Find out Which Vulnerabilities Matter the Most (and the Least)
By focusing on your truly risky vulnerabilities and devices, become safer and faster.

Reduce Device Cyber Risk

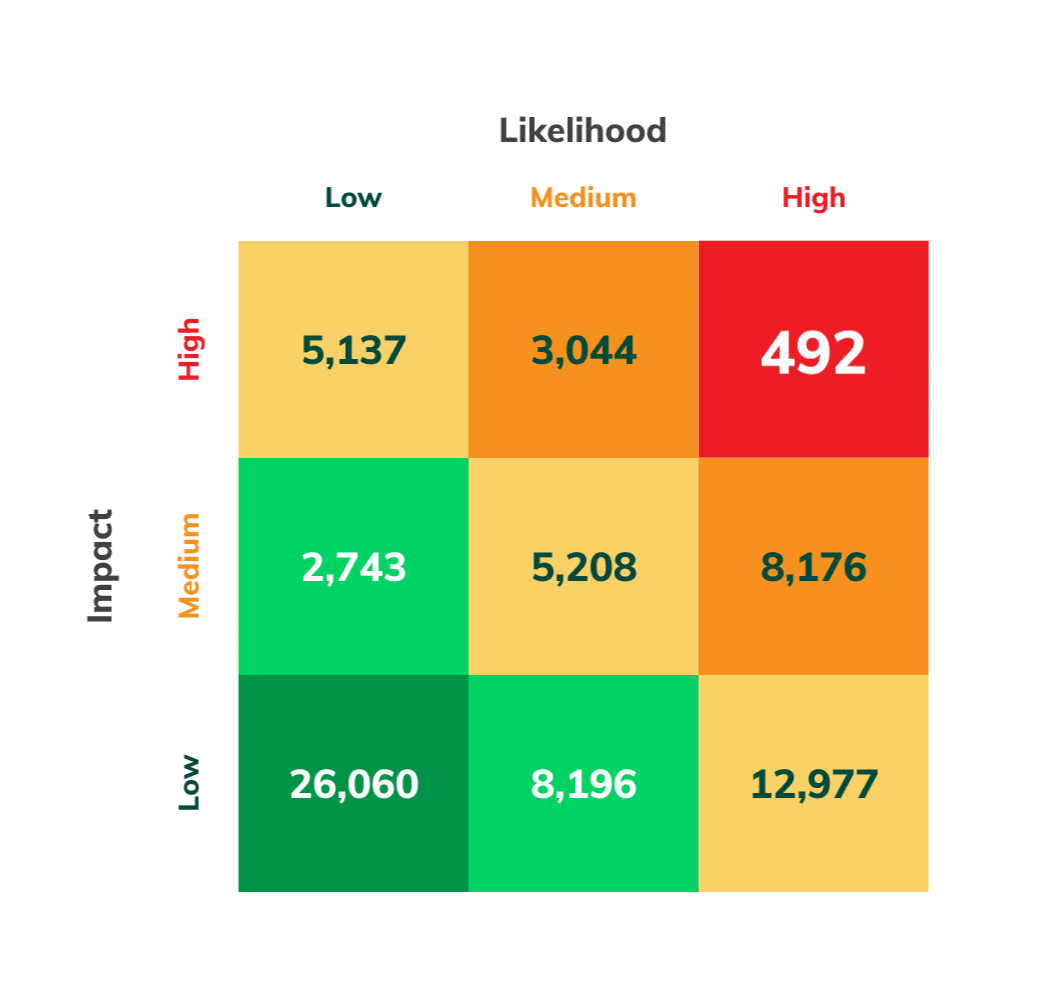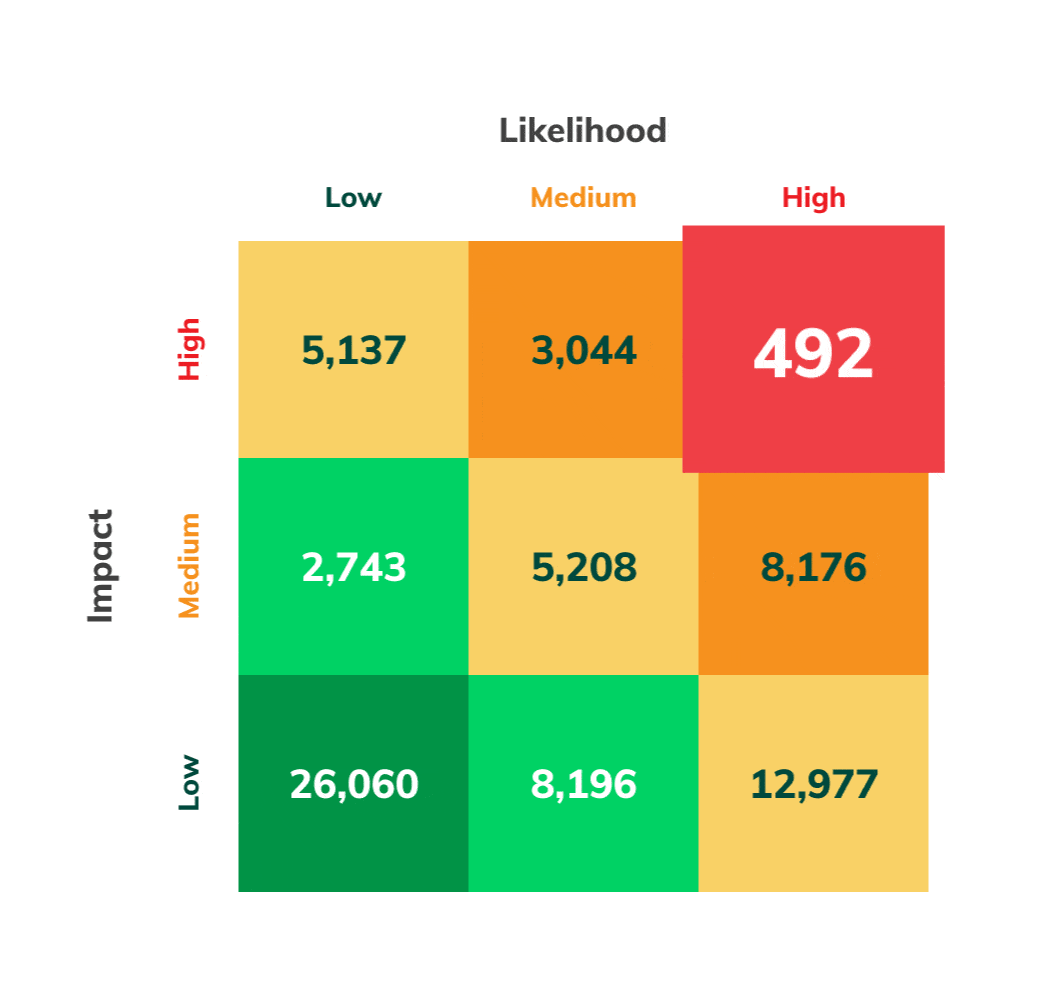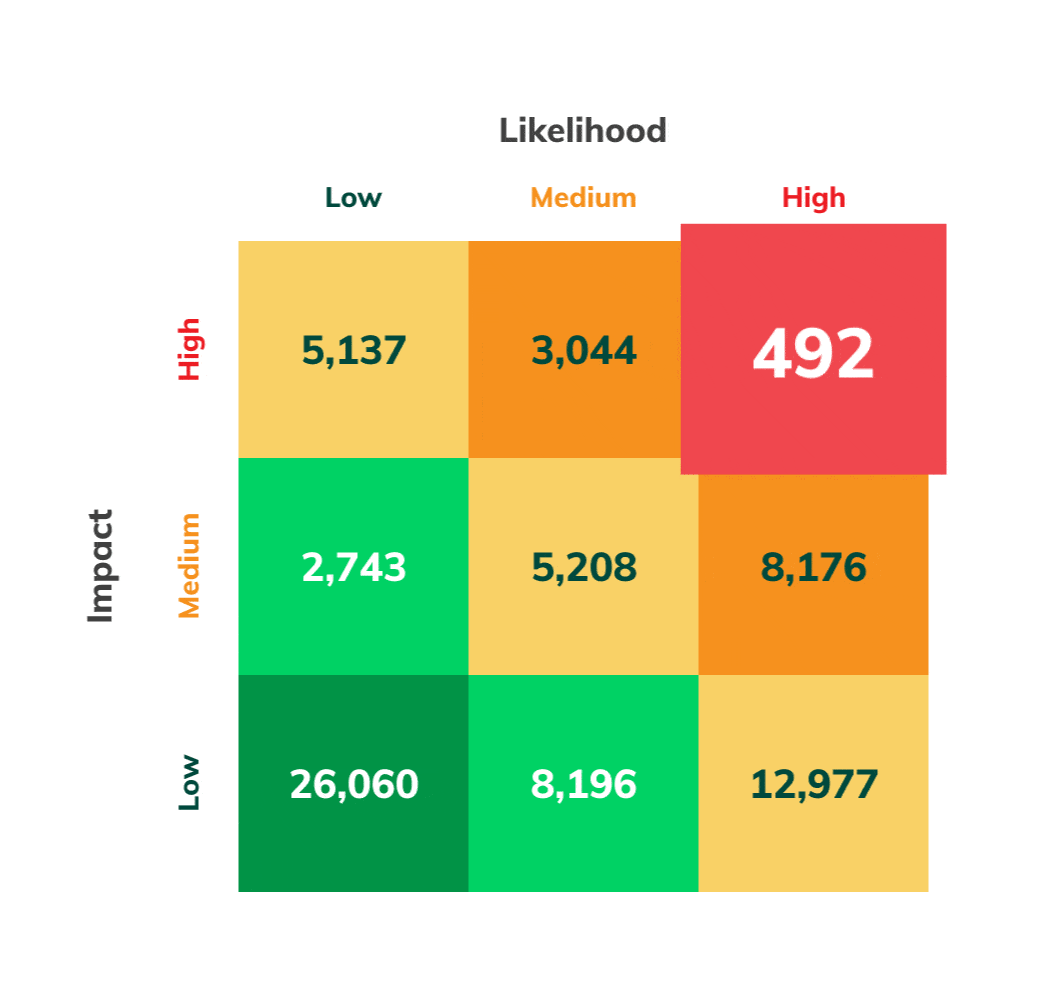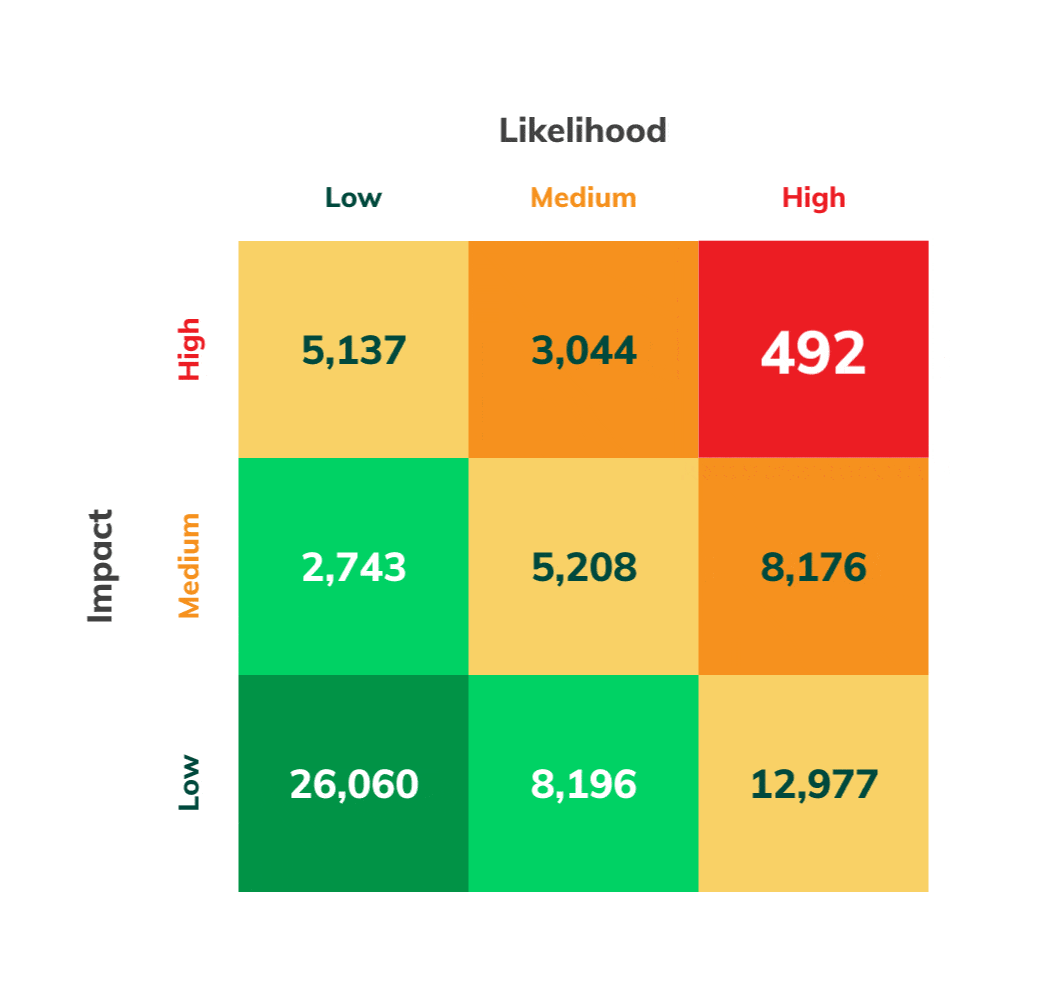
