Asimily’s Security Summary Report: Creating a Shared Language
As regulated industries go, healthcare has historically been one of the most highly-monitored ones. Falling within most governments’ definition of “critical infrastructure,” the industry is fundamental to protecting human life. Simultaneously, it manages vast amounts of sensitive data, often stored or accessed by medical devices that can be difficult to manage and secure. While health delivery organizations (HDOs) must comply with various laws and agency regulations, they often struggle to document and report on compliance activities in ways that enable executive leadership to engage in the meaningful oversight that they need to.
Data protection for Internet of Medical Things (IoMT) devices is highly technical. While health technology management (HTM) teams maintain these devices, IT and security teams work to mitigate their security risks. These activities require a deep understanding of device and network configurations. Meanwhile, proving governance means that business executives and boards of directors need insight into how these activities protect patient health and protected health information (PHI).
For executive leadership and the board of directors to make informed, risk-based decisions, HDOs need a solution that effectively communicates the business impact of technical activities.
What is governance?
Governance consists of the risk management oversight responsibilities that executive leadership and board of directors members must undertake to achieve compliance objectives. For HDO stakeholders to prove good governance, they need to measure their data protection program’s performance by analyzing whether policies and processes mitigate security risks effectively.
Health Insurance Portability and Accountability Act (HIPAA)
While HIPAA may not use the term “governance” specifically, it requires HDOs to prove accountability under the Security Rule, effectively creating a risk assessment and governance requirement. For example, under the Security Rule, HDOs must develop safety measures that consider:
- Size, complexity, and capabilities
- Technical, hardware, and software infrastructures
- Costs of security measures
- Likelihood and possible impact of risks to electronic PHI (ePHI)
Health Industry Cybersecurity Practices (HICP)
Incorporated into regulatory compliance requirements through Congressional vote, HICP Practice #10 outlines the basic cybersecurity oversight and governance requirements. HDOs of all sizes, must engage in cybersecurity risk assessments that document:
- Information system threats and vulnerabilities
- Potential impact and effectiveness of current safeguards and controls
- Likelihood that the threat or vulnerability could compromise data or information system assets
Since performing a risk assessment is an ongoing process, HDOs should engage in the following governance practices:
- Regular access reviews
- Periodical evaluations of security controls’ effectiveness
- Regular evaluations of threats and vulnerabilities to PHI
Key compliance and governance challenges with medical devices
Although HDOs recognize the need to prove governance over their data privacy and security programs, they face significant challenges arising from the proliferation of IoMT.
Highly Technical
Managing medical device security is primarily a technical initiative focused on software, hardware, and network configurations. Executive leaders and boards need information that enables them to make at-a-glance risk-informed decisions, not technical information that provides little context into how device security impacts patient health and data.
No one-size fits all
In security, every organization’s environment is unique. However, this becomes even more true when managing medical device risk and security. For example, many HDOs use compensating controls for End of Life (EoL)/End of Service (EoS) devices, like radiology equipment running Windows 7 operating system (OS). Traditional IT security technologies often fail to measure the security impact that these controls have.
Need visibility into program maturity
Executives and directors need to understand how their HTM, IT, and security teams’ activities help them protect patient health and data. These stakeholders need to make informed decisions to approve strategies and budgets. To discharge their responsibilities, they need visibility into and metrics for trends over time to gain insight into the program’s maturity.
