Securing IoT Under CMMC

Attackers continuously target the defense industrial base (DIB), the organizations that have contracts with the US Department of Defense (DoD). In an attempt to better secure the DIB, the DoD established the Cybersecurity Maturity Model Certification (CMMC) program that requires organizations to provide compliance documentation as part of the contract bid process.
In December 2024, the DOD published the final rule implementing CMMC and its associated security measures for safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). These are 2 classes of unclassified information worth some protection, but not as stringent as more secret information requires. The final rule discusses the different compliance levels, assessment types, and security requirements that organizations need to know when engaging in the DoD contracting process.
CMMC does pertain to Internet of Things (IoT) devices. Organizations seeking to obtain or maintain DoD contracts should understand how their IoT security posture can impact their compliance and their ability to work with the DoD.
What is the Cybersecurity Maturity Model Certification (CMMC)?
CMMC is a program that intends to create consistent cybersecurity compliance requirements across DoD contractors and subcontractors to help safeguard FCI and CUI. All members of the DIB need to prove compliance by engaging in self-assessments or third-party audits before being granted a contract award.
The CMMC requirements apply to all DoD solicitations and contracts wherein a DIB member will be processing, storing, or transmitting:
- Federal Contract Information (FCI): information not intended for public release that the government provides or contractor generates for the government as part of a contract for delivering products or services
- Classified Uncontrolled Information (CUI): information that the government or an entity creates or possesses as part of a contract that also falls under a law, regulation, or Government-wide policy requiring safeguarding or dissemination controls
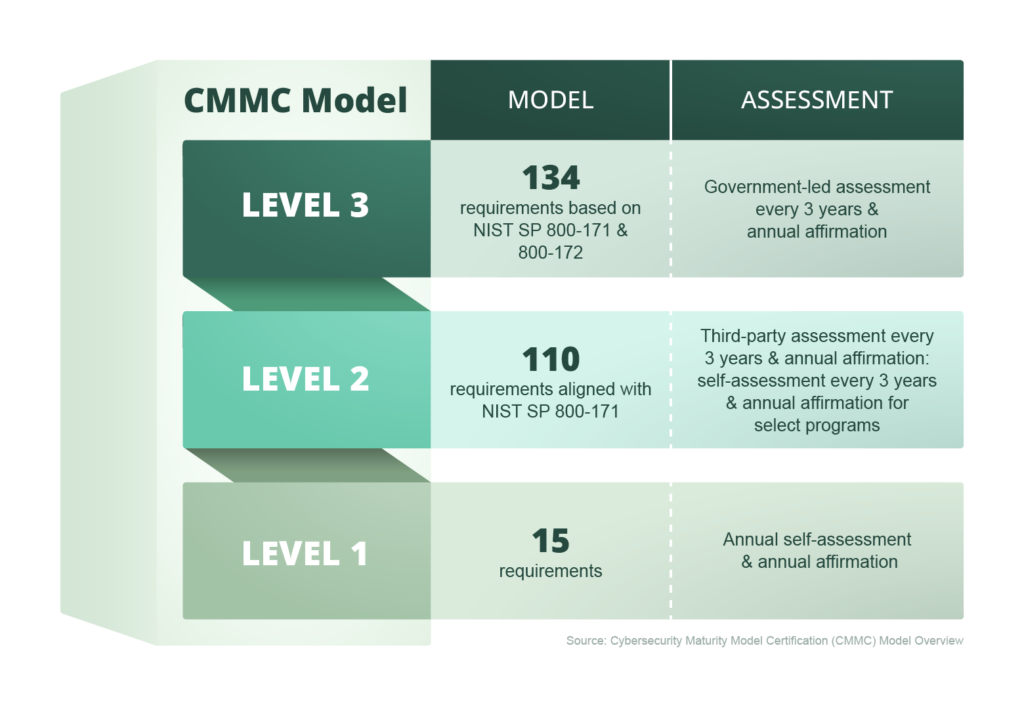
Under the final rule, generally referred to as CMMC 2.0, DIB members fall within one of the following three compliance categories:
- Level 1 Basic Safeguarding of FCI: Basic cyber hygiene requiring an annual self-assessment and affirmation of compliance with 15 security requirements listed in the Federal Acquisition Regulations System (FARS) “Basic Safeguarding of Covered Contractor Information Systems”
- Level 2 Broad Protection of CUI: Compliance with 110 requirements as shown through a self-assessment or third-party assessment every three years as outlined in the solicitation based on the information processes, transmitted, or stored on contractor or subcontractors systems
- Level 3 Higher-Level Protection of CUI Against Advanced Persistent Threats: Compliance with 134 requirements proving achievement of CMMC Final Level 2 stats and assessments every three years by the Defense Contract Management Agency’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC)
Where does the National Institute of Science and Technology (NIST) Special Publication (SP) 800-171 r3 fit into CMMC?