Vulnerabilities Ranked by Exploitability Risk and Danger
With Asimily’s detailed Likelihood and Impact analyses, vulnerabilities and devices get ranked, showing you the most critical changes needed to reduce risk. This helps avoid activity that doesn’t reduce the biggest risks.
Get in TouchPrioritize Faster, Leave Attackers Behind
Always Know the Next and Best Action to Take
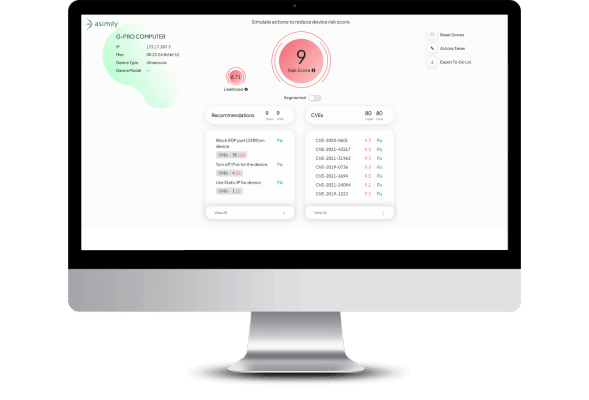
Model Risk Reduction, Save Effort
See Risk ROI for any given action with Risk Simulator – save time for your scarce cybersecurity resources.

Gain Efficiency with Device and Vulnerability-Level Analyses
Asimily’s AI/ML + NLP technology plus Asimily Labs’ analyses highlight the most important IT, IoT, IoMT, and OT devices and vulnerabilities to prioritize – giving you dramatically less work to perform while slashing true risk down to size.

