Protecting Technology that Saves Lives
Securing Vital Medical Devices
Internet-connected medical devices deliver unparalleled patient care, but they are a top target for cyber criminals. Safeguard your healthcare operations without disrupting care.
Request a Demo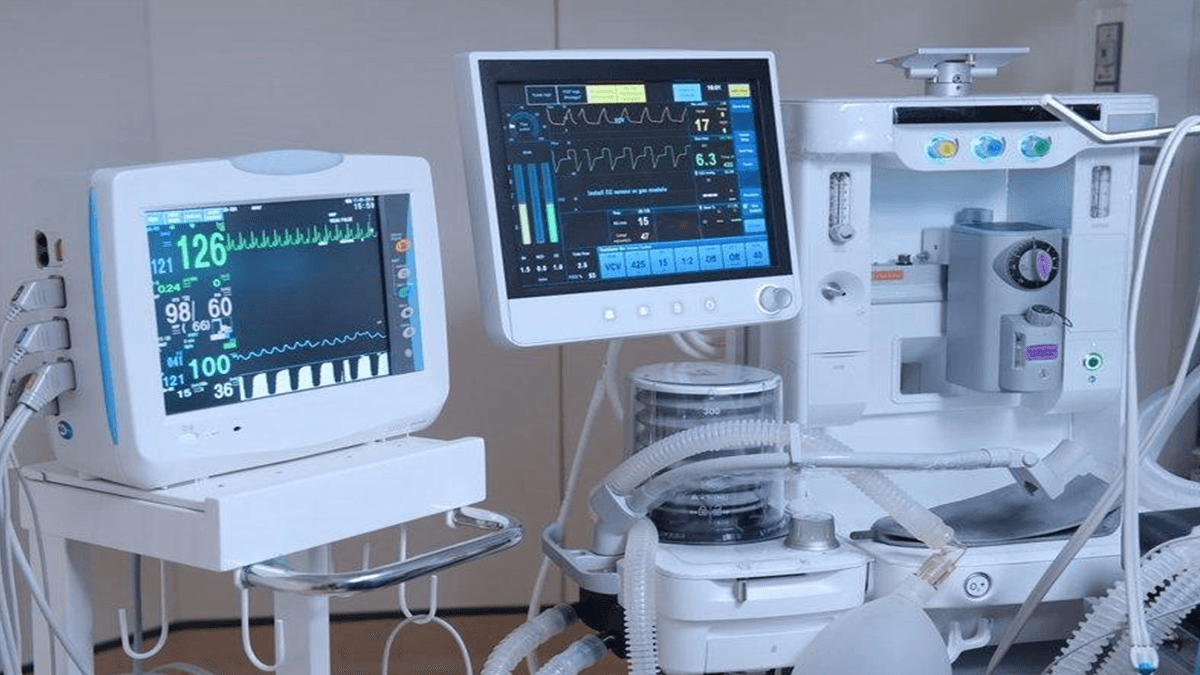
See, Prevent, Minimize, and Model IoT Risks
Protect Every Connected Device
Know Every IoT Device
Keep an accurate inventory of current and new devices, using safe, passive traffic monitoring. Devices are classified and you can customize each one.
Anticipate Threats Proactively
Staying one step ahead of cyber criminals is non-negotiable. Rely on us to discover, inspect, and buttress your connected devices for peak performance and maximum security.
Acknowledge Risks Without Sacrificing Functionality
Patient care should never rest, and neither should vigilance. We monitor all connected devices in your environment for anomalies and alert you of unusual traffic or communications 24/7.
How and Why Medical Devices Get Hacked
Ransomware
As more patient data is stored on connected devices and hospitals rely on these devices, it becomes more enticing for cyber criminals to hold the data for ransom.
Legacy Systems
Outdated medical devices often lack modern security measures, making them prime targets for hackers.
Target Quantity
With over 10 billion IoMT targets, some are bound to be attacked successfully.
Mass Produced
Medical devices are needed in such high quantities that security testing is not always prioritized to ship on time, increasing the risk of defects that could lead to vulnerabilities.
Poorly Guarded
Healthcare professionals wear many hats, and IT expert is not always one of them. Manufacturers often prioritize ease of use over security, leading to vulnerabilities.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.
Frequently Asked Questions About OT Security
OT security must prioritize availability and safety over confidentiality. OT environments include specialized protocols (Modbus, DNP3, CIP), legacy systems that can’t be patched, and devices with 20+ year lifecycles. Asimily’s platform addresses these unique OT security challenges with specialized protocol parsing, compensating controls, and risk-based prioritization designed for operational technology.
Legacy OT devices often can’t be updated or replaced. Asimily provides compensating controls through network segmentation recommendations, configuration monitoring to detect changes, and behavior analysis to identify anomalies—all without requiring agents or modifications to your OT systems. Our passive monitoring ensures zero impact on production systems.
Yes. Asimily’s OT security platform provides robust integrations with SIEM, SOAR, CMDB, and vulnerability management platforms. Unlike competitors with limited on-premises integration capabilities, we deliver the unified IT/OT inventory and risk visibility your security operations center needs to protect against cross-domain attacks.
Asimily goes beyond basic asset inventory by identifying your “crown jewel” OT systems—the devices and processes most critical to your operations. Our platform uses contextual analysis to understand device criticality based on its role in production, safety implications, revenue impact, and position within your Purdue Model architecture. By mapping device relationships and dependencies, we help you prioritize security investments and implement appropriate compensating controls for your most vital OT infrastructure, whether it’s an aging production line generating significant revenue or safety-critical systems in hazardous manufacturing processes.
Comprehensive OT security requires understanding risks from all network points—not just OT devices in isolation. Asimily provides complete visibility into your entire attack surface, including IT/OT convergence points, network neighbors that could serve as pivot points for attackers, and IoT devices that interact with your OT environment. Our platform identifies risks from adjacent systems like HVAC controllers or building management systems that attackers historically exploit to reach critical OT networks. This holistic view ensures you understand and can mitigate risks from any potential entry point, not just direct OT vulnerabilities.