Introducing Asimily Risk Simulations
The healthcare industry is today the number one target for cyberattacks. This alarming trend came to the fore in 2021 and worsened in 2022. Ransomware—when attackers hold the victim’s data hostage and demand money—is the latest big threat; furthermore, phishing and other attacks continue to endanger healthcare delivery organizations (HDOs). Risks are everywhere—is your current security posture up to the challenge?
Asimily Risk Simulations specializes in prioritizing risks and protecting what matters. Unique solutions for internet of medical things (IoMT) devices are able to support HDOs in responding to the current crisis. Besides strengthening your security, this technology improves asset utilization and saves you money.
Medical providers are at risk due to constrained security budgets and sensitivity to any downtime. An attack can have life-or-death consequences. In addition, security failures can potentially give rise to regulatory fines, lawsuits, and lost customers. Costs can reach millions of dollars—and any data loss will interfere with operational effectiveness.
Technology has brought remarkable benefits to the healthcare industry. However, while IoT medical devices bring better care, they also expose patients and providers to a greater likelihood of attack. These threats make healthcare cybersecurity more important than ever.
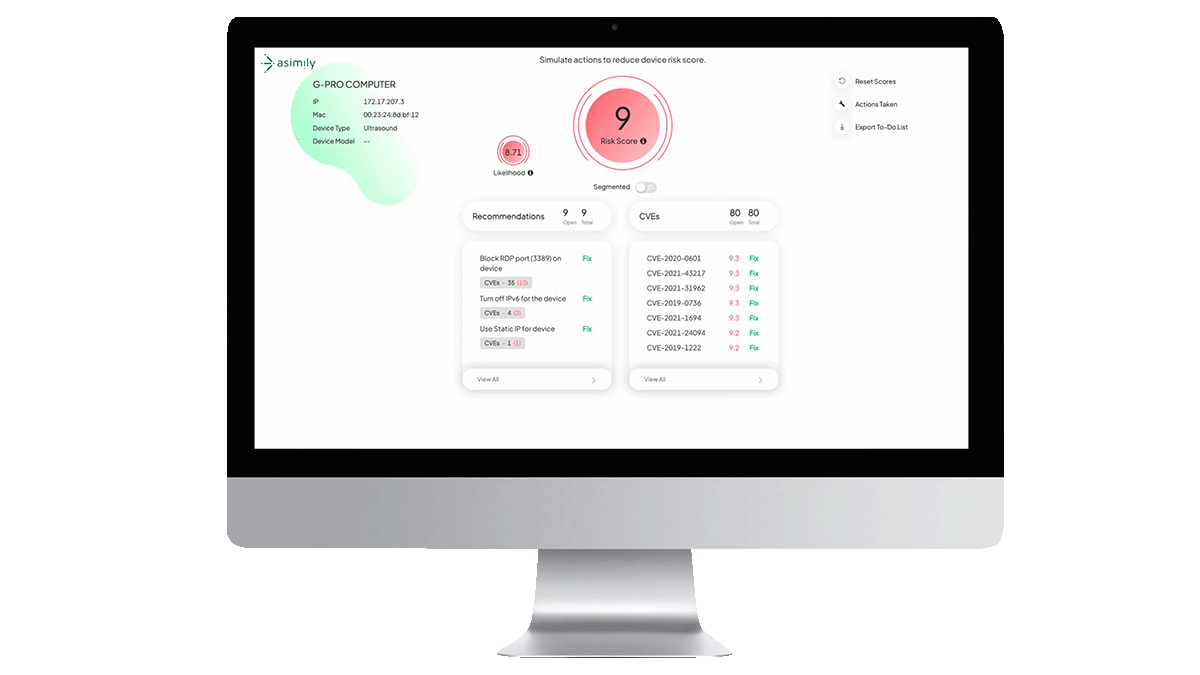
Fortunately, there are new healthcare security tools to respond to these challenges: for instance, Asimily’s risk simulations. These tools will help you identify risks, take the appropriate actions to secure your assets, and toughen up your IoT security posture overall.
Asimily specializes in prioritizing risks and protecting what matters. Unique solutions for internet of Medical Things (IoMT) devices are able to support HDOs in responding to the current crisis. Besides strengthening your security, this technology improves asset utilization and saves you money.
What Makes a Strong IoMT Security Posture
A security posture is the broad ability of an organization to defend itself against cyber threats. This includes the ability to foresee and forestall attacks—as well as to recover after an incident. When it comes to a strong IoMT security posture, this refers more specifically to a proven ability to protect connected medical devices.
The right infrastructure and policies contribute to a strong IoMT security posture. As with data, the network and devices on the net need to be well protected. Along with the appropriate technology, testing, and training also enhance your security. For medical devices, it’s important to use tools made specifically for these devices—for example, Asimily’s Insight rather than a general-purpose tool.
Security must adapt dynamically to the evolving threat landscape. IoMT devices remain relatively new and the methods of targeting them are changing rapidly. Isolated tools and processes are thus giving way to comprehensive security programs that stay ahead of the latest angle of attack.
When an HDO has a strong security posture, it’s able to successfully detect and block attacks. This includes high-risk IoMT devices that are particularly vulnerable to exploitation. Access controls and logging ensure that problems are traceable. Moreover, the network itself is defended by a firewall, and employees understand and adhere to safe practices.
Patching is important to maintain a good IoMT security posture. That said, patching on its own isn’t the whole story. You should also segment intelligently, mitigate risks, and learn about device vendors and products. Asimily Insight helps HDOs accomplish these goals.
Assessing and Improving Security Posture for IoT and IoMT
A security posture is never static; it can always be analyzed and improved. Here, risk simulations are a key element in upgrading your IoMT security posture. It’s also crucial to create a framework outlining your security objectives—and to measure data on issues detected and resolved.
Risk simulations from Asimily Insight work to assess the degree of vulnerability in your medical devices. That’s critical information when you’re deciding how best to support your security posture. For instance, you may find that certain devices or access controls are inadequate.
Once you’ve identified your risk profile through running simulations, the next step is to prioritize these risks. Not all IoMT weaknesses are equally probable—nor would each have the same impact. As such, it’s wise to focus on the risks that could potentially disrupt business operations or compromise patient outcomes.
Automatic IoMT security tools like Insight cut the average time to find and fix problems. They tighten your security posture to keep attackers out. Further, it’s easy to view the total risk profile of your network, as well as security information specific to your medical devices. These features complement risk simulations to boost the security of your devices.
Improving IoMT Security Posture Through Risk Simulations
Risk simulations are a valuable tool in any HDO’s cybersecurity strategy. Asimily produces leading-edge risk simulation software that evaluates the threats facing medical devices by analyzing likely attack paths. These simulations are already helping many healthcare institutions to improve their security—and they can help yours too.
Increase your uptime and lower your costs with a solution built with IoMT in mind. Our complete risk remediation platform goes beyond simulations to include features for inventory, forensic analysis, and device tracking, among many other functions. It’s the security tool specifically designed for healthcare organizations—and it’s currently protecting over 20 million devices at 2,000 sites.
Threats against HDOs may be on the rise—but you don’t have to be the next victim. Consolidate your security posture against malware, ransomware, and other risks. Contact Asimily now to secure your defenses.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




