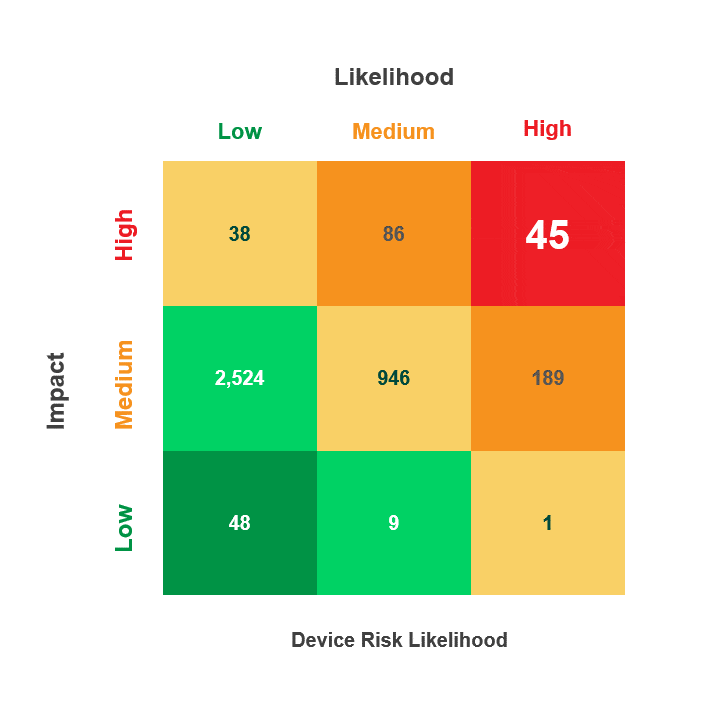
Prioritize Vulnerability Management Activities Across the Device Lifecycle
Most Healthcare institutions have thousands of IT, IoT, and IoMT devices that could have hundreds of thousands, if not millions, of CVEs impacting their inventory. By operationalizing the MITRE ATT&CK Framework, you can identify the CVEs that are actually exploitable within the context of your unique environment.
For example, a CVE may utilize the Remote Desktop Protocol (RDP) to exploit a specific device type, but if that device cannot respond to RDP, then threat actors can’t use it during an attack. With this information, you can prioritize other exploitable vulnerabilities, saving time while improving your security posture.
With Asimily, you can prioritize your remediation activities and address exploitable CVEs based on the measured risk a device poses if exploited by enabling you to:
- Filter the hundreds of thousands of CVEs associated with your inventory to just those that are exploitable on your network.
- Prioritize your efforts to address the real risks to your network and not just the published list of potential threats
- Utilize the CVEs criticality score along with the Common Vulnerability Scoring System (CVSS V. 3) and the Risk Rubric for CVSS to rate the exploitable CVEs based on their “Likelihood” to put the device at risk (Low, Medium, High)

Effectively Remediate Vulnerabilities Using Each Device’s MDS2, SBOM, and the MITRE ATT&CK Framework Data
By combining this data, you can focus on implementing the vendor-suggested, clinically valid remediation actions that align with how threat actors attack HDOs, including:
- Document remediation decisions to meet compliance and governance
- Mass edit all devices impacted by the same decision
- Review high-impact and high-likelihood devices with open CVEs
- Use clinically valid and vendor-approved recommendations to improve security
- Collaborate more effectively with clinical engineering and their vendors to identify and install OEM security patches in a timely manner
- Understand the technology architecture for visibility into what the devices connect to and integrate with
- Identify open ports and closed ports that are not in use
- Implement and enforce policies, like White Lists, that enable faster remediation
Continuously Monitor for Anomalous Behavior
By correlating threat intelligence with medical device activity, you can more rapidly identify anomalous behavior that might indicate a security incident. Your ability to detect threats reduces an attack’s impact because you can start investigating the incident faster. As attackers continue to target medical devices, you should have threat detection capabilities that enable you to stop an attack as soon as possible.
Asimily integrates with an HDO’s security incident and event management (SIEM) tool so that it can correlate data from various security technologies, such as:
- Threat feeds
- Endpoint detection and response
- Network monitoring tools
With our alerts, they gain visibility into changes that lead to device misconfigurations like:
- Factory Defaulted
- Missing HTTPS
- External DNS
- Expired Certificate or Obsolete SSL or TLS Version
- Wrong Network or VLAN
Gather Forensic Data
When an incident occurs, you need the technical forensic data that helps you quickly track down the attackers and appropriately report events to law enforcement.
With Asimily’s Packet Capture, you capture the syslogs, enabling analysis of what happened. For example, you would be able to correlate medical device network activity with:
- RAM information from servers
- Traffic information from network devices
- Data transferred to an FTP server
By capturing this data in real-time, you document attacker activity during the event. This enables you to:
- Limit the blast radius by preventing them from gaining additional access to resource
- Contain and expel them faster, reducing dwell time and impact
- Document activity across the kill chain
Report on Security Initiatives Across the IRT
Your security and incident response programs incorporate stakeholders with different amounts of technical knowledge. Your IT and security analysts need deep technical information like CVE numbers or IP addresses. Meanwhile, your senior leadership needs to understand security’s impact on business objectives and patient health.
For example, senior leadership needs to report security incidents to the board of directors and respond to auditor questions. By tracking trends, management can prove governance over security. Tracking risk trends and comparing security against peers enables your HDO to document your commitment to security and reduce potential fines by verifying compliance.
With Asimily’s Security Summary Report, leadership gains visibility into their medical device security program’s performance over time. Asimily’s Security Summary Reports provide at-a-glance visibility into:
- Device risk likelihood
- Device security compared to industry peers
- Vulnerabilities closed, including a focus on high-risk vulnerabilities
- Top anomaly categories

To learn more about Asimily’s robust threat detection, business continuity, and disaster recovery, download our Total Cost of Ownership Analysis on Connected Device Cybersecurity Risk whitepaper or contact us today.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




