The Essential Forensic Analysis Guide for IoMT Cyber Security

Author: Priyanka Upendra, Sr. Director of Customer Success, Asimily
Problems have a tendency to repeat themselves when gone unaddressed. This is why forensic analysis is so essential to running a tight ship. Healthcare delivery organizations (HDOs) conduct forensic analysis to understand what sorts of suspicious events they’re working against or have faced already. The problems are difficult enough in any case, but have an added salience for internet of medical things (IoMT) devices.
Forensic analysis helps information security officers reevaluate the effectiveness of security monitoring tools and the weak points in infrastructure. For example, medical devices and building management systems (BMS) often expose an organization to threats. However, any sort of asset connected to the network can pose some risks.
Computer crimes have grown in number and severity, with HDOs the worst hit. Forensic analysis is a key step in assembling evidence after a cyberattack; this assists organizations in preventing future incidents and protecting data—as well as helping law enforcement pursue the offenders.
Forensic analysis includes any actions you might take to collect, examine, and report on data. Time is of the essence since attackers can escalate or withdraw quickly. Asimily’s Distributed Sniffer offers immediate network information, making it a highly valuable aid.
Taking the right steps operationally in conjunction with a sound policy and the right tools will prepare you for a solid defense. IoMT devices may be vulnerable to attackers—but you can monitor proactively and conduct analysis after anomalies to protect your healthcare delivery organization.
What is Forensic Analysis for IoMT?
Forensic analysis for the Internet of Medical Things is the retrospective analysis of incidents that have already happened. You’re trying to use evidence to piece together more of the details of the event.
To start, it’s critical to determine how an attacker got into the network. Did they exploit a vulnerable system, or have an accomplice within the organization? It’s also important to learn which tactics they employed to spread within the network.
To gain a better understanding of the attacker, you’ll want to identify the motivation behind the attack. Is it an attempt to extort money? To cause destruction? And if relevant and possible, forensic analysis may ask to attribute the attack to a specific entity.
The process is analytics-driven in that it relies on raw data sets. This supports efforts to understand what happened and discover what techniques malicious actors may have used in the process.
Note that forensic analysis is generally separate from detection because forensic work takes place after the incident—often even after the response. Detection should happen as soon as possible, but you can only conduct forensic analysis after the dust has settled.
You can use the resultant information to reassess risk management activities. You may want to restructure or reinforce healthcare cybersecurity measures; as such, forensic analysis is part of a comprehensive approach to vulnerability management. It helps in covering your IoMT devices and the entire network against risks.
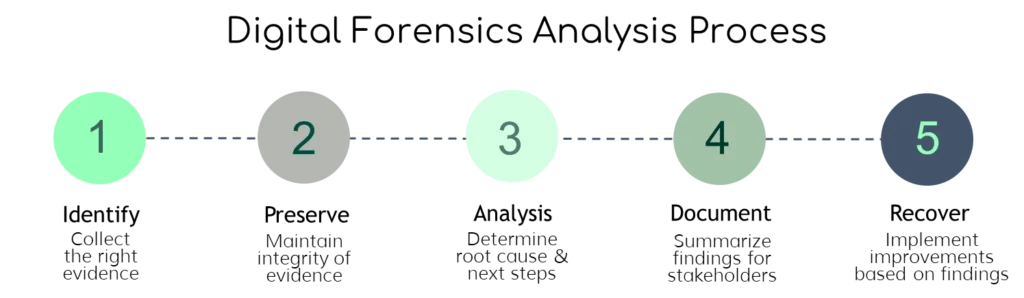
We can divide forensic analysis into multiple stages, including investigating cyberattacks after the event and developing post-incident reports and actions. Each stage has its own steps that combine to help you react to an attack—and prevent the next one from occurring.
Investigating Cyber Attacks Post-Incident
After a healthcare security incident, you need to investigate the situation. This starts with data gathering and policy considerations. Then you can conduct a formal investigation of the incident. Asimily’s Distributed Sniffer helps you uncover the problem right in the heat of battle.
IoMT security is too complex to eliminate all threats. Therefore, it is necessary to focus on preventing the most critical problems, then responding effectively to the rest. Incident response should produce a cleaner network that is more resilient to attacks.
Data Gathering and Policy Considerations
When a problem occurs with IoT medical devices, it’s important to collect data about the incident and report it within IT right away. This also goes for malfunctions and any suspicious or unexpected behaviors—not just outright breaches.
But it’s in the wake of the crisis that forensics becomes critical. The risk of exposing protected health information makes it especially important for HDOs to have this capacity.
Assign the right staff and external partners to each component of forensics. For example, you may have IT personnel responsible for managing data analysis and also work with third-party software providers and medical device manufacturers.
The team assigned specifically to incident response should have multiple people with forensics abilities. You can use exercises and new technology demonstrations to maintain the relevant skills. Additionally, you should have more general teams that can contribute to forensics, including HR, legal, and physical security.
