Protecting Technology that Saves Lives
Securing Vital Medical Devices
Internet-connected medical devices deliver unparalleled patient care, but they are a top target for cyber criminals. Safeguard your healthcare operations without disrupting care.
Request a Demo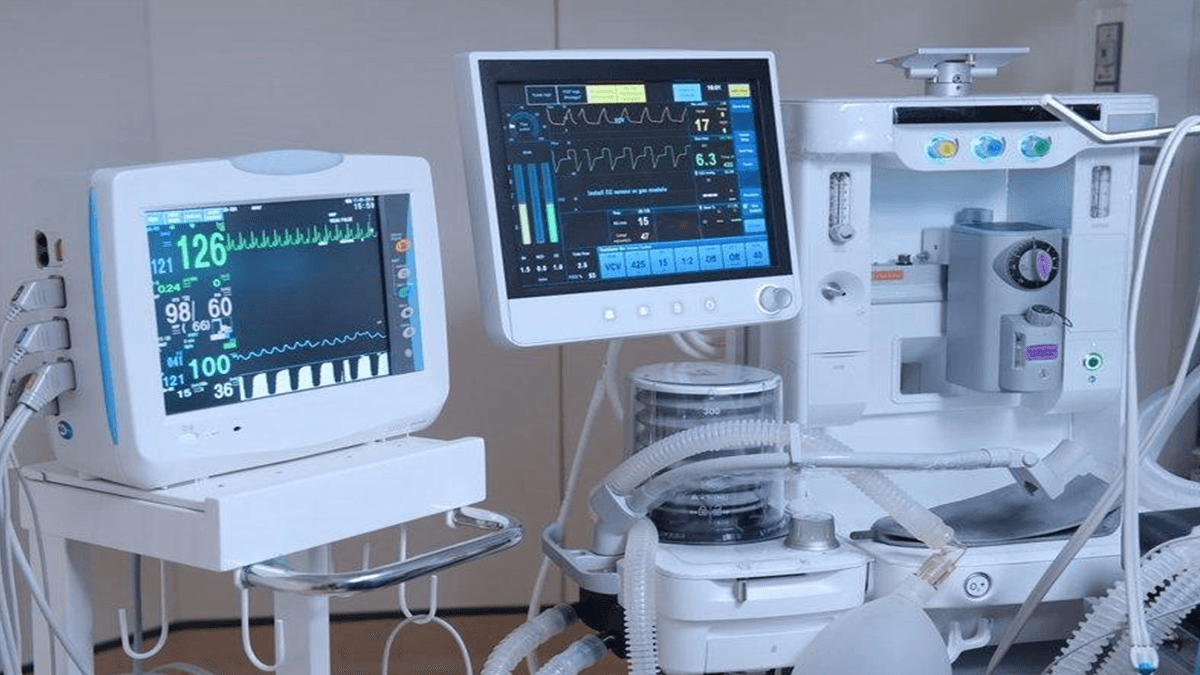
See, Prevent, Minimize, and Model IoT Risks
Protect Every Connected Device
Know Every IoT Device
Keep an accurate inventory of current and new devices, using safe, passive traffic monitoring. Devices are classified and you can customize each one.
Anticipate Threats Proactively
Staying one step ahead of cyber criminals is non-negotiable. Rely on us to discover, inspect, and buttress your connected devices for peak performance and maximum security.