The DoD assumes that the majority of the DIB will fall into some form of Level 2 compliance requirements. As part of achieving the certification, organizations are directed to NIST SP 800-171 r3 and its 110 controls across the following 14 control families:
- Access Control
- Awareness and Training
- Audit and Accountability
- Configuration Management
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Personnel Security
- Physical Protection
- Risk Assessment
- Security Assessment
- System and Communications Protection
- System and Information Integrity
Where Does IoT Fit into NIST SP 800-171 r3?
NIST SP 800-171 r3 defines, in footnote 3, a federal information system as systems used or operated by an executive agency, by a contractor of an executive agency, or by another organization on behalf of an executive agency and specifically includes the following
- operational technology (OT)
- Information technology (IT)
- Internet of Things (IoT) devices
- Industrial IoT (IIoT) devices
- specialized systems
- cyber-physical systems
- embedded systems
- sensors
At a minimum, organizations engaging in CMMC audits should incorporate IoT and IIoT devices into their compliance across the following controls.
3.1 Access Control
IoT devices use the organization’s wireless networks for remote access to systems, yet they often have minimal authentication and authorization control capabilities. Organizations should consider how they plan to implement the following controls:
- 3.01.01 Access Enforcement: implementing access control policies, including for remote access, for logical access to CUI and system resources and the enforcement mechanisms used
- 3.01.05 Least Privilege: limiting system and remote access for user and system processes to the least amount of access necessary to complete a specific duty or function
- 3.01.12 Remote Access: establishing usage restrictions, configuration requirements, and connection requirements for authorizing and routing remote access
Network segmentation is a key part of implementing appropriate logical access to data and systems. With Asimily, organizations can establish and maintain targeted segmentation to respond to IoT-specific risks by placing devices with shared security risk profiles on the same network segmentation. With targeted segmentation, organizations seeking to achieve CMMC compliance can implement IoT-focused risk mitigation techniques, including:
- Security governance
- Patching
- Device configuration management
- Upgrading or replacing insecure devices
3.3 Audit and Accountability
When incorporating IoT and IIoT into CMMC audits, organizations should consider how they plan to implement the following controls:
- 3.03.01 Event Logging: collecting log data relevant to system and environment security
- 3.03.05 Audit Record Review, Analysis, and Reporting: reviewing and analyzing system audit records and correlating them across different repositories for organization-wide situational awareness
Asimily enables organizations to incorporate IoT and IIoT devices into their audit and continuous controls monitoring by integrating this collecting and generating information about these devices so that organizations can correlate with other data from the environment. A device change timeline feature has proven popular with customers seeking to provide information to regulators.
3.4 Configuration Management
Organizations seeking CMMC compliance should ensure that they implement and maintain secure configurations across all IoT and IIoT devices. Organizations should consider how they plan to implement the following controls:
- 3.04.01 Baseline Configurations: setting, documenting, and reviewing baseline configurations for connectivity, operation, and communications
- 3.04.04 Impact Analyses: analyzing the potential security impacts that changes to the system would have
- 3.04.06 Least Functionality: configuring system and components to provide only critical capabilities, including restricting the use of functions, ports, protocols, connections, and services
- 3.04.10 System Component Inventory: developing, documenting, reviewing, and updating an inventory of all hardware, software, and firmware in the system
Asimily enables organizations to implement several of these security controls for the IoT and IIoT deployments. Configuration Control maps very nicely to 3.04.01. Our passive scanner enables organizations to incorporate these devices into their system component inventory by creating an accurate profile that includes:
- Operating system
- IP address
- MAC address
- Port numbers
- Applications
- Hostname
- Version number
When organizations engage in their impact analyses, they can use Asimily to model risk around their IoT and IIoT deployment by:
- Simulating device risk scenarios that calculate which configurations minimize risk
- Identifying the configurations that will have the least risk impact within their unique environments
- Comparing similar device types to find the ones that achieve business objectives while minimizing security risks
3.6 Incident Response
As threat actors continuously look for new ways to gain access to sensitive systems and data, incorporating IoT and IIoT device data into their incident response program. Organizations should consider how they plan to implement the following controls:
- 3.06.01 Incident Handling: implementing incident-handling capabilities consistent with the incident response plan, including preparation, detection and analysis, containment, eradication and recovery
- 3.06.02 Incident Monitoring, Reporting, and Response Assistance: tracking, documenting, and reporting system security incidents
- 3.06.03 Incident Response Testing: testing the incident response capabilities to determine effectiveness and identify potential weaknesses or deficiencies
- 3.06.05 Incident Response Plan: developing and implementing a coordinated approach to incident response, including the structure for and high-level approach to incident response
Asimily enables organizations to respond to security incidents by collecting and storing forensic data that they can integrate into their security event information management (SIEM) tool or other security incident detection and response tool, including the following capabilities:
- Capturing traffic from any device in a centralized location that can be saved to their preferred destination
- Identifying the optimal blocking services or ports that still allow a device to function
- Helping quarantine compromised devices or segment them away from other assets quickly
3.11 Risk Assessment
The risk assessment process helps organizations focus their security controls around the most likely and most impactful potential threats. When incorporating IoT and IIoT into CMMC compliance, organizations should consider how they plan to implement the following controls:
- 3.11.01 Risk Assessment: Considering threats, vulnerabilities, likelihood, and adverse impacts to operations and assets based on unauthorized access to CUI
- 3.11.02 Vulnerability Monitoring and Scanning: monitoring for and remediating vulnerabilities, including patch levels, function, ports, protocols, services, and misconfigurations across the organization and its supply chain
Asimily’s risk assessment capabilities enable organizations to gain insight into:
- What devices contain vulnerabilities
- If threat actors’ can use the devices in an attack
- How an attack on those devices would impact service delivery
Organizations seeking to achieve CMMC compliance can then leverage Asimily’s risk modeling capabilities to identify mitigation activities to reduce risk.