Policies need to support your efforts to investigate attacks. The incident response team should have authorization to conduct network investigations under relevant conditions. Familiarize personnel with your forensic policies so that they’re ready when any incident occurs.
These policies should also clearly establish each person’s duties, both internally and externally. You should also outline what actions to take ordinarily and in case of an attack, and which tools to use. Forensic policies work in tandem with your wider policies and practices to ensure a reliable response to any malfeasance.
There are numerous sources for data collection—servers, mobile devices, and the IoMT devices themselves. You can also use network monitoring data and application logs. Data gathering has some added complexity when using the cloud (rather than on-premises resources) due to the service provider holding data spread over various locations.
Steps for Data Collection
Automating your data collection is essential to prepare for any incident. Asimily automatically tracks infusion pumps, MRIs, linacs and other IoMT devices, revealing the time and place they were last connected. Moreover, Asimily monitors all traffic to and from a device, simplifying forensic analysis.
Several precautions can help ensure data validity in case it’s needed for legal or disciplinary reasons. For example, you should generally make a copy of data and only run analyses on the copy, not the original. You can also use checksums and control who has physical access to the data. Document the steps you take during data collection, including information on the tools you use.
In post-incident forensics, it can be necessary to disconnect devices from the network to protect systems and evidence. Bear in mind how device isolation—and any other steps you take—may impact the organization’s regular activities. You may also want to list all the people who have access to an affected device, as they may have useful knowledge.
Prepare any material you’ll need for data collection in advance, such as backup storage and chain of custody forms. In the event that you have to deal with law enforcement, they may be involved in acquiring evidence, and retain your storage hardware for extended periods.
Before starting a formal investigation, ensure you have enough data to proceed. If not, work with stakeholders to resolve the lack of information. Your hardware and software for data collection should already be installed and configured.
As an example, suppose that an electroencephalogram (EEG) device shows abnormal behavior. You may have noticed unusual network traffic to and from the device. Your IT team can investigate the location and functionality of the EEG device.
The sooner you have this information, the better. If you’re using Asimily you’ll already know when and where the device last went online, vendor- and device-specific data, and more information useful to the investigation.
Starting the Formal Investigation of the Incident
A security violation triggers a formal investigation. Your forensic analysis aims to uncover the cause of the incident and enable steps to recover. The investigation starts out with a specific point—for instance, an affected device or a compromised account or person.
On the basis of what you find at that starting point, you can then discover additional targets to investigate. By the time you detect an intrusion, it’s quite unlikely that you found the first entry into the system, unless you have strong evidence that it’s the first entry.
Ideally this breadth-first search will help you discover all the places that were impacted or compromised. This will help determine how the attacker penetrated in the first place—and how you can fix the problem. For example, you may find that an employee clicked a link in a malicious email. You might then conduct a refresher course on employee cybersecurity training and ensure tighter access controls.
Assess the Attack
With physical IoMT devices, HDOs are completely reliant on the manufacturer and their internal network teams. When it comes to the internal network, often there isn’t device-specific information other than what’s happening on the HDO’s network. This makes HDO security more difficult than general network security.
The formal investigation process is not a straight line. Rather, it’s like analyzing points on a graph and trying to figure out which were touched by the attacker. Incident responders usually think about this in a “branching graph” way and do a broad search to try and understand where the vulnerable points are.
Ideally you can discover which points or nodes are the “root” of the infection—the source from which the attack spread. Typically you don’t start off knowing where the attacker’s point of entry is, but that’s a purpose of forensic analysis: to determine the initial point of entry where the attacker got into the network.
Identifying this initial point of entry contributes to understanding the root cause of the issue and why the attack happened in the first place. Your job is to figure out where the attack started and how far it reached.
Systematically examine as much relevant data as you can extract from the affected devices. You can later filter out information that doesn’t pertain to the suspicious behavior or attack. Narrow down data to parts connected with the investigation—for instance the time around the event or IP addresses associated with the event. Then bring together details from all components—devices and network traffic—to make your understanding as complete as possible.
Essential Forensic Analysis Tool: Asimily’s Distributed Sniffer
Asimily’s Distributed Sniffer is a unique tool to facilitate and accelerate the investigation process. It helps with data collection and analysis by capturing raw network traffic, either on command or automatically in response to suspicious activity.
Most HDOs lack the ability to capture suspicious network traffic in an automatic fashion. As such, they have to install another system on the network physically—which is expensive and time-consuming. You can’t afford to waste time and money during an attack!
You’re better off with the defense provided by a tool expressly designed for that exact purpose. Asimily’s holistic security solution has a forensic analysis module to assist your investigations into malicious activity. It isolates the source of problems to give you a better understanding of how to respond.
