The Next-Generation Cyber Asset and Exposure Management Platform
Complete Risk Mitigation for Any Danger
Risk Mitigation
Divert Attacks
Get simple guidance to protect cyber assets from malicious traffic via segmentation or microsegmentation
Block Exploits
Use clear recommendations to mitigate attack vectors outside of segmentation and patching
Accelerate Patches
Get comprehensive asset management – including IoT password management and IoT patching with a click of a button.

Understand Every Connected Device, Vulnerability, and Status
Inventory and Visibility
Automated, Accurate Inventory
Gain a complete repository of IT, IoT, OT, and IoMT devices while finding “unmanaged” devices
Enrich Your Data with Device Details
Have all your devices’ details, assembled in one place
Safe, Powerful Data Collection
Protect devices during data gathering by using any of passive, protocol-based, API-based, or combinations, including via integrations

Bring Order to Vulnerability Chaos
Vulnerability Prioritization
Prioritize the Highest Risks
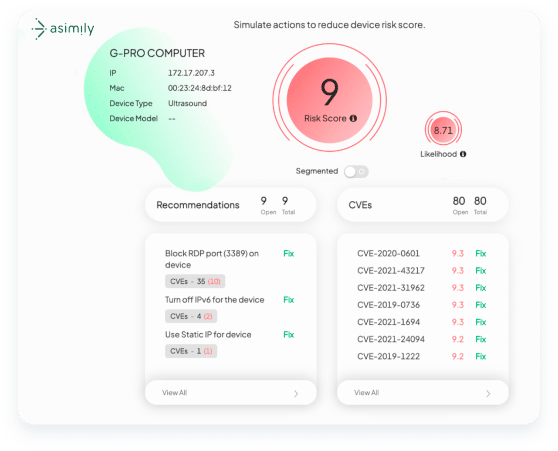
Identify the top 2% riskiest devices in the environment for immediate risk reduction
Know Risks Faster
Shorten exposure windows with continuous detection of new vulnerabilities
Model Risk ROI Before Doing Work
See Risk ROI for any given action before deploying resources with Risk Simulator
Shorter To-Do List
By knowing which vulnerabilities are less risky for you, get time back to focus on riskier issues.

Go from Threat to Resolution Faster and Safer
Threat and Response
Detect Anomalies
Use rules to spot IT, IoT, OT, or IoMT that deviate from allowable activity.
Monitor Device Behavior
With simple pull-downs, augment threat detection with guardrails for your devices triggering alerts or actions
Simplify Incident Response
Capture packets for anything you want to investigate on your network, reducing incident response time and expense.
Governance, Risk, and Compliance
Governance, Risk, and Compliance
Proactive Risk Avoidance
Prevent risk before purchasing with risk modeling and device hardening guidance
Configuration Control
Take snapshots of every device which can be used for recovery, including for ransomware
Detect Configuration Drift
Receive alerts due to drift in device configurations and scroll through their timelines to detect causes
Device Hardening
Gain access to crowdsourced data on the most secure configurations known for individual devices
Protecting Your Industry’s Unique Devices
Healthcare
Asimily provides the necessary tools to identify and address IoT vulnerabilities in healthcare, ensuring the protection of patient data without interrupting the delivery of critical care.
Discover MoreManufacturing
In an industry that relies heavily on IoT devices to drive automation, efficiency, and connectivity, Asimly can help. By ensuring the security of IoT devices, manufacturers can safeguard their intellectual property, prevent production disruptions, and maintain the trust of their customers and partners.
Discover MoreHigher Education
Educational institutions depend on interconnected devices to facilitate learning, research, and campus operations. Protect sensitive student and faculty data, maintain operational integrity, and foster a secure, productive academic environment with Asimily.
Discover MoreGovernment
Asimily equips government entities worldwide with the necessary tools to secure their IoT devices, protect critical infrastructure, and ensure data privacy. Defend against cyber threats and uphold public trust by proactively mitigating vulnerabilities.
Discover MoreLife Sciences
Where delicate research, development, and data exchange are ongoing, securing your IoT devices is a top priority. Proactively manage and mitigate vulnerabilities, reducing the risk of theft or loss of critical research and development efforts.
Discover MoreReduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, people protected, and IT assets secure.
Frequently asked questions
An IoMT security solution is a software platform that provides cybersecurity capabilities focused on IoMT – the Internet of Medical Things, which are network connected medical devices. Those capabilities typically include safely creating an inventory of devices, managing security vulnerability information, providing risk mitigation guidance, and assisting with incident response processes.
An IoT security solution is a software platform that provides cybersecurity capabilities focused on IoT – the Internet of Things, which are network connected devices. Those capabilities typically include providing risk mitigation guidance, safely creating an inventory of devices, managing security vulnerability information, deploying patches, and assisting with incident response processes.
Overall risk – from incidents and vulnerabilities – is typically mitigated in two ways: hardening your attack surface and shortening the life of attacks that get past your perimeter. A risk mitigation platform that has both of those functions can significantly reduce the risk of connected IoT, OT, and IoMT while still allowing them to function.
Organizations have told Asimily that they are most impressed by its attention to service, its broad software capabilities and commitment to rapid risk reduction by any means necessary. Unique capabilities such as packet capture, targeted attack prevention (using the MITRE ATT&CK Framework as a guide, not just a classifier), Configuration Control and many others are also frequently cited.






