The Next-Generation Cyber Asset and Exposure Management Platform
With Asimily, manage exposure across your entire cyber asset attack surface – IT, IoT, OT, and IoMT. Visibility, Vulnerability Management, Risk Mitigation, Threat Response, and Governance, Risk, and Compliance.
- Inventory and Visibility. Keep an accurate inventory of current and new cyber assets, using safe, passive traffic monitoring.
- Vulnerability Mitigation. Mitigate vulnerabilities efficiently with pinpoint fixes that remove the biggest risk.
- Anomaly Detection and Incident Response. Monitor assets, detect anomalous behavior, and alert operators to remediate any identified anomalies.
- Risk Modeling. Envision, predict, and act with unparalleled confidence, and unlock a new era of proactive risk mitigation.
Schedule a Demo with an Asimily Expert
Why Asimily?
Security Starts With Visibility
Keep every device you depend on up and operational, starting with an automated inventory. Protect them all via a single dashboard, with actionable information ready for your whole team.
Learn More
Don’t Let Vulnerabilities Manage You
To threat actors, all connected devices are simply attack vectors. Asimily helps end the IoT and IoMT security deficit by prioritizing and mitigating the most critical vulnerabilities, not simply managing them.
Learn MoreMinimize Incident Harm, Speed Investigations, and Recover Fast
At Asimily, we understand the importance of efficient, timely incident response (IR) across large and diverse device landscapes. That’s why we provide a comprehensive solution that enables IR teams from detection to resolution.
Learn More
Ensure Compliance with Standards and Regulations
Achieve regulatory compliance with industry best practices (such as NIST) for risk reduction for devices.
Learn MoreReduce Device Vulnerabilities 10x Faster
Mitigate vulnerabilities efficiently with pinpoint fixes that remove the biggest risk. Asimily analyses of exploitability yields quick fixes, not big projects..
Learn More
Fast Forensics For Any Incident, Anywhere
Get easy, centralized packet capture when incidents occur. Set device behavior rules to spot concerning anomalies.
Learn More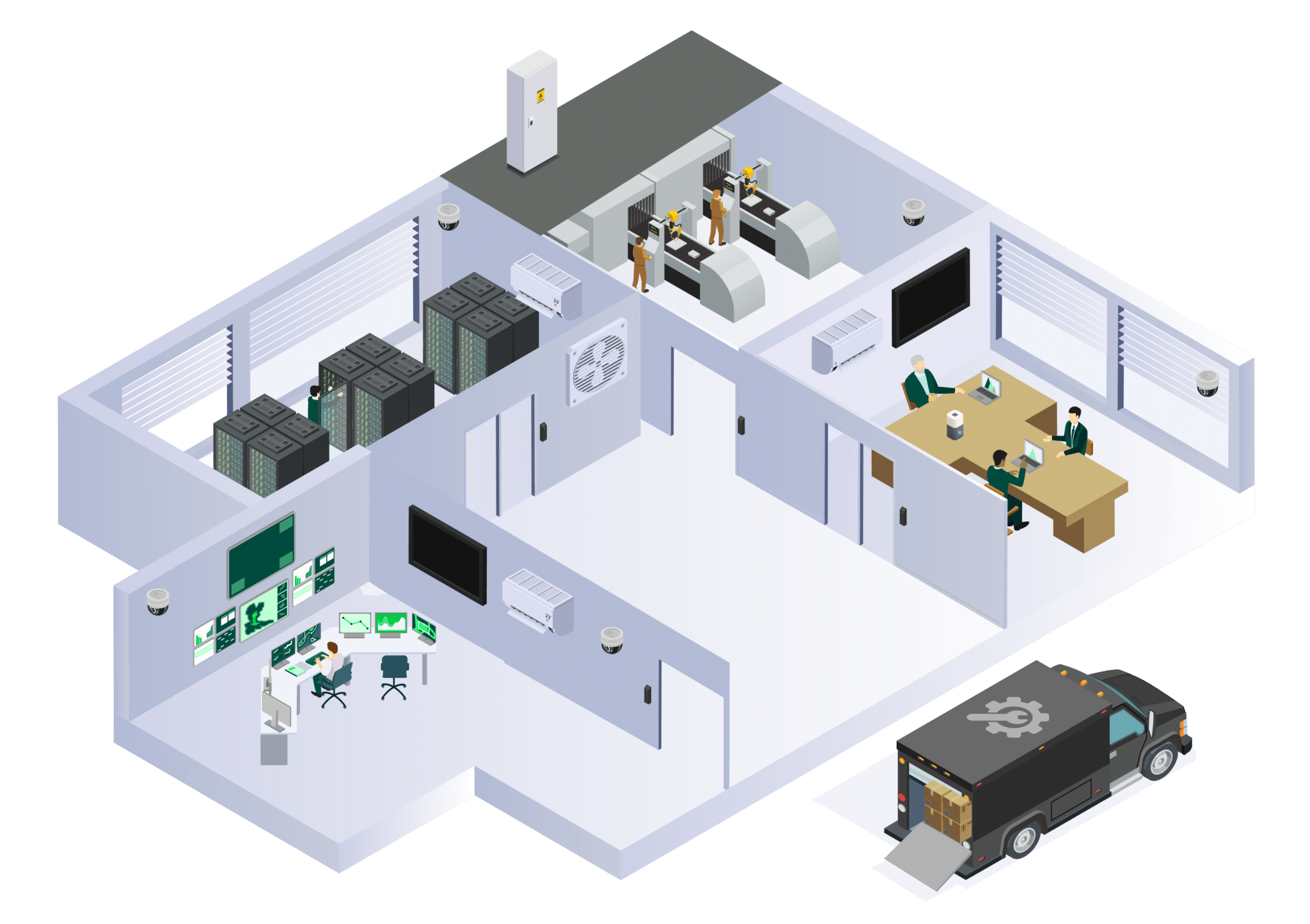
Act Confidently for Every Device’s Lifecycle
Model device risk pre-install, not while on the network. See the risk reduction of your work, before you get to work.
Learn More
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.









