Securing Medical Devices Throughout their Lifecycle: The Role of Collaboration
Securing medical devices is a constantly evolving challenge due to the nature of device complexity and the quickly changing security landscape. A lack of collaboration between shareholders and limited budgets often complicates attempts by Healthcare Delivery Organizations (HDOs) to mitigate these issues.
The consequences of having unsecured medical devices can be devastating. According to a survey by the Ponemon Institute in 2022, cyberattacks increased patient mortality for 20% of HDOs.
To keep patients safe, stakeholders throughout the healthcare industry must work together to secure medical devices across their entire lifecycle, from manufacture and deployment through maintenance and eventual decommissioning.
Understanding the Medical Equipment Lifecycle
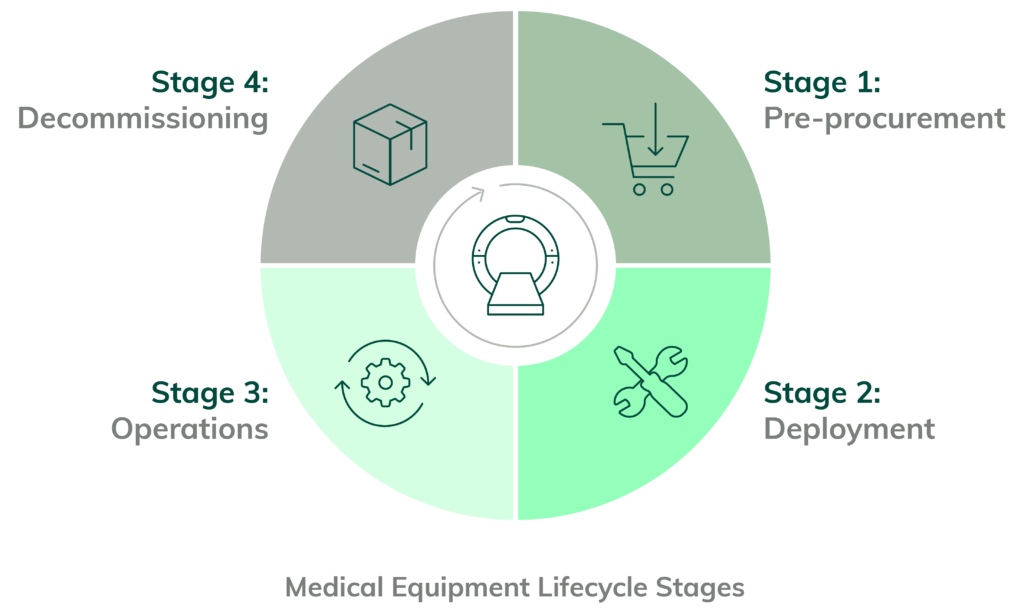
The Medical Equipment Lifecycle (MELC) is a framework for understanding the steps in deploying and managing medical devices. It’s intended to help maintain the device’s integrity throughout its lifetime and is integral to the Internet of Medical Things (IoMT) security.
The Medical Equipment Lifecycle is the process of managing medical equipment, from initial purchase and maintenance to eventual disposal. It includes establishing policies and procedures for the use of medical equipment, managing, and keeping track of equipment maintenance, and planning for replacements when the equipment reaches the end of its useful life.
The four stages of the Medical Equipment Lifecycle as they relate to cybersecurity:
Stage 1: Pre-Procurement Risk Assessments and Procurement of the Medical Device
In this stage, HDOs identify the type and model of the medical device to be procured and deployed. It’s essential to ensure the device is compatible with existing networks and clinical applications. Cybersecurity vulnerabilities are determined by using public and manufacturer databases and analyzing similar real-world deployments, including the most commonly used configurations.
An IoMT risk management platform can perform these analyses and offer insights into the optimal configuration for initial deployment.
Stage 2: Deployment of Network-Connected Medical Device
Securing medical devices at the device level is possible, such as disabling specific ports or limiting network access. Often devices are manufactured using general-purpose technologies, such as embedded browsers. These technologies often default to openness but should be locked down tightly for only the clinical need delivered by the device overall.