With the Distributed Sniffer, HDOs can set policy-based triggers that automatically capture raw packets of data about any suspicious activities in your network. You can define these policies on what counts as an attack, an exploit, or other malicious activities and program them as triggers to immediately record any information on what the attacker is doing in real-time.
When the Distributed Sniffer detects an incident, it offers several useful outputs. A topology report shows you the network connections of the IoMT device, so you can easily track the potential paths of an attacker. A flow analysis tells you which network protocols the devices use to connect with other systems, which can signal the perpetrator’s methods.
Since medical devices often don’t produce detailed and easy-to-use logs, collecting data is more than half the battle. Asimily’s Distributed Sniffer stores traffic involving the affected device as either source or destination.
With the data from the Distributed Sniffer, you can better assess attackers’ methods and take post-incident actions. This is the only solution for HDOs to collect data effectively during a security event.
Developing Post-Incident Reports and Actions
After you’ve formally investigated the root cause of an attack and the extent of its spread, it’s time to do follow-up work. Post-incident analysis and activities are important for the long-term security of your organization.
Generating Insights Based on the Incident
While a security violation is, of course, a negative event, it also has the positive side effect of teaching you which threats to work against. Consider the event an opportunity to reevaluate how your processes are working. For instance, you may want to conduct penetration tests to gauge the readiness of your network.
A reassessment should identify improvements that need to be made within the organization. Examine your policies to see what may have contributed to the vulnerability and needs reshaping. Did any procedures in particular fail to prevent the attack?
To generate insights, you want to study the data. With experience and reasoning, you can draw inferences about the incident. This is like using the scientific method or any rigorous investigative technique. Patterns in the data may reveal individuals, locations, or events that arouse suspicion. By tying together various threads, you can reach a sound conclusion.
Having corroboration from multiple sources helps—which is why it’s useful to have collected data well.
As with collecting evidence, you want to document all important steps taken during the analysis and reporting stages. In presenting the findings from your investigation, be sure to note any areas of uncertainty or compelling alternative explanations.
Which information you include in a report depends on the audience. For more technical audiences, it may make sense to include detailed data; meanwhile, a business audience may prefer a more visual summary—and a legal audience may yet ask for exhaustive descriptions.
It’s also important to stay abreast of the latest developments and technologies. Technology evolves rapidly, and the key to success is to keep learning. Asimily offers next-gen solutions for forensic analysis and security of medical devices.
Creating Action Plans Based on Post-Incident Insights
After reviewing reassessment documents, identify a responsible person or group to implement the action items from your “after-action report.” These items may include tabletop exercises, educating and retraining employees, and utilizing a third-party provider to monitor systems continuously.
In your report, you should note any actions that would lead to further information or prevent another problem from occurring. For example, if you find any exploited vulnerabilities, note these so they can be closed. You should also include any policy recommendations in your report.
It’s a good idea to arrange a team meeting after your forensic analysis to go over your procedures and policies. You may want to reconsider your data storage policies or your access controls, for instance. Don’t neglect to tell employees about any new policies.
One approach to proactively improving your cybersecurity is running a simulation of attacks. A great example of this simulation is the “Cyber Storm” events run in collaboration with law enforcement, regulatory agencies, participating HDOs, the Department of Homeland Security (DHS), Cybersecurity and Infrastructure Security Agency (CISA), and Information Sharing and Analysis Centers (ISACs). These “Cyber Storm” events are table top exercises that HDOs have regularly participated in since 2015.
But all HDOs have the critical infrastructure to protect and can benefit from the practice of simulating cyberattacks, regardless of institutional size. You can do conduct simulations as simply as having team members answer hypothetical questions in a room—or develop more advanced methods.
The goal of simulation and other preparation is to improve your policies and procedures. Asimily’s holistic solutions also include powerful policy management functionality, to cement your organizational policies into network policies. Then it becomes feasible to detect even hard-to-find attacks that attempt to sneak under the radar. You can adjust the policy for any aspect of any device as well since after an IoMT security incident, you may want to revise or add policies.
Improve Your Forensic Analysis with Asimily
Forensic analysis involves collecting and evaluating data, a critical response in the aftermath of cybersecurity problems at healthcare delivery organizations. Furthermore, this analysis improves incident response procedures and policies to protect against future attacks.
Forensic analysis is a process, not just a single action. It starts with your investigation after a cyberattack or suspicious activity has occurred. Then you produce post-incident reports, and take follow-up actions to prevent a recurrence. The right technology along the way can spell the difference between success and failure.
Asimily is an essential platform for protecting IoMT devices—designed specifically for the healthcare industry—that will simplify your forensic analysis, as well as other key security tasks. Asimily’s Distributed Sniffer finds data right when you need answers fast; additional features help secure your network and devices at all times, including before hardware purchases and throughout business operations..
Contact Asimily to improve your healthcare cybersecurity posture today!
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




