The Power of Many: Harnessing Healthcare Device Synergy Across a Multi-Location Network

One of the most common problems healthcare delivery organizations (HDOs) face is optimizing medical device utilization. For large HDOs with multiple locations, this can be especially challenging. Health technology management (HTM) teams can easily be overburdened maintaining standalone medical equipment, and the proliferation of Internet of Medical Things (IoMT) devices adds new cybersecurity risks for teams to address.
To ensure their facilities continue to provide a superior patient care experience and to maximize the ROI from each medical device, HDOs must ensure that every medical device is being used to its fullest and that IoMT security risks are adequately mitigated. Understanding device utilization goes hand-in-hand with optimizing device security, especially for organizations with a large fleet of connected devices. But how can HDOs get the insights they need across multiple locations and teams?
Effective device utilization is a collaboration between HDOs and IoMT security companies. By selecting the right partner, HDOs can ensure that each device is used to its fullest and improve resource allocation across all locations.
What Is Device Utilization Management in Healthcare?
One of the biggest challenges modern HTM teams face is knowing how many devices they have and where they are located. Some medical equipment, like infusion pumps, defibrillators, and patient monitoring devices, are highly mobile and likely to be used multiple times throughout a shift. Further compounding the problem, many healthcare facilities overestimate device needs to ensure availability, which can lead to underutilization. According to a study by Wollega University, two out of five pieces of medical equipment are underutilized. Underutilization of medical equipment leads to wasted resources and reduces effectiveness, which can have trickle-down impacts on patient care.
Device utilization is especially critical for IoMT devices, as they can quickly proliferate within an HDO’s network and are often ideal targets for malicious actors. Effective utilization management mitigates cybersecurity risks for these devices by creating robust device inventorying, understanding which devices on the network communicate with one another, and identifying potentially anomalous behavior patterns.
Benefits of Device Utilization Management
Device utilization management offers substantial advantages to both HDOs and patients. Devices like MRI machines are costly to purchase and run, and getting the safest uses out of each is essential for optimizing uptime and financial success. By implementing an effective device utilization monitoring and management system, HDOs can gain insights into which devices are in high demand and underused, allowing for informed decision-making regarding equipment allocation.
For example, an HDO with a high-device utilization of MRI machines or infusion pumps can prioritize the patching and maintenance of these devices, reducing the burden on HTM teams. Now, imagine this HDO is comprised of several different hospital networks. Rich insights on device utilization would allow the HDO to ensure resources—in this case, MRI machines and infusion pumps—are well allocated among the hospitals that need them most.
What are the Challenges of Utilization Management Across Multiple Locations?
Over the past several years, HDOs have seen rapid technological advancement, embracing IoMT technology to enhance the patient care experience and addressing new cybersecurity concerns on razor-thin budgets. Keeping pace with technology innovation in a digital-first economy can be challenging. Now, more than ever, HDOs need accurate device metrics across all locations.
When HDOs have accurate device inventory and utilization metrics, they uncover actionable ways to reduce risk. For example, HTM personnel can leverage this data to implement an evidence-based approach to maintenance, scheduling outages when it will be least disruptive to patient care delivery. Alternatively, they may also leverage the utilization data for an Alternative Equipment Maintenance (AEM) program, where teams alter the frequency of OEM recommended maintenance for devices with low usage.
For IoMT devices, it can be challenging to tell what each device is used for and when. Without that information, it can be difficult for HDOs to effectively engage in capital planning and determine what quantities of devices are needed in the future, as well as how regularly devices in their current fleet need maintenance.
Suppose an HDO receives a request for more infusion pumps but doesn’t know if more devices are necessary. A purpose-built IoMT management platform like Asimily can provide a detailed utilization summary for the department requesting new infusion pumps. The utilization percentage is high, but what other data is available?