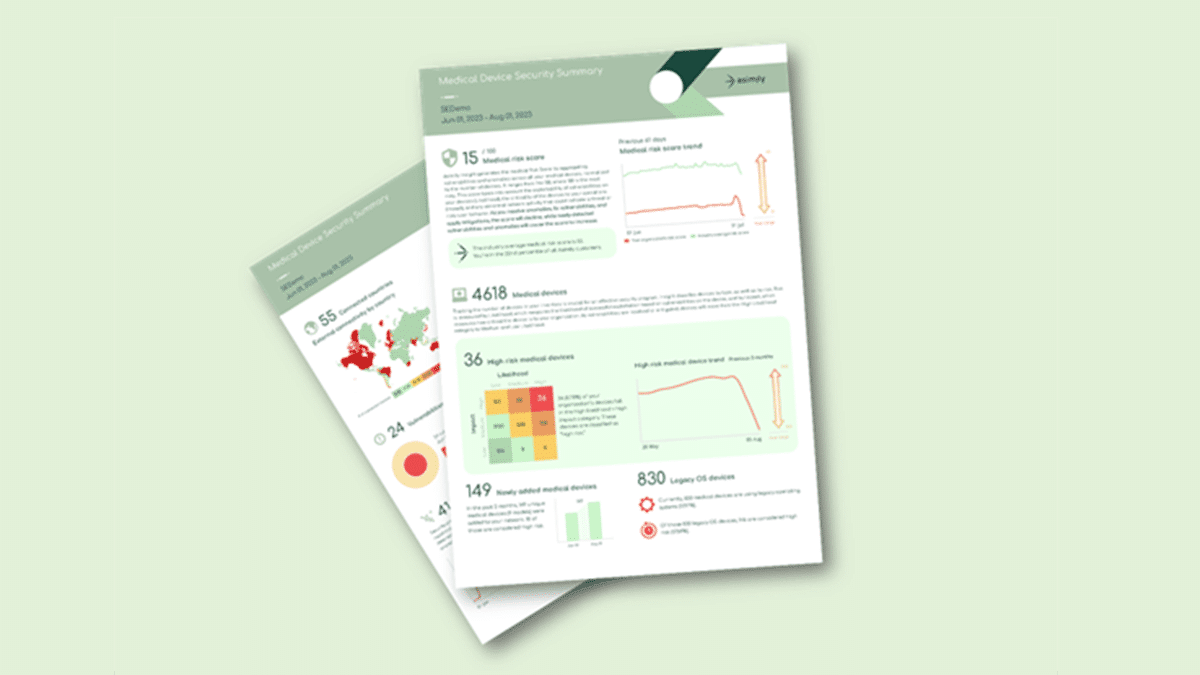
Asimily’s Security Summary Report
Executives and directors need compliance reports that empower them to monitor and understand their current medical device security posture more effectively to implement future strategies that protect patient health and data.
Regulatory agencies increasingly seek to hold C-suite members personally accountable for security incidents. In the last few years, various CISOs have been embroiled in Federal Trade Commission (FTC) enforcement actions, criminal obstruction proceedings, and Securities and Exchange Commission (SEC) enforcement actions. As federal agencies seek to hold CISOs accountable, future actions by the Department of Health and Human Services (HHS) are a definite possibility.
With Asimily’s Security Summary Report, HTM, IT, and security teams can collaborate efficiently to provide this visibility, establishing a common language across all security and privacy stakeholders.
Comply with risk assessment requirements
The cornerstone of any data protection program is the organization’s risk assessment. From a compliance perspective, HDOs must document their analyses as part of proving governance. From a business perspective, leadership needs to understand what risks it wants to mitigate, transfer, or decline.