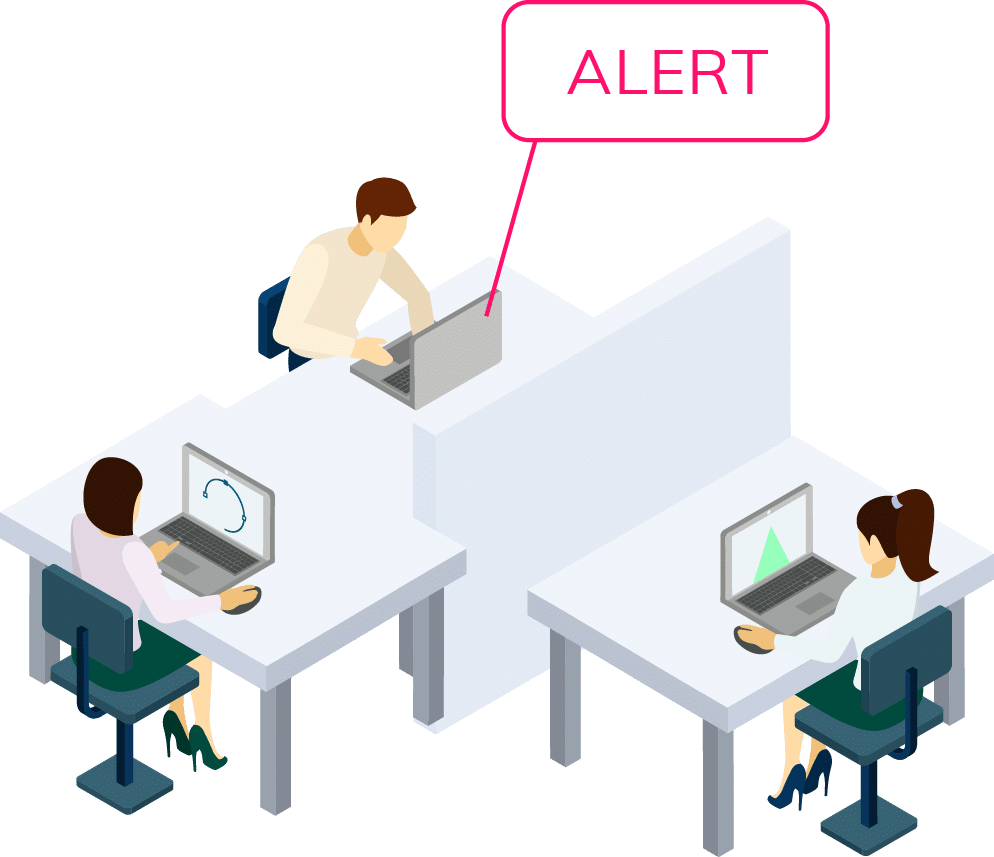
Acknowledge Risks Without Sacrificing Functionality
Patient care should never rest, and neither should vigilance. We monitor all connected devices in your environment for anomalies and alert you of unusual traffic or communications 24/7.
How and Why Medical Devices Get Hacked
Ransomware
As more patient data is stored on connected devices and hospitals rely on these devices, it becomes more enticing for cyber criminals to hold the data for ransom.
Legacy Systems
Outdated medical devices often lack modern security measures, making them prime targets for hackers.
Target Quantity
With over 10 billion IoMT targets, some are bound to be attacked successfully.
Mass Produced
Medical devices are needed in such high quantities that security testing is not always prioritized to ship on time, increasing the risk of defects that could lead to vulnerabilities.
Poorly Guarded
Healthcare professionals wear many hats, and IT expert is not always one of them. Manufacturers often prioritize ease of use over security, leading to vulnerabilities.