Get Better, Efficient Fixes
Navigating the complexities of device vulnerability mitigation can be overwhelming. Asimily provides you with ranked, simple, fix instructions and utilization data. Use those insights to remove the riskiest problems faster.

Reduce Risk
Asimily understands that demonstrating your organization’s defense is essential. Get a clear risk score from 0-100, allowing you to assess your security against peers and track progress over time.
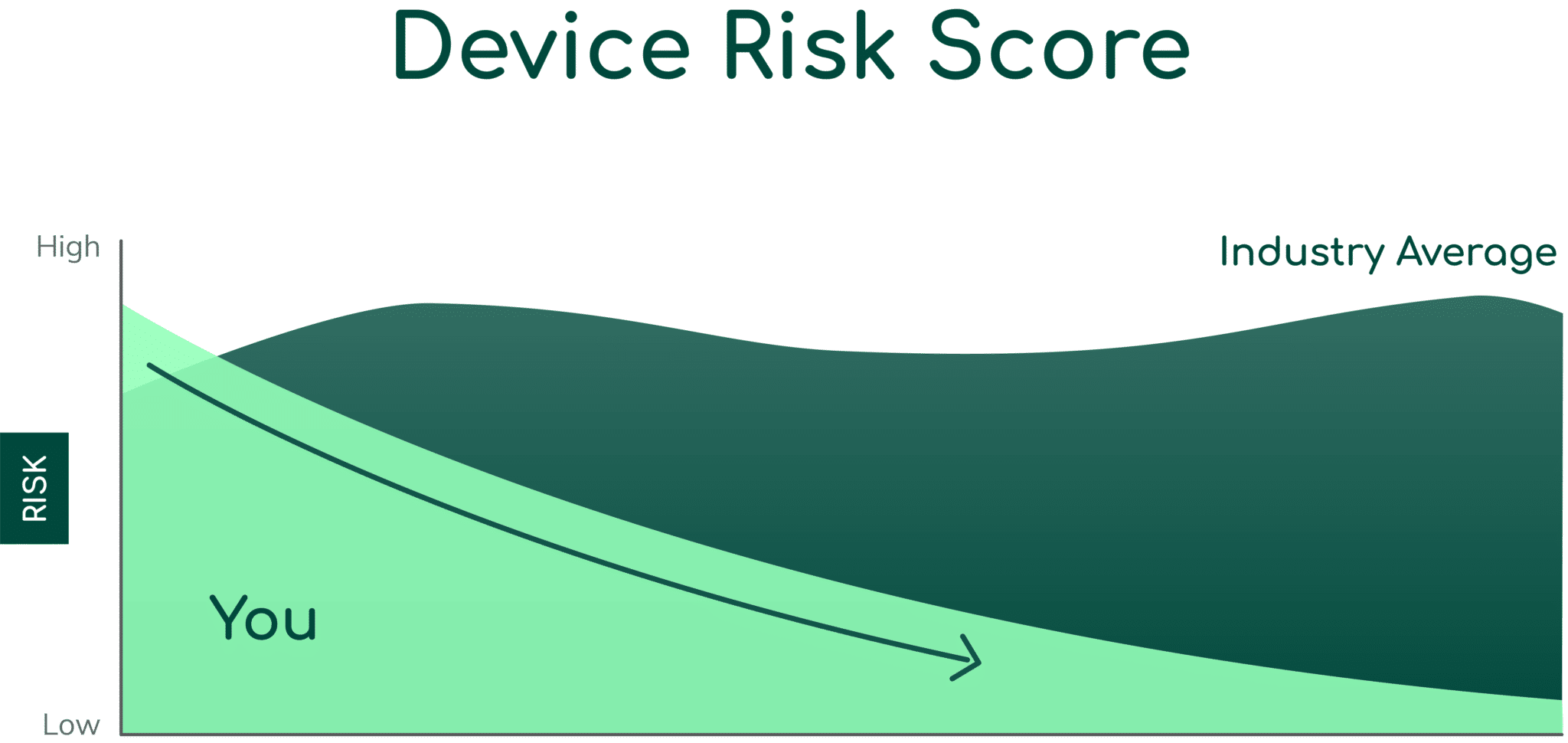
Model Changes that Reduce Risk
Asimily helps you optimize team time by showing you the impact of different mitigation strategies before starting any work. Tackle the most important vulnerabilities first.