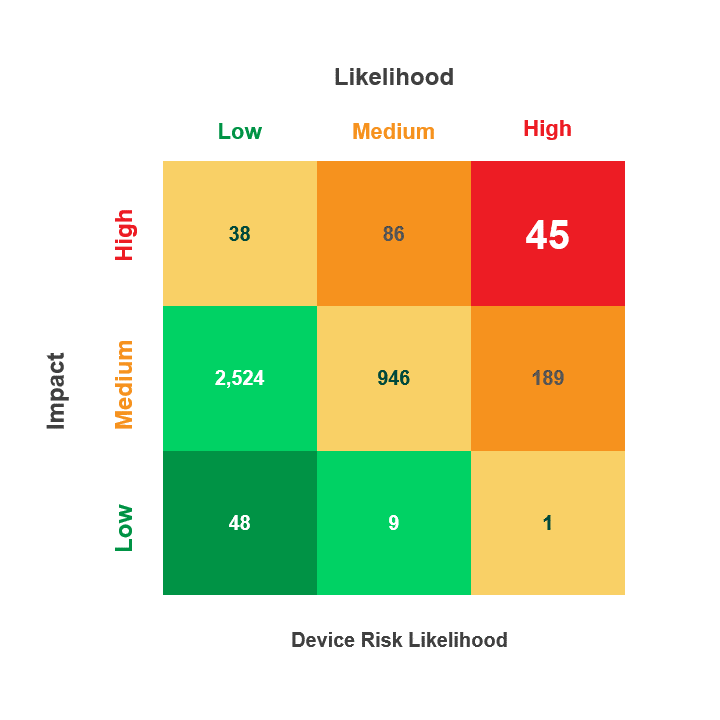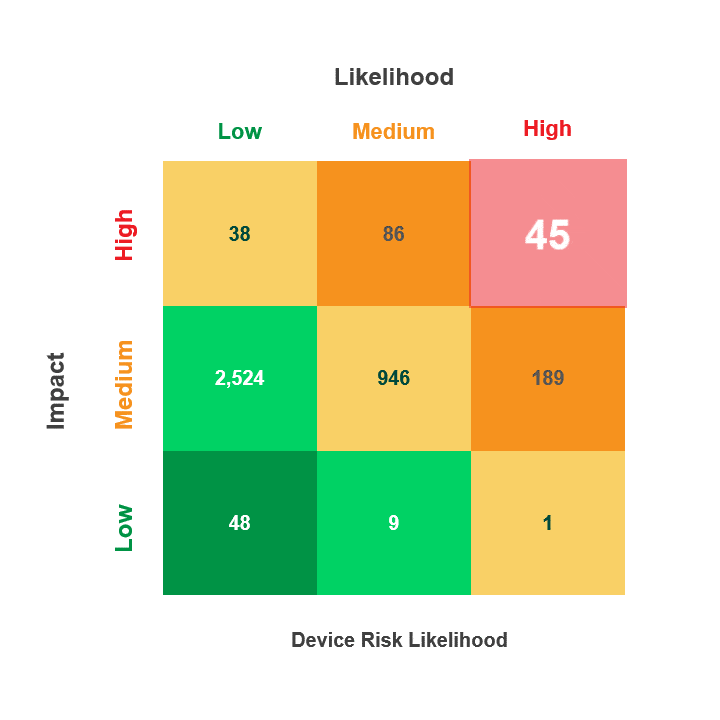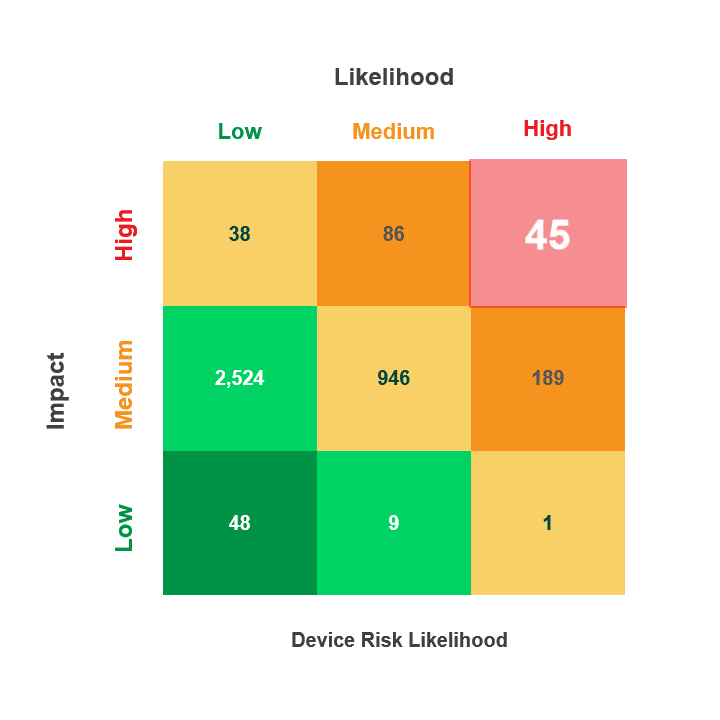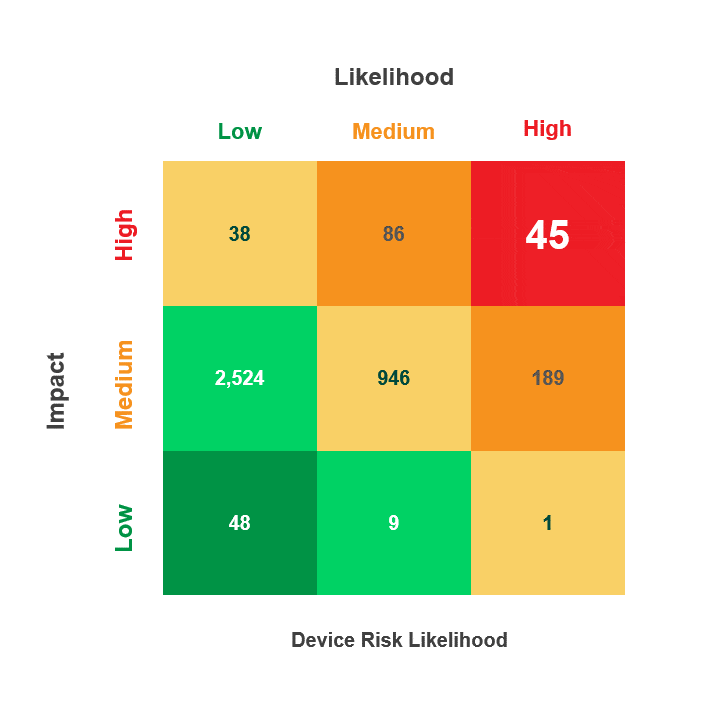
Risk is calculated by multiplying a security incident’s likelihood by its potential impact. When reviewing medical device security and privacy risks, HDOs need quick visibility into:
- Devices containing vulnerabilities
- Threat actors’ ability to use the devices in an attack
- The impact that an attack on those devices would have on patient health, data, or hospital operations
The Asimily Security Summary Report includes risk heatmaps that provide the visibility that executives and directors need so they can understand their current risk profile. With our security summaries, c-suites and boards can focus the questions they ask their CISOs on their highest-risk devices.