An effective IoMT solution will continuously monitor and update authentication protocols, logging systems, alerting mechanisms, and audit trails.
Digitizing Manufacturer Disclosure Statements for Medical Device Security (MDS2s) and Software Bills of Material (SBOMs) is also crucial for this stage. MDS2s provide information on securing medical device components and how to update them per new vulnerabilities, while SBOMs offer a list of all software installed on a medical device. Manufacturer disclosure of SBOMs will be required by the US Food and Drug Administration (FDA) starting in 2023.
Through analysis, the IoMT security solution should determine the efficacy of existing security measures and suggest viable ways to improve them.
Stage 3: Operating the Network-Connected Medical Device
During the life of the network-connected medical device, two bad cybersecurity outcomes can impede the operation of the device. First, an attacker can get past defenses to modify a device’s function. Second, a modified device can misbehave on the network.
Shoring up defenses requires Vulnerability Mitigation. Any vulnerability must first be identified, then prioritized thoughtfully. Will this vulnerability affect a high-impact procedure? Is there evidence that this vulnerability is likely to be exploited? How does my configuration affect the vulnerability?
Or, if a device starts to misbehave, it should be detected very quickly. Putting in tripwires for clearly bad device behavior helps alert security teams if something is going wrong. Further, being able to instantly capture that device’s network traffic via packet capture aids with root cause analysis.
Throughout the operational life of the device, other work will be required to keep it safe and functional. Any manufacturer-endorsed upgrade will need to be evaluated via a risk assessment to consider if and when they should be done. Sometimes these upgrades are purchased, so a cost-benefit analysis is required
These risk assessments, which can take dozens of hours, can be aided by a risk simulation. A risk simulation allows the parameters of a device to be changed to see if that makes the device more or less risky. These simulations, like financial models in a spreadsheet, are quick and easy to run, allowing multiple scenarios to be considered rapidly and cheaply without interrupting the device’s clinical duties.
Stage 4: Decommissioning of the Network-Connected Medical Device
Disposition of the network-connected medical devices is the final stage of the Medical Equipment Lifecycle. Legacy devices are most vulnerable to security breaches, and recognizing when to decommission protects healthcare operations and reduces unnecessary spending. Some decommissioning may be safely delayed with carefully crafted security controls. This can extend the economic and clinical life of some devices.
The Role of Manufacturers in Medical Device Security
Medical Device Manufacturers (MDMs) play a critical role in ensuring the security of network-connected medical devices. Manufacturers are responsible for designing, producing, and testing the devices’ hardware and software components to ensure compliance with current security standards. After the device gets released, manufacturers must provide ongoing support and address new risks.
MDMs can be relied on for thorough testing before the device hits the market. The second part of their responsibilities, however, takes more work. Many medical devices still need upgrades because the MDM never released a patch. The challenge manufacturers face is that upgrading IoMT devices is far more onerous than upgrading typical IT products. The stakes are higher, as medical device failure can lead to patient death.
Securing medical devices requires collaboration between all stakeholders involved in the Medical Equipment Lifecycle. Organizations must work with MDMs to ensure risk management solutions have the most up-to-date information.
The Role of HDOs in Securing Medical Devices
HDOs have the most significant responsibility for securing medical devices. These organizations must remain vigilant regarding cybersecurity and be aware of any potential risks connected to device deployment and maintenance.
They also need to create secure networks to make unauthorized access or tampering impossible. Regular vulnerability scans can identify any existing weaknesses in the system.
Challenges that affect manufacturers also affect HDOs. If the manufacturer does not release an approved patch, upgrading the device is impossible. Replacement is usually too costly to be a reasonable alternative.
HDOs should consider additional measures to protect IoMT devices, such as employing a third-party IoMT security provider.
The Role of IoMT Cybersecurity Providers in Securing Medical Devices
HDOs that use network-connected medical devices should consider collaborating with an IoMT security provider, such as Asimily. An IoMT cybersecurity provider can help heaHDOs assess their risk level and provide guidance on improving their devices’ security.
