Identifying and Monitoring Security KPIs for Healthcare

As HDOs build and mature the security programs that protect digital transformation strategies and improve patient care, they should identify and monitor IT and security KPIs.
Data breach costs across the healthcare industry continue to increase. According to the 2023 Cost of a Data Breach report, healthcare continues to experience the highest data breach costs across all sectors, and those costs increase year over year. In 2023, the average healthcare data breach cost rose from $10.10 million in 2022 to $10.93 million in 2023, an 8.2% year-over-year increase. Even more troubling, the report found that the average cost of a healthcare data breach increased by 53.3% over the last three years.
Meanwhile, healthcare delivery organizations (HDOs) work with razor-thin operating margins of 0.4% on average in 2023. With little financial room for error and consistently rising data breach costs, many HDOs have placed additional focus on their cybersecurity and privacy programs to ensure continued financial stability and business operations. As they continue adding more Internet of Medical Things (IoMT) devices to their environments, their data breach risk mitigation strategies must also secure these devices. Unfortunately, securing these devices comes with problems, including outdated technologies and confusion over the department responsible for it.
What are Healthcare Security KPIs?
Cyber security KPIs measure and evaluate the effectiveness of an organization’s security controls, including policies and processes. By tracking specific metrics and risk indicators, HDOs can identify gaps in their security program to make informed decisions around:
- Budgeting
- Staffing
- Technology investments
Security teams can proactively respond to the changing threat landscape by fine-tuning systems and controls by monitoring and reviewing the security KPIs.
Vulnerability KPIs
Vulnerabilities are a fact of life for any organization using software. They are discovered regularly, forcing organizations to address them via patches, remediation, compensating control or other protections. Patching is rarely available for IoT and IoMT, leading to an emphasis on other means.
Some examples of Vulnerability KPIs include:
- Patching cadence: time between publication of vulnerability and applying the security patch to the operating system, software, or firmware.
- MTTR (Mean Time to Remediate): the time it takes from when a vulnerability is confirmed to when it is secured. Often, these vary based on the severity of the vulnerability – Critical, High, Medium, Low, Informational).
- Number of Vulnerabilities Discovered: number of known vulnerabilities on devices connected to networks that attackers can exploit and still need to be patched or have compensating controls implemented.
Security Incident KPIs
Although everyone would like zero security incidents, you should remember that not every incident is a data breach. With these metrics, you gain insight into trends to help understand where you may need to incorporate additional technologies or monitoring.
Some examples of security incident metrics include:
- Attempted intrusions: number of times threat actors attempt to gain unauthorized access.
- Number of security incidents: number of true alerts that required the security team to take additional action.
- Mean Time to Detect (MTTD): average time to detect a security incident once it occurs.
- Unidentified devices on internal networks: potential malicious devices with unauthorized access to networks used for sensitive data storage, transmission, and processing.
- Access management: number of accounts with excess access discovered during regular reviews.
Security Response KPIs
To measure the organization’s incident response and cyber resilience, HDOs can use the following metrics:
- Mean Time to Investigate (MTTI): average time from alert until the incident’s root cause is determined.
- Mean Time To Contain (MTTC): average time from alert until the threat actor is contained.
- Mean Time to Recover (MTTR): average time from alert until all impacted systems are restored to their pre-attack state.
- Dwell time: length of time that a threat actor remained in systems.
Business Performance KPIs
Digital transformation means that the HDO’s cybersecurity posture impacts its business performance.
When incorporating security and privacy into business performance, some security KPIs include:
- Overall risk score: the likelihood that an attack will lead to service downtime or cost money.
- Comparison to peers: organization’s security posture compared to other similarly situated HDOs based on things like region or number of beds.
- Business disruption: time spent without access to devices, networks, or applications that leads to impaired patient care and lost revenue.
- Overall risk score: the likelihood that an attack will lead to service downtime or cost money.
- Compliance violations/fines: non-compliance with regulations like the Health Insurance Portability and Accountability Act (HIPAA).
Why HDOs struggle with IoMT security KPIs?
IoMT devices pose unique security and patient health risks. The devices often lack the same inherent security controls as traditional workstations, meaning their proliferation across an HDO’s environment dramatically expands the attack surface. Alternatively, taking devices offline while responding to an incident or scanning a network undermines patient care.
