Increasing Manufacturing IIoT Cyberattacks and Mitigation Strategies
An unsettling number of large US industrial companies have been hacked this year. A shortlist of 2023 IIoT attacks and losses in just the past twelve months provides insight into the IIoT security challenges that the manufacturing industry faces as threat actors continue to target them:
- February: Gates Industrial Corporation, a power transmission company, experiences a ransomware attack where threat actors exfiltrate human resources records
- March: Ingersoll Rand, a compressor giant, experiences a ransomware attack where malicious actors leaked an estimated 3% of the stolen data
- August: Freeport-McMoRan Inc., a copper and gold mining company, experienced service disruption arising from a cybersecurity incident affecting its information systems
- September: Johnson Controls International, a heating, air conditioning, and fire-safety systems company, experienced a ransomware attack that also impacted two of its subsidiaries where malicious actors allegedly stole over 27 terabytes of data, potentially including Department of Homeland Security (DHS) floor plans and security information, and encrypted the company’s VMWare ESXi machines
- October: Mueller Water Products Inc, a maker of fire hydrants, butterfly valves and leak detection technology, experienced a cybersecurity incident impacting operational and information technology systems, noting in late November that facilities had “substantially” returned to normal operations
- October: Fortive Corp., which makes test and measurement tools and asset management software, experienced a ransomware attack, reporting a $5 million one-time expense related to remediation and operational outages
While this may only look like six unrelated attacks, the reality is that this is a limited list. Increasingly, threat actors target the manufacturing industry. Although primarily financially motivated, cybercriminals may look to the industry as part of larger nation-state cyber espionage objectives.
By understanding why malicious actors view manufacturers’ IIoT security vulnerabilities, organizations can implement work more purposefully to mitigate data breach risks.
History of Manufacturing IIoT Security Cyberattacks
Attacks against the manufacturing industry are nothing new. In the notorious 2017 NotPetya attack estimated to cost over $100 million globally, Mondelez, a multinational food and beverage company, suffered permanent damage to 1,700 servers and 24,000 laptops, impacting global production operations. To complicate matters, the attack also included multiple supply chain partners, like Maersk, a shipping container company, and FedEx. To complicate matters in a way that increased total costs arising from the attack, Mondelez’s insurance carrier, Zurich, refused to cover the $100 million claim. The denial cited the war exclusion and sparked a cyber insurance coverage litigation that led to Lloyd’s of London changing their coverage terms permanently.
Despite the size and scope of the NotPetya attack, the historical throughline shows that malicious actors have targeted the industry for years. These costly attacks have made headlines at least once a year with some of the most damaging including the following:
- 2015: Cybercriminals leveraged IIoT security gaps in the HanesBrands to compromise an estimated 900,000 customers.
- 2019: Ransomware group LockerGoga forces Norwegian aluminum manufacturer Norsk Hydro to switch some plants to manual operations.
- 2020: Attackers released over 3GB of data stolen from Advantech, a large Internet of Things (IoT) manufacturer, costing the company an undisclosed amount of money and leading to business interruption.
Taking note from recent history, the attacks against manufacturers are likely to only grow in number and severity. According to IBM X-Force incident response data, malicious actors have focused more intently on the manufacturing industry year-over-year since 2019.