IoMT cybersecurity providers are adept at identifying gaps in the Medical Equipment Lifecycle. They can illuminate areas where security measures could be improved and help devise a strategy for limiting risks. Healthcare IT departments can entrust stages two and three of the Medical Equipment Lifecycle to their IoMT provider.
Collaboration between IoMT providers, HDOs, and MDMs is necessary for maximum medical device security. IoMT providers can bridge healthcare organizations and MDMs, leading to increased communication and understanding of the risk landscape.
Implementing an Effective Medical Device Security Program
Implementing a working medical device security program in five steps is possible.
Conduct a Comprehensive Risk Assessment
HDOs should coordinate with manufacturers to assess risks and prioritize them by severity. The assessments should occur regularly throughout the Medical Equipment Lifecycle. Cooperation between stakeholders is essential at this juncture because manufacturers report fresh vulnerabilities and release patches when appropriate, while HDOs use the information to manage risk levels.
Asimily can help with the risk assessment process. The platform keeps track of every connected device and monitors vulnerability trends.
Implement Access Controls and Authentication Mechanisms
HDOs should implement access controls, such as two-factor password authentication. Role-based access control can also restrict user permissions.
A good IoMT cybersecurity platform provides secure authentication mechanisms to protect medical devices from unauthorized access. HDOs can customize role-based access control measures.
Regularly Monitor Devices for Anomalies and Suspicious Activity
HDOs should employ automated systems to monitor devices for anomalies and suspicious activity. These automation efforts include keeping track of device performance, logins and activations, and network traffic changes.
Asimily gives a comprehensive view of all connected medical devices and their behavior. The platform looks for anomalies and suspicious activity and will alert the organization if any threats are detected. For example, high volumes of data going to certain countries can be an indicator of compromise (IoC).
Keep Devices Up-to-Date with the Latest Security Patches and Updates
One of the easiest ways to keep devices secure is to apply relevant patches as soon as possible. A delay could result in severe consequences. A January 2022 cybersecurity report found that over 50% of hospital IoMT devices had “known critical risks” that could potentially affect function.
Unfortunately, patches may not be available, despite the known risk. MDMs do not rectify a discovered vulnerability if it’s impractical. In this case, HDOs must decide what risk level they can comfortably operate under. One mitigation is to rely on IoMT providers to apply countermeasures.
Asimily can help with patch management. The platform identifies devices running outdated software versions and can inform the organization when a patch was last installed.
Establish Ongoing Security Awareness and Training Programs
HDOs should ensure that all staff members are aware of security best practices. They should understand the need for passwords, other authentication mechanisms, and general security practices, such as ignoring links sent from unknown email addresses.
Asimily’s webinar series can educate staff and ensure everyone is up-to-date with the latest security threats.
The Power of Partnerships: Real-World Examples of Successful Collaboration for Securing Medical Devices
With the help of solid partnerships, HDOs and IoMT security platforms can work together to ensure that medical devices are properly defended. Asimily is proud to have been part of several successful collaborations in the past few years.
One example is a 1700-bed health system across that had problems with its patient monitors. After a short investigation, Asimily Insight showed significant SNMP traffic flowing to the affected patient monitors. The IP was identified as an internal BMC Discovery tool. Once the tool was turned off, the patient monitor function returned to normal.
The partnership between Asimily and this HDO resulted in an improved security posture across the system.
Asimily: Your Partner in Medical Device Security
Medical devices are highly vulnerable to attack, forcing HDOs to ensure that they have reliable security measures in place.
Asimily helps secure medical devices with our advanced platform. We offer powerful capabilities that allow healthcare organizations to monitor, detect, and respond to threats. Vulnerability prioritization lets your team focus on threats that matter instead of wasting time on minor problems.
We also understand the importance of collaboration. Numerous partnerships and integrations enable working with all stakeholders, from device manufacturers to healthcare providers. With Asimily, medical devices can remain secure and operational at all times.
Schedule a consultation with an Asimily expert to see how you can defend your hospital systems against ransomware and malware attacks with the leading risk management platform for the Internet of Medical Things (IoMT).
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