As HDOs work to secure these critical yet sensitive technologies, they face various challenges.
Lack of Clearly Identified Responsible Party
Historically, healthcare technology management (HTM) and clinical engineering teams managed medical devices, ensuring continued performance rather than security. Meanwhile, IT and security teams focused on data protection controls. With IoMT, medical devices connect to networks, requiring both performance and security oversight. Many HDOs still need to identify a responsible party, leaving HTM, IT, and security teams confused over who should manage and monitor security updates.
No Single Source of IoMT Information
HTM teams record their devices’ information in a Computerized Maintenance Management System (CMMS), while IT and security teams use the Configuration Management Database (CMDB). Although the two inventory systems have some overlaps, they also leave security configuration data disconnected from other information about the devices, such as physical location on campus. Without a single source of holistic IoMT information, HTM, IT, and security teams struggle to gain visibility into their security posture.
Complex, Dynamic Networks
Medical devices are sensitive to changes in network traffic, causing them to fail. High-traffic networks can lead to a service outage, but traditional active vulnerability scanners that detect security weaknesses can also cause IoMT to fail.
Interrupting Patient Care
Unlike knocking a laptop offline, an IoMT device that fails to remain connected to the network can undermine patient care. For example, some IoMT, like ventilators, must remain online because patient lives depend on them. In other cases, IoMT service availability can delay a patient’s Care, like with robots used during surgeries.
End of life (EoL)/End of service (EoS)
Many medical devices have a long lifespan. For example, CT scans and MRI machines typically last for ten to fifteen years because they are expensive. However, over time, these devices have become connected to the internet. Meanwhile, many run on outdated, EoL/EoS operating systems, meaning manufacturers no longer supply security updates. Without these, HDOs need to implement clinically validated compensating security controls to keep clinically useful devices available.
Incorporating IoMT into IT and Security KPIs with Asimily
With Asimily, HDOs get a technology that solves the IoMT visibility and sensitivity issues, making securing these devices challenging. Designed purposefully to overcome the challenges that unique environments and device configurations create, Asimily enables HDOs to identify and integrate IoMT cybersecurity KPIs into their overarching data protection and business objectives.
Develop Baseline Risk Security KPIs
With Asimily, HDO can identify and inventory all medical, laboratory, and IoMT devices, including their relationships. With this information, they can build an asset inventory that combines IT and HTM data, enabling them to document:
- All IoMT devices connected to their networks
- Manufacturer
- Device type
- IP addresses
- Applications on devices
- Operating systems and versions
- Software versions
With this data, HTM, IT, and security teams can harden devices or work from a shared understanding of the clinically validated compensating controls.
Assess Organizational Risk
An organization’s overall security risk score incorporates various components:
- Device risk: the number and types of devices that have active vulnerabilities and would have a high impact on the HDO if they were compromised.
- Network anomalies: any malicious or suspicious activity detected on the network.
- Number of vulnerabilities remediated: both the total number and the number of high-risk vulnerabilities fixed during a given period.
- Peer comparison: long- and short-term trends that measure the HDO’s security program effectiveness to other similar HDOs.