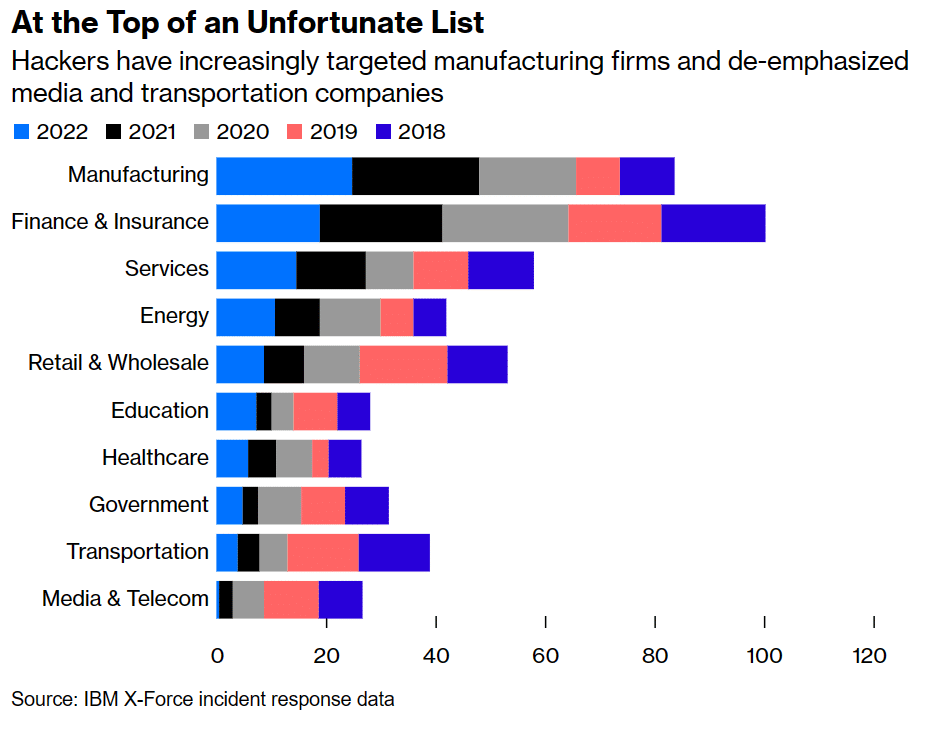
Manufacturing Faces CyberAttack Pressure
Most cybercriminals are financially motivated. They want to quickly deploy attacks against organizations that they know are likely to pay the ransom. The manufacturing industry gives them the return on investment they want because companies in the vertical have more to lose than other victims. Manufacturers have different motivations for paying a ransom than companies in other industry verticals. While many of the reasons may sound similar, like business interruption, the reality is that the way IT environments connect to manufacturing floors means recovering from attacks is more complex. Additionally, the impact on human life arising from these cyber-physical systems changes the organization’s risk matrix.
Lost Revenue From Disruption
While ransomware attacks cause business interruption for any victim, the impact on the manufacturing industry is often more damaging. According to research, an analysis of more than 122 attacks impacting industrial operations found that more than 80% began by compromising IT systems. Manufacturers already struggle with quarter-over-quarters after-tax profit loss. According to the US Census Bureau, the manufacturing industry’s after-tax profits have decreased steadily since the second quarter of 2022, noting that the most recent data from Q2 2023 indicates an overall profit loss of $64.3 billion since then.
Meanwhile, attackers target the human-machine interfaces that link engineering workstations to the public-facing internet. By manipulating these internet-facing applications, attackers can move laterally to undermine manufacturing operations which can have long-term effects, as evidenced by Mueller Water Products taking nearly a month to return to substantially, not completely, normal operations. The lost revenue from a month’s business interruption can ultimately undermine an entire quarter’s earnings.
Physical Harm
The connection between the Industrial Internet of Things (IIoT) and the manufacturing floor changes an organization’s risk profile. For manufacturers, an attack that impacts machinery can have an impact on human health and safety, not just revenue. In these cyber-physical systems, IIoT security risk evaluations integrate with traditional safety hazard evaluations. Most existing risk assessment frameworks focus on traditional data impact and fail to respond to the cyber-physical system need for real-time, dynamic risk modeling and response. With no real way to standardize these controls, manufacturers are more motivated to pay the ransom since they want to protect human life as well as sensitive data.
Intellectual Property and Brand Damage
While other industries, like software, may worry about intellectual property and brand damage, manufacturers often work on sensitive products or with governmental entities. Further, a manufacturer’s intellectual property is often is competitive advantage. If attackers gain access to trade secrets, blueprints, or patented techniques, then the business’s market share can suffer. For example, manufacturers across the Defense Industrial Base (DIB) have long been targeted because their products can have national security and defense implications. Beyond the typical ransomware cybercriminal, nation-state actors engaging in cyber espionage also target the industry. In some cases, the ransomware attack acts as a distraction from a longer-term advanced persistent threat. Even if the company pays the ransom, the attackers may still be stealing data as part of a larger plan.
Easing Burdens By Incorporating IIoT Security
Manufacturers face the dual pressure of securing their environments while still hitting revenue targets. Implementing IIoT enables them to reduce operating costs, manage supply chains, and anticipate maintenance needs. However, securing these devices cost-effectively is challenging as the process often requires specialized technologies and skills.
As manufacturers begin to incorporate IIoT security into their overarching programs, they should look for solutions that give them the insights necessary to respond to these unique problems.