Meanwhile, CISOs have visibility into these risks and can prepare their answers. Together, business and security leadership can foster stronger relationships that enable them to build robust security and privacy programs.
Compare program to industry
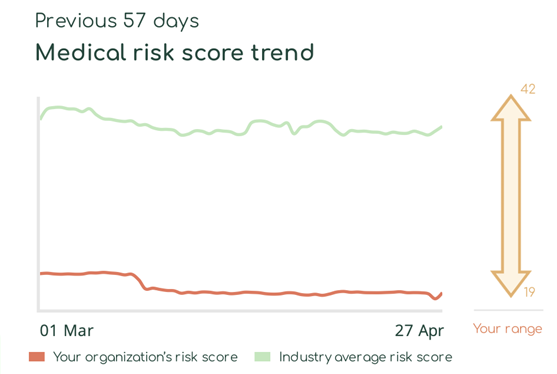
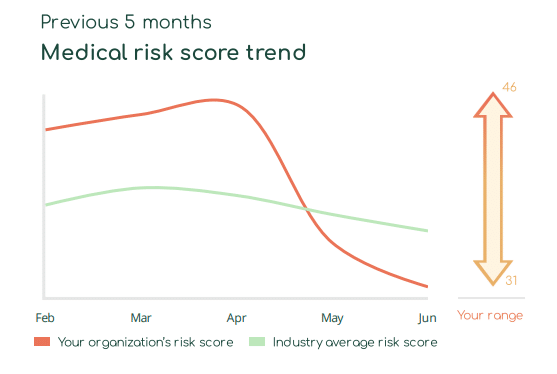
Annually, boards must compare their organization’s financials to peers. As HDOs integrate more technology into their patient care initiatives, comparing medical device security posture to industry peers becomes increasingly important. For senior executives and directors to understand their current risk posture, they must have the same visibility into medical device security that they have into financial stability.