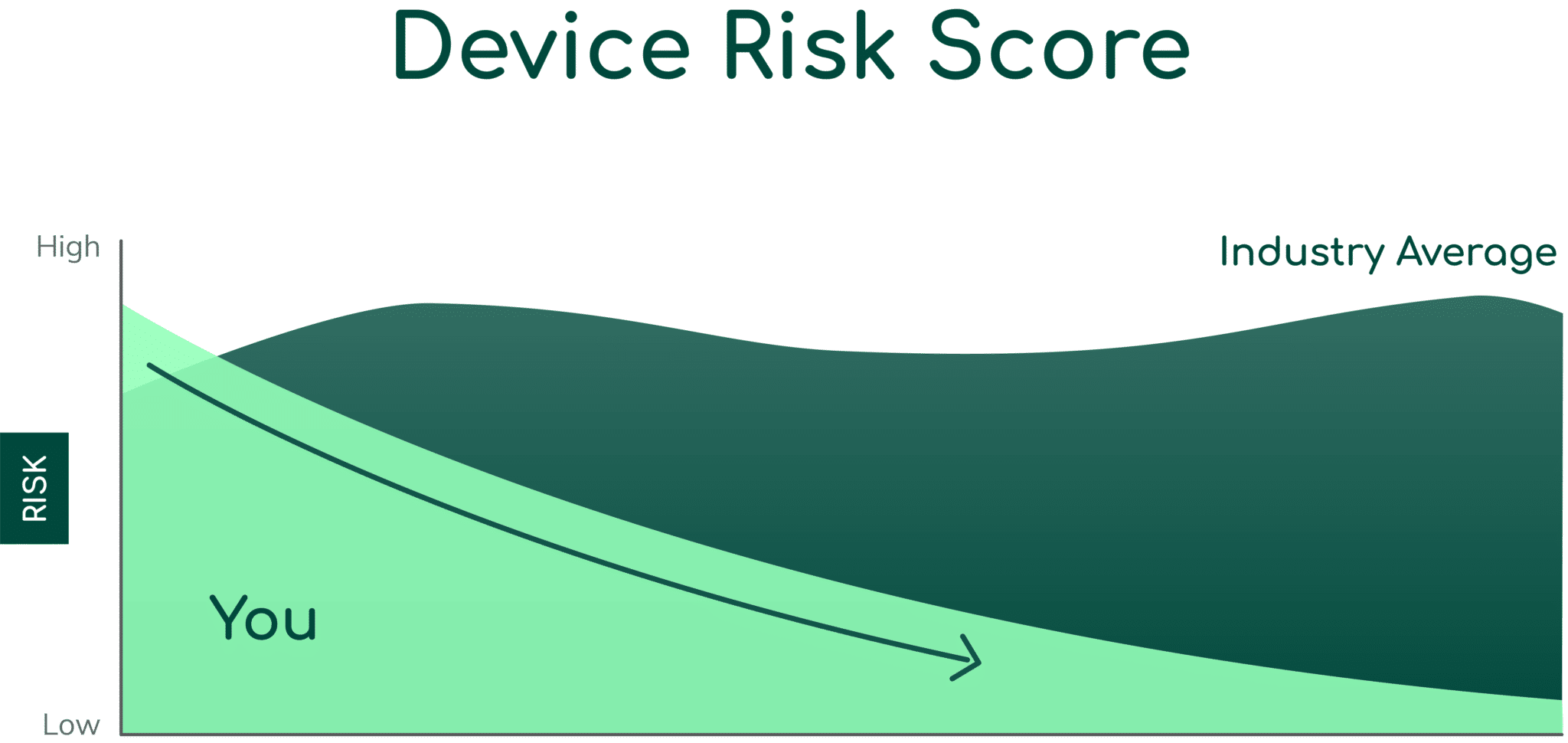
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.
Frequently asked questions
Common types of IoT device vulnerabilities include weak or default passwords, outdated firmware or software, insufficient authentication mechanisms, insecure data transfer and storage, lack of device management, and poor physical security.
IoT device vulnerabilities can have significant consequences for your organization. They can lead to data breaches, unauthorized access to systems, disruption of operations, compromised privacy, financial losses, reputational damage, and even physical harm in certain cases.
Regular vulnerability assessments and proactive mitigation help prevent potential exploits, reduce the risk of cyberattacks, ensure data privacy, and maintain the integrity and availability of IoT systems.
Effective vulnerability mitigation typically involves these key steps: Discovery and inventory of IoT devices. Vulnerability scanning and assessment. Prioritization based on risk analysis. Remediation of vulnerabilities. Ongoing monitoring and reevaluation. Reporting and documentation of efforts.
Assessment of risks should be conducted on a regular basis to keep pace with the evolving threat landscape. Frequency of these assessments may depend on factors such as industry regulations, risk tolerance, and criticality of the devices. A general rule of thumb would be to conduct vulnerability mitigation activities quarterly.