Catalyze Risk Reduction
Customized Program + Technical Management
Create a best-in-class IoMT cybersecurity program rapidly built from a combination of innovative technology, expert guidance, field experience, and proactive collaboration.
Request Consultation