The Next-Generation Exposure Management Platform for IoMT, IoT, and OT
Identify, Prioritize, and Mitigate risk across your cyber assets.
Why Asimily?
Identify and Prioritize the Riskiest 2% of Vulnerable Devices
With a detailed, MITRE ATT&CK-based analysis of each vulnerability from Asimily Labs, learn your true risk for IoT, IoMT, and OT Devices – not just what the vulnerability report says. Use Risk Simulator to see risk ROI before completing any given action, saving time.
Find Out HowComplete Device Visibility Done Safely and Tailored to your Environment
Get an accurate inventory of IT, IoT, OT, and IoMT devices, their applications, and their behavior. Safely inventory your network using any of passive, protocol-based, API-based, or integration-based methods to generate a normalized source of data.
Find Out HowThe Only Complete Risk Mitigation Solution
Asimily offers many ways to reduce risk – Targeted Attack Prevention, Device Patching, and Segmentation. Get the choices you need to reduce risk instead of just learning about it.
Find Out HowStrengthen your Responses to Threats
From anomaly detection to aiding incident response, each event investigation matters. Detect potential attacks and enforce policies to ensure security stays robust. All of this with packet capture for incident responders.
Find Out HowCompliance-Ready with Ease
With detailed reporting, record-keeping, device timelines, password management, and Configuration Control, you have what you need for each devices’ unique requirements.
Find Out HowReduce Risk Faster
Asimily analyzes each vulnerability using patented AI/ML and Asimily Labs experts. No stopping at basic categorization. Find out the real risk faced, and how to quickly eliminate it. Asimily customers typically remove more than 10,000 high-risk vulnerabilities in their first 3 months.
Find Out How
Don’t Stare at Dashboards – Take Recommended Action Now
Offers every technique possible to reduce risk now – microsegmentation, targeted attack prevention (180+ types), and patching – a device at a time or automatically.
Find Out How
Secure Your Devices with IoT Patching
Install new, safe firmware for IoT devices in just a few clicks (or none). Speed up IoT patching and password management of devices with a click of a button.
Find Out How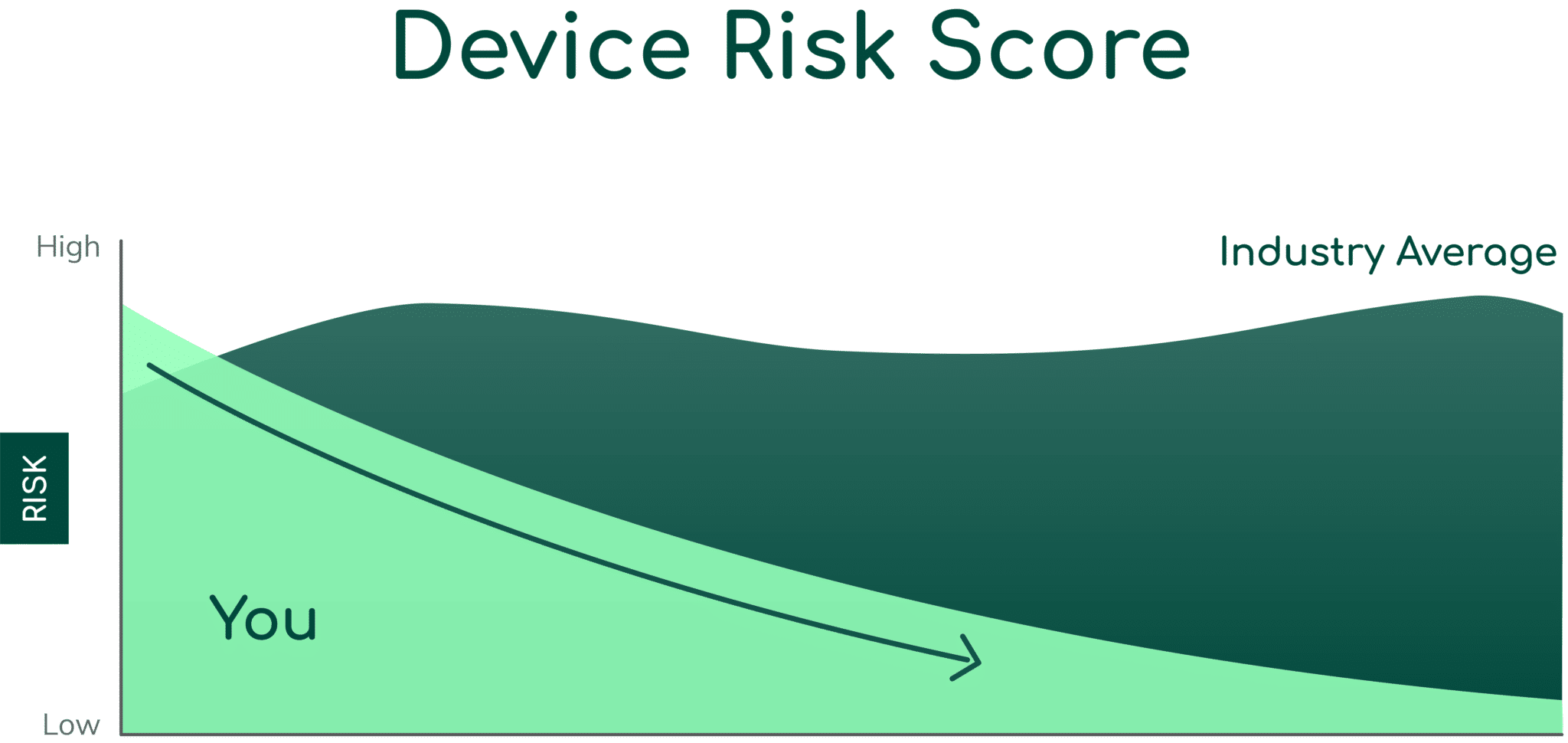
Read the Latest from Asimily
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.