With Asimily Security Summary Reports, HDO c-suites and directors gain at-a-glance visibility into how their medical device risk compares with industry peers. Using these reports, they can set benchmarks for their HDO’s security posture to measure their program’s overall effectiveness. Our Medical Risk Score Trend visualizes risk metrics over time, indicating that even with some ups and downs, they continually mature their programs. Further, they can use this visibility into medical device security as a competitive differentiator and a metric proving governance.
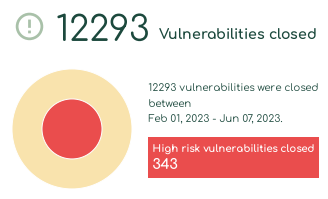
Report program success key performance indicators (KPIs)
Governance is an accountability process. HDO leadership must establish KPIs for proving the effectiveness of their data protection programs. As HDOs integrate more medical devices, they must incorporate metrics for securing these into their overarching KPIs.
With Asimily Security Summary Reports, c-suites and directors gain visibility into their medical device security programs. Our security summaries provide metrics that show medical device security improvement over time, enabling stakeholders to assess the impact that their security investments have on their overarching data protection and compliance posture. Using these metrics, they can prove that their current investments provided value and identify areas where they need to allocate additional financial and staffing resources.
Allocate resources more effectively and efficiently
With razor-thin operating margins, c-suites must allocate financial and human resources as precisely as possible. High-level risk data and trends give them visibility into their data protection program’s overarching success. However, their future investments must be done purposefully, so they need to understand where they should focus.
Asimily Security Summary Reports translate complex technical language for business-level discussions. For example, we take technical risks and create device-based categories that highlight areas requiring additional attention.

Similarly, we translate the types of anomalous behavior indicating potential security and privacy risks into categories that make sense to non-technical end users. With these reports, CISOs can communicate their needs more effectively with their leadership and directors.
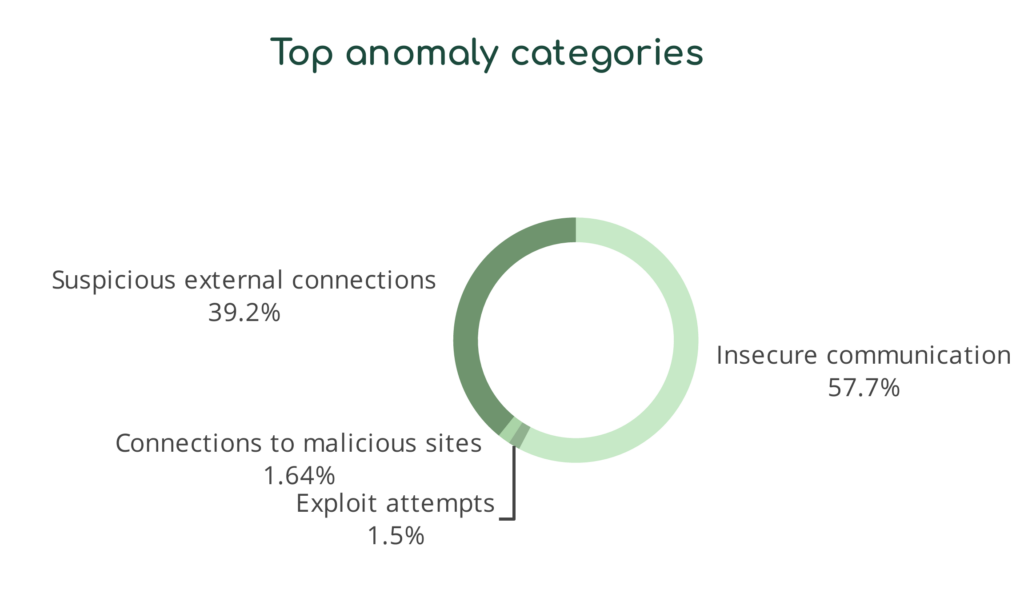
Communication is Critical to Compliance
Compliance – and especially governance – is a team sport. Technical and business stakeholders must have a shared language across all security initiatives so that they can work from the same understanding of risk.
To learn more about the Asimily risk remediation platform, visit our website or contact us today.
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