Asimily’s passive scanning solution enables organizations to identify vulnerabilities and prioritize remediation activities by analyzing:
- Security data that the manufacturer supplies
- Open-source software components that developers used
- Vulnerability criticality
- Attacker tactics, techniques, and procedures (TTPs) that can use the vulnerability, using the MITRE ATT&CK framework-based analysis
Asimily eases the burdens of vulnerability remediation by providing actionable recommendations that include:
- Updating software and firmware
- Deactivating needed services to limit connectivity
- Blocking risky ports using a Network Access Control (NAC) tool
- Altering configurations to harden devices
3.12 Security Assessment and Monitoring
Proactive security monitoring should help organizations mitigate risk and detect incidents faster. When including IoT and IIoT into their compliance program, organizations should consider how they plan to implement the following controls:
- 3.12.01 Security Assessment: determining whether the safeguards and countermeasures are implemented correctly, operating as intended, and producing the desired outcomes
- 3.12.03 Continuous Monitoring: engaging in ongoing and continuous system level monitoring for awareness of security posture
Asimily enables organizations to identify cybersecurity key performance indicators and gain visibility into risk, including:
- Creating baselines
- Identifying target objectives
- Tracking trends over time
- Comparing security posture to peers
With Asimily’s platform, organizations can enhance their continuous monitoring capabilities by:
- Identifying suspicious activity deviating from normal behavior
- Enabling them to set smart policies aligned to unique threat detection needs
- Receiving detection policies from Asimily when new and active threats emerge, such as log4j
- Integrating with their incident management platform or security incident and event management (SIEM) tool
3.13. System and Communications Protection
IoT and IIoT devices connect to and communicate across the organization’s networks and the public internet. To bring these within their CMMC compliance program, organizations should consider how they plan to implement the following controls:
- 3.13.01 Boundary Protection: monitoring and controlling communications at external managed interfaces, implementing subnetworks to physically or logically separate public and internal network components, and using external systems through managed interfaces
- 3.13.12 Collaborative Computing Devices and Applications: prohibiting the remote activation of collaborative computing devices, like white boards, microphones, and cameras
Asimily’s platform enables organizations to implement targeted segmentation that makes monitoring and controlling communications at external managed interfaces easier. The IoT-focused security solution helps organizations manage IoT devices used for collaboration, like mitigating risks from white boards or smart TVs used during video conference calls.
3.14. System and Information Integrity
IoT and IIoT devices often collect, store, and transmit sensitive information, so organizations should consider how they plan to incorporate them when implementing the following controls:
- 3.14.01 Flaw Remediation: identifying systems affected by known software and firmware flaws, including vulnerabilities resulting from them, and updating them with patches, service packs, and hotfixes
- 3.14.03 Security Alerts, Advisories, and Directives: using publicly available sources of system security alerts and advisories to identify potential risks
- 3.14.06 System Monitoring: monitoring inbound and outbound communications traffic to identify attacks, indicators of potential attacks, unauthorized connections, and unauthorized system use
With Asimily’s platform, organizations can incorporate IoT-focused threat intelligence to identify potential security flaws that require remediation. Additionally, Asimily monitors IoT and IIoT communications to identify suspicious activities, like communications that can potentially be with a command and control (C2) server.
3.16. System and Services Acquisition
This section focuses on leveraging the principles of system security engineering, including legacy devices. To comply with CMMC, organizations should consider how they will implement the following controls:
- 3.16.02 Unsupported System Components: replacing unsupported system components or identifying other risk mitigation strategies when unable to replace unsupported components
Asimily’s simple remediation suggestions can apply to unsupported devices by offering alternative risk mitigation strategies, like disabling functionalities or blocking risky ports.
3.17. Supply Chain Risk Management
IoT and IIoT devices are fundamentally a supply chain risk that organizations need to mitigate. Organizations should consider how they will implement the following controls:
- 03.17.01 Supply Chain Risk Management Plan: developing a plan for assessing supply chain risk, identifying risk response actions, and monitoring plan performance across research, development, design, manufacturing, acquisition, delivery, integration, operations, maintenance, and disposal of the system, system components, or system services
- 3.17.02 Acquisition Strategies, Tools, and Method: developing and implementing acquisition strategies, contract tools, and procurement methods to identify, protect against, and mitigate supply chain risks
Organizations can use Asimily to engage in meaningful, data-driven risk assessments as part of their supply chain risk management processes. By simulating device risks before purchasing the devices, organizations can more precisely calculate risk and gain visibility into the mitigations that would enhance security.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