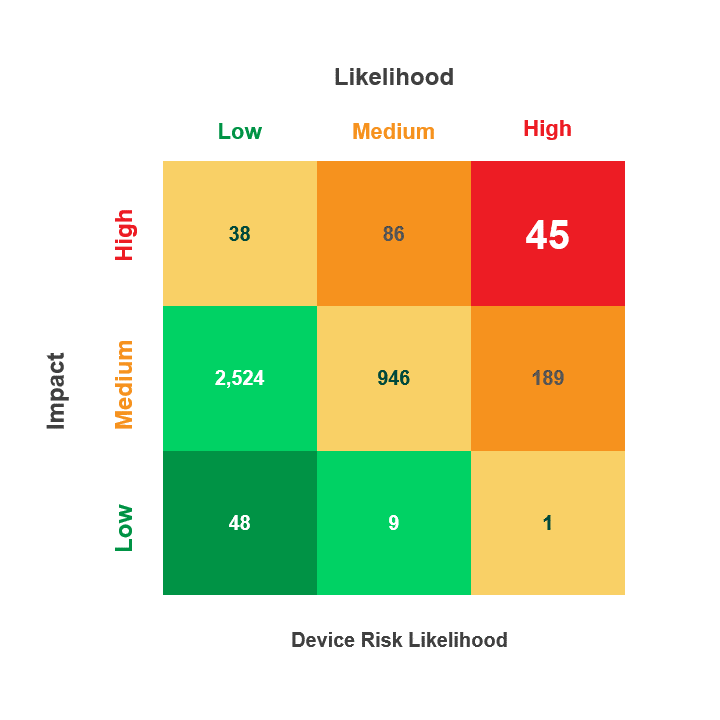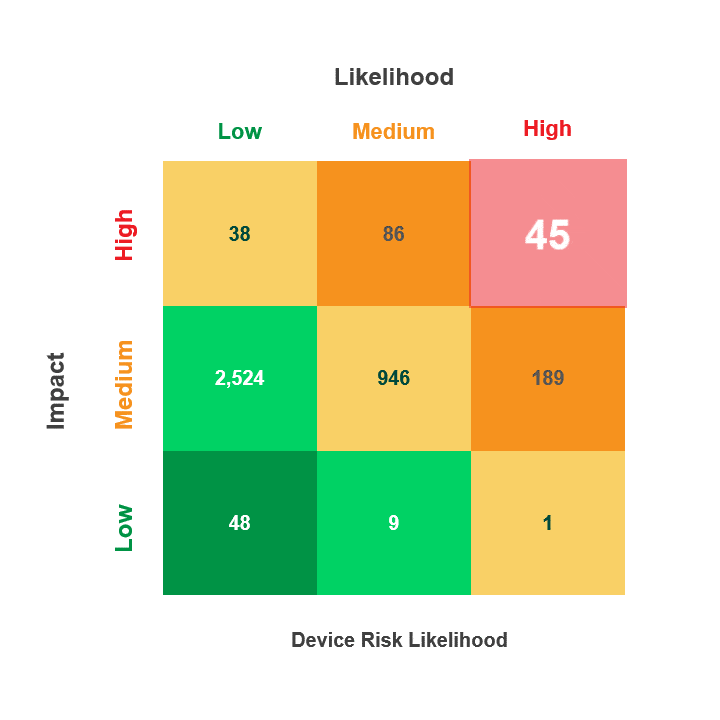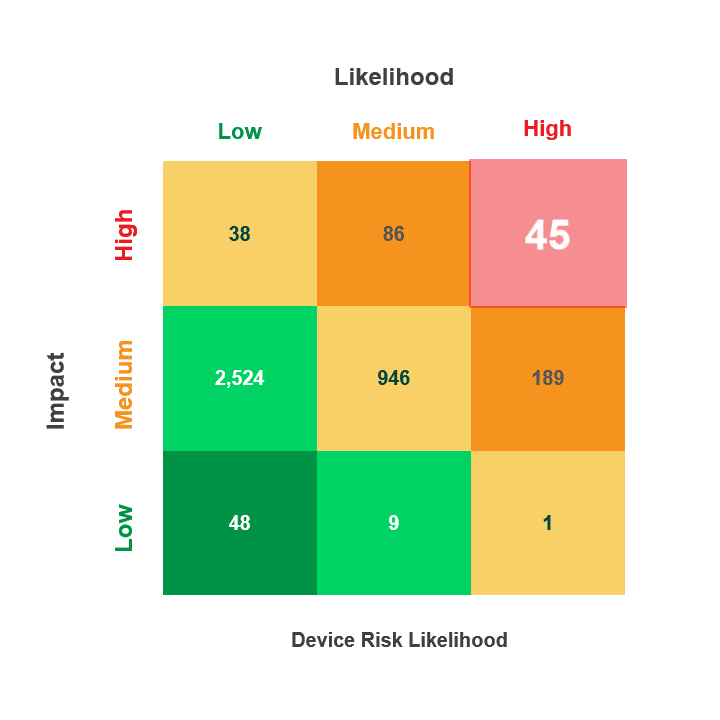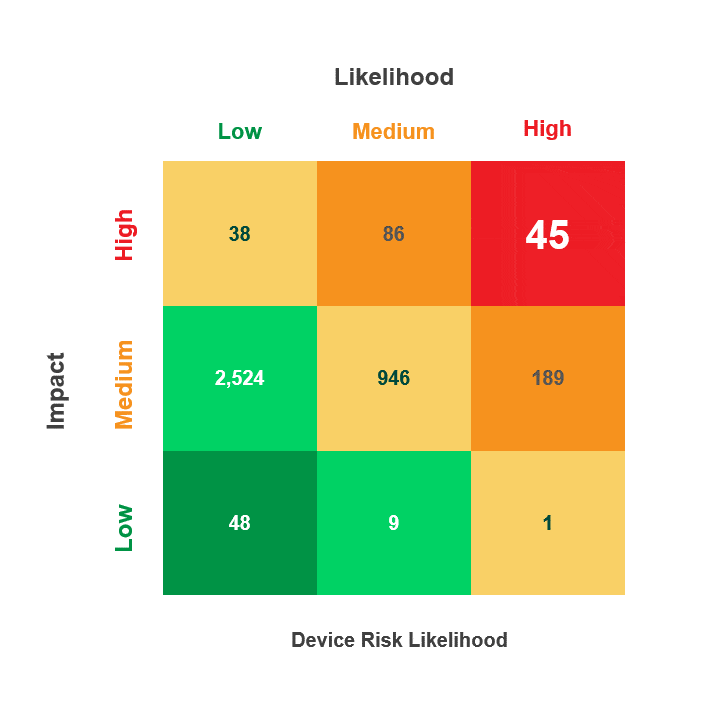
When tracked over time, a single score that represents organizational risk can be helpful. While it appears simplistic, an organization risk score that uses a scale(1-10 and 1-100 are common) is easy to digest and share. Scores need not be organization-wide; they can also address subsets like medical devices or departments. Showing that the score is heading in the right direction can help galvanize support and marshal resources for improved cybersecurity.
Asimily’s Security Summary Reports provide this information in easy-to-understand ways so that technical and executive stakeholders understand the HDO’s current security and risk posture. With our quantitative data, HDOs can use their risk score to determine whether their security posture achieves – or better yet exceeds – objectives.
Manage IoMT vulnerabilities
Asimily’s passive vulnerability scanner enables HDOs to scan IoMT safely without changing the device’s configurations or readings while patients use them. Further, IT and security teams can integrate these scans with their active scanning tools for a comprehensive, layered security approach.
With Asimily’s deep, contextual engine, HTM and security teams can work together to prioritize vulnerabilities by aggregating and analyzing:
- Manufacturer-supplied security data
- Open-source software components
- Vulnerability criticality
- Current attack methods using the vulnerability

By taking the environment’s needs into account, Asimily provides simple, short, and effective recommendations that identify activities like:
- Deactivating unnecessary services without impacting clinical function.
- Blocking risky services with a Network Access Control (NAC) tool.
