The Importance of Policy-Based Action in IoT Security

The Internet of Things (IoT) has driven a complete overhaul of the healthcare industry. While the technology offers numerous advantages for improved patient care, many new medical devices lack the needed IoT security. Each device connected to the internet represents a potential security risk, which not only puts vulnerable patients at risk, but could also be an entry point into healthcare network infrastructure.
A robust IoT security solution is imperative for patient safety, data protection at scale, and business security. Issues such as a security breach slowed incidence detection and remediation, or a security team that’s dealing with alert fatigue and high rates of false positives mean it’s time to adopt policy-based action functionality.
What Is Policy-Based Action Functionality in IoT Security?
Healthcare providers invest in medical devices to save lives, yet these devices come with significant security risks. Taking into account factors such as operational complexity, limited threat protection, and access based on trust, it’s no easy feat to protect healthcare networks and their data.
As its name suggests, Asimily’s policy-based action functionality executes automatic actions based on a policy. Asimily understands that organizations often work according to their own security policies, and that all vulnerabilities aren’t equal.
Asimily’s IoT security solution allows you to customize a policy on any device—based on any parameter. The result is 100% visibility across all devices in respect of your internal guidelines and metrics. This helps detect malicious threats, such as “low and slow” data exfiltration, that other solutions might miss.
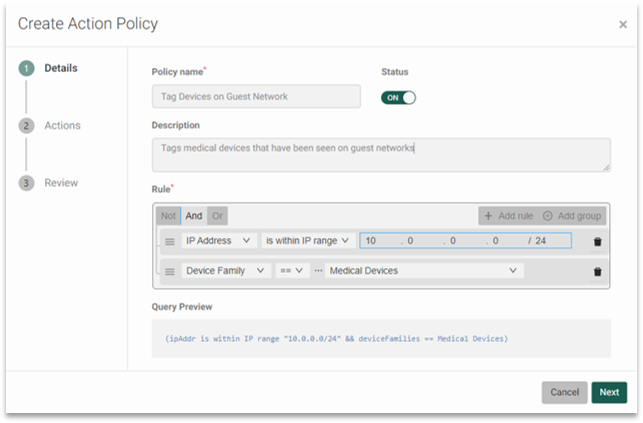
What Are the Benefits of Policy-Based Action Functionality in Healthcare?
Policy-based action functionality offers multiple healthcare security advantages:
- Improved threat detection
- Automated containment and mitigation, so platform tools can resolve attacks with minimal human intervention—freeing up staff to focus on other priority tasks
- Faster security risk response times
- More precise and accurate detection, which reduces the number of manual alert investigations needed
- Consistent and continuous enforcement of security policies
- Reduced business expenses, such as labor and operational costs
- Reduced debilitating losses due to long downtimes and security breaches
- Stronger compliance, thanks to managed reporting and decreased regulatory complexity
Common Use Cases of Policy-Based Action Functionality in IoT Security
Policy-based action functionality can assist in tighter security measures across the board for your IoT devices.
For example, it allows for closer scrutiny of who exactly is accessing the network—when a device is on the guest network, you can tag its origination point as such right away. The same labelling extends devices originating from networks known to be segmented. This helps you flag which devices to focus more attention on, for safety considerations.
Policy-based action functionality also lets you extend network restrictions across devices. You can suppress actions on specific networks, following the assumption that devices on said network already have an action blocked.
Automatic device clearing parameters also keep access tidy: you can mark devices for deletion if they have not been in the past 30-90 days (or whatever parameters you choose).
Is Outdated IoT Security Costing You?
The median downtime of business-critical apps after a cybersecurity incident is 14 hours, costing an average of $200,000 per hour. When it comes to the internet of medical things (IoMT), this can also affect patient health.
Traditional endpoints in IoMT devices are all attack vectors to threat actors. Whatever your healthcare cybersecurity deficit, Asimily provides the solution by defending all devices in your network. As experts in the field, they are passionate about helping clients reduce operational inefficiencies and device downtimes. To safeguard your network’s critical healthcare data, schedule a no-obligation consultation with our experts today.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