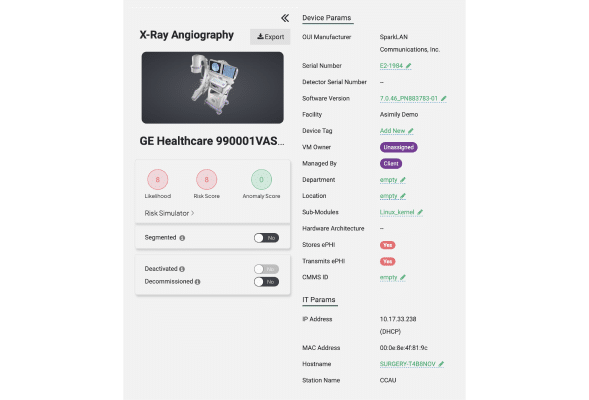
Use Network Configuration to Measure Real Risk
Asimily evaluates each new vulnerability and customizes the risk level for each individual device, considering the vulnerability, importance, network, and configuration factors. Reduce real risk; not theoretical risk based on vuln data alone.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.
Protecting Your Industry’s Unique Devices
Healthcare
Asimily provides the necessary tools to identify and address IoT vulnerabilities in healthcare, ensuring the protection of patient data without interrupting the delivery of critical care.
Discover MoreManufacturing
In an industry that relies heavily on IoT devices to drive automation, efficiency, and connectivity, Asimly can help. By ensuring the security of IoT devices, manufacturers can safeguard their intellectual property, prevent production disruptions, and maintain the trust of their customers and partners.
Discover MoreHigher Education
Educational institutions depend on interconnected devices to facilitate learning, research, and campus operations. Protect sensitive student and faculty data, maintain operational integrity, and foster a secure, productive academic environment with Asimily.
Discover MoreGovernment
Asimily equips government entities worldwide with the necessary tools to secure their IoT devices, protect critical infrastructure, and ensure data privacy. Defend against cyber threats and uphold public trust by proactively mitigating vulnerabilities.
Discover MoreLife Sciences
Where delicate research, development, and data exchange are ongoing, securing your IoT devices is a top priority. Proactively manage and mitigate vulnerabilities, reducing the risk of theft or loss of critical research and development efforts.
Discover MoreFrequently asked questions
Common types of IoT device vulnerabilities include weak or default passwords, outdated firmware or software, insufficient authentication mechanisms, insecure data transfer and storage, lack of device management, and poor physical security.
IoT device vulnerabilities can have significant consequences for your organization. They can lead to data breaches, unauthorized access to systems, disruption of operations, compromised privacy, financial losses, reputational damage, and even physical harm in certain cases.
Most organizations struggle to keep up with the sheer volume of cybersecurity jobs to be done. Hardening due to new vulnerabilities, seeing if a vulnerability is relevant, investigating anomalies, and keeping up with regulatory requirements take up significant time. As a result, prioritizing the riskiest vulnerabilities to address first becomes essential to mitigate risk.
Effective vulnerability prioritization requires understanding which vulnerabilities even apply to your environment. Then it has to be assessed in the context of your devices. Is the vulnerability risky or not? The same vulnerability could be risky if it is known to be exploited in the wild, trivial to execute, or present on critical devices. Numerous other factors enter into the analysis. A simple way to group these considerations is assessing the Impact and Likelihood of an exploit due to an unmitigated vulnerability.
Attackers have scale, time and professionalism on their side. They’ll get a jump on less prepared organizations who will eliminate less risky issues before more risky issues. This expands vulnerability windows and increases the likelihood of a successful attack – in general and against devices.