- Hardening vulnerable devices by updating their configurations.
- Implementing micro-segmenting when altering configurations affects the clinical function.
Improve Incident Response KPIs
Security teams can detect, investigate, contain, and eradicate malicious actors more rapidly by incorporating IoMT into their incident response processes. Asimily’s security and monitoring solution enables HDOs to detect anomalous activity indicating a potential security incident. With Asimily, security teams can set up alerts for specific incidents and tailor policies to their unique networks and IoMT device environments. Further, our packet capture and forensic analysis capabilities enable security teams to collect, review, and preserve the appropriate forensic evidence.
Align to Frameworks for Compliance
As HDOs improve their security posture, they should document all processes to achieve compliance goals. With Asimily, HDOs can align their medical device security activities to the Health Industry Cybersecurity Practices (HICP) Practice #9 by using these security KPIs suggested by the 405(d) Task Group:
- Number of medical devices that do not conform to basic endpoint protection cybersecurity practices measured weekly.
- Number of medical devices not currently segmented on wireless or wired networks measured monthly.
- Number of unmitigated high-risk vulnerabilities on network-connected medical devices measured monthly.
- Number of devices that have unknown risks due to lack of manufacturer-disclosed information, measured monthly.
- Number of medication devices procured that did not receive security evaluation, measured monthly.
To learn more about how Asimily can help you establish and monitor security KPIs, download our Total Cost of Ownership Analysis on Connected Device Cybersecurity Risk whitepaper or contact us today.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