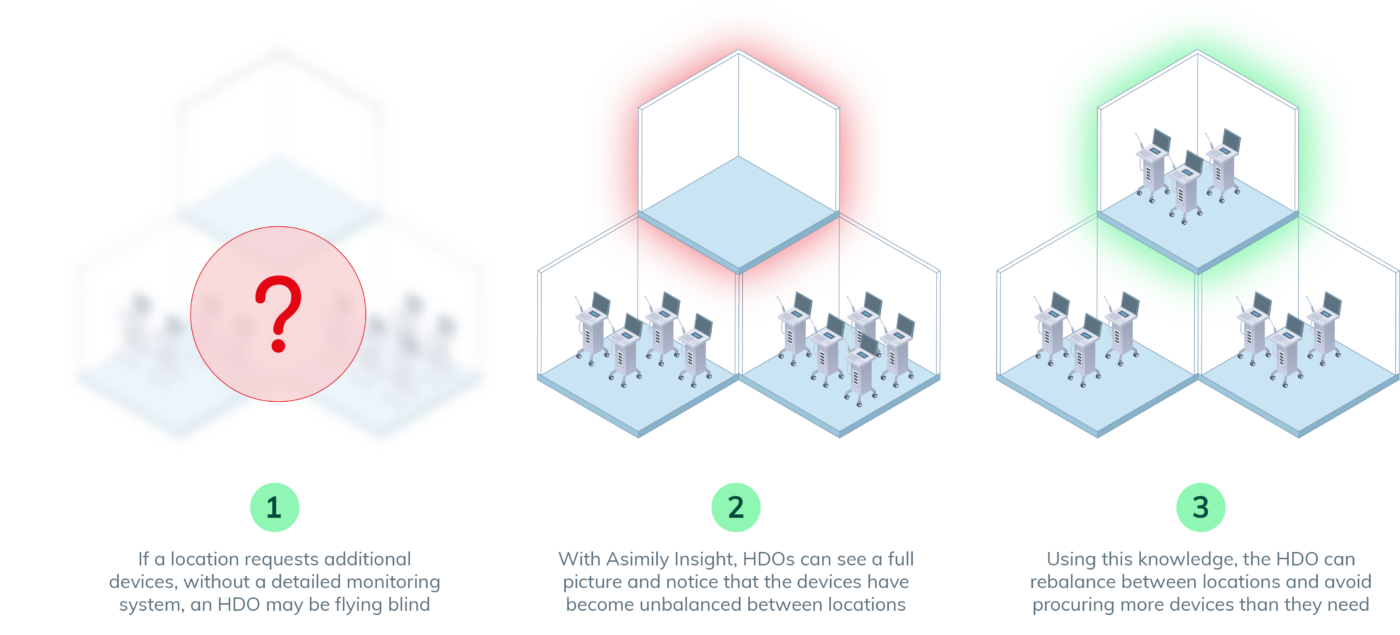
The Asimily platform can determine how many infusion pumps were used simultaneously across locations and identify any devices that were not in use. If a device was inventoried but not in use, it could have been misplaced or misallocated to a different department. By identifying these devices, the HDO can rebalance their allocation of infusion pumps across all locations.
Case Studies: The Power of Device Utilization for HDOs
Partnering with the right IoMT security vendor provides HDOs with a strategic approach to device utilization. Integrating accurate device metrics into a broader security program has measurable risk reduction benefits that keep healthcare facilities safer, allowing them to focus more on patients and less on cybersecurity risks.
Accurate Device Utilization Helps Six-Hospital System Increase Vulnerability Remediation
Methodist Le Bonheur Healthcare, a six-hospital system, faced significant challenges in managing and securing its extensive network of connected medical devices across multiple locations. Their HTM team needed a way to track, classify, and secure over 65,000 devices—without any formal HoMT security program in place. Realizing that their current system was insufficient, they initiated a formal process to select an IoMT security vendor, ultimately choosing the Asimily platform to meet their needs.
With Asimily, the team at Methodist Le Bonheur achieved full visibility into device activity, reducing their vulnerability remediation time by 85%. This solution helped Methodist Le Bonheur proactively detect and respond to potential cyber threats, improve their device utilization, and avoid unnecessary equipment purchases by reallocating underused devices to other facilities in-network where they were most needed.
How Asimily Helps HDOs Improve Device Utilization at Multiple Locations
Asmily helps HDOs ensure that every medical device is being used to its fullest, allowing HDOs to make better use of their devices, save money, and dedicate more resources to patient care. Additionally, Asimily effortlessly scales insights across multiple locations without incurring the astronomical costs of re-deploying the solution at each location.
The real-time transparency of the Asimily platform provides actionable analytics that HDOs can use to maximize the usage of existing medical equipment. Asimily’s capabilities empower HDOs to:
- Uncover a device’s location in real-time within the platform (or by integrating with an asset location solution).
- Centrally manage all assets for multi-location/region deployments through region tagging within the platform – enabling HDOs to holistically understand their device fleet.
- Identify underutilized devices to increase utilization by 25% or more through optimized scheduling
- Track study and image counts to inform maintenance/replacement planning, potentially extending equipment lifespan
- Compare utilization across facilities to pinpoint and remedy inefficient use of under-leveraged devices
Utilization is just one of the benefits associated with a comprehensive IoMT security solution, with security as the core value. Asimily helps ensure the security of all connected IoMT devices on the network. Our inventory and vulnerability detection capabilities are built to monitor traffic to and from IoT equipment and proactively identify security fixes, which are often simple and quick.
In the event of a cyberattack, our platform, with its rapid response features, quickly captures packets to aid incident responders. With Asimily, teams can keep a handle on their IoT attack surface and ensure they are as safe as possible, providing a sense of reassurance and security.
To learn more about Asimily, download our whitepaper, IoT Device Security in 2024: The High Cost of Doing Nothing, or contact us today.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