Identify IIoT Devices
Manufacturers should start with a passive scanning solution that can identify and inventory all IIoT technologies without disrupting service. By inspecting packets rather than initiating traffic, these solutions can build accurate device profiles for each connected device containing the following information:
- Operating system
- IP address
- MAC address
- Port numbers
- Hostname
- Version number
By creating a comprehensive IIoT device inventory, manufacturers have the visibility necessary to implement appropriate IIoT security controls.
Scan Networks For Vulnerabilities
With the visibility gained from the initial scan, manufacturers can monitor and manage their IIoT deployments more effectively. A passive vulnerability scanning technology can augment the current IT environment vulnerability scanner data. Typically the data sources are integrated, for a single, accurate inventory.
Once this comprehensive visibility into all connected devices has been achieved, their vulnerabilities can be found and attributed to each IIoT device. A quantifiable and actionable set of risks and how to remediate them becomes available for the first time as a reward for all that hard work.
Prioritize Vulnerability Remediation Activities
Not every vulnerability poses the same risk to the organization’s IIoT security. Remediating every identified vulnerability would be overwhelming and like a game of Whac-a-Mole. With insight into the exploitable vulnerabilities and a detailed analysis of the attack that goes beyond the basic CVE information, manufacturers can focus their remediation activities on high-priority, high-risk issues.
They also need solutions that understand how compensating controls enhance IIoT security. In some cases, no security update exists, or applying the update would impact service. To mitigate these risks, any IIoT security solution should provide simple, short, and effective compensating control recommendations, like:
- Deactivating unnecessary services without impacting clinical function.
- Blocking risky services with a Network Access Control (NAC) tool.
- Hardening vulnerable devices by updating their configurations.
- Implementing micro-segmenting when altering configurations affects the IIoT device operations
Monitor IIoT Devices For Anomalous Behavior
As attackers continue to target the manufacturing industry, companies need more than prevention. They need to identify anomalous activity on their networks that could indicate an attack. Using a solution built for IIoT devices, manufacturers can incorporate these risky devices into their overarching IIoT security monitoring. Integrating this data into their security information and event management (SIEM) tool, they can build high-fidelity alerts that enable faster identification and response times.
Further, with the technical forensic data, they can analyze what happened, tracking down attackers faster and enabling appropriate event reporting to law enforcement. For example, with a passive scanner that captures packet data, they can correlate IIoT device network activity with:
- RAM information from servers
- Traffic information from network devices
- Data transferred to an FTP server
Track IIoT Security Metrics Over Time
Security key performance indicators are critical to a robust IIoT security program. Without visibility into IIoT security, a manufacturing company has a blind spot. However, with comprehensive visibility into all devices connected to the network, the organization can uplevel its security by identifying trends over time. With reports that track risk trends and make technical data accessible, senior leadership and boards of directors can make informed decisions about security initiatives.
With at-a-glance visibility through visualizations, leadership can get the answers they need, including information about:
- Device risk likelihood
- Device security compared to industry peers
- Vulnerabilities closed, including a focus on high-risk vulnerabilities
- Top anomaly categories
Asimily: Risk Management and IIoT Security Monitoring to Ease Manufacturer Burdens
Asimily provides holistic context into an organization’s environment when calculating Likelihood-based risk scoring for devices. Our vulnerability scoring considers the compensating controls so you can more appropriately prioritize remediation activities.
Organizations efficiently identify high-risk vulnerabilities with our proprietary, patented algorithm that cross-references vast amounts of data from resources like EPSS (Exploit Prediction Scoring System), Software Bills of Material (SBOMs), Common Vulnerability and Exposure (CVE) lists, the MITRE ATT&CK Framework, and NIST Guidelines. It understands your unique environment, so our deep contextual recommendation engine can provide real-time, actionable remediation steps to reduce risk and save time.
Asimily customers are 10x more efficient because the engine can pinpoint and prioritize the top 2% of problem devices that are High-Risk (High Likelihood of exploitation and High Impact if compromised). Asimily’s recommendations can easily be applied in several ways, including through seamless integration with NACs, firewalls, or other network enforcement solutions.
Schedule a consultation with an Asimily expert to see how you can efficiently prioritize and remediate vulnerabilities with the leading lIoT risk management platform.
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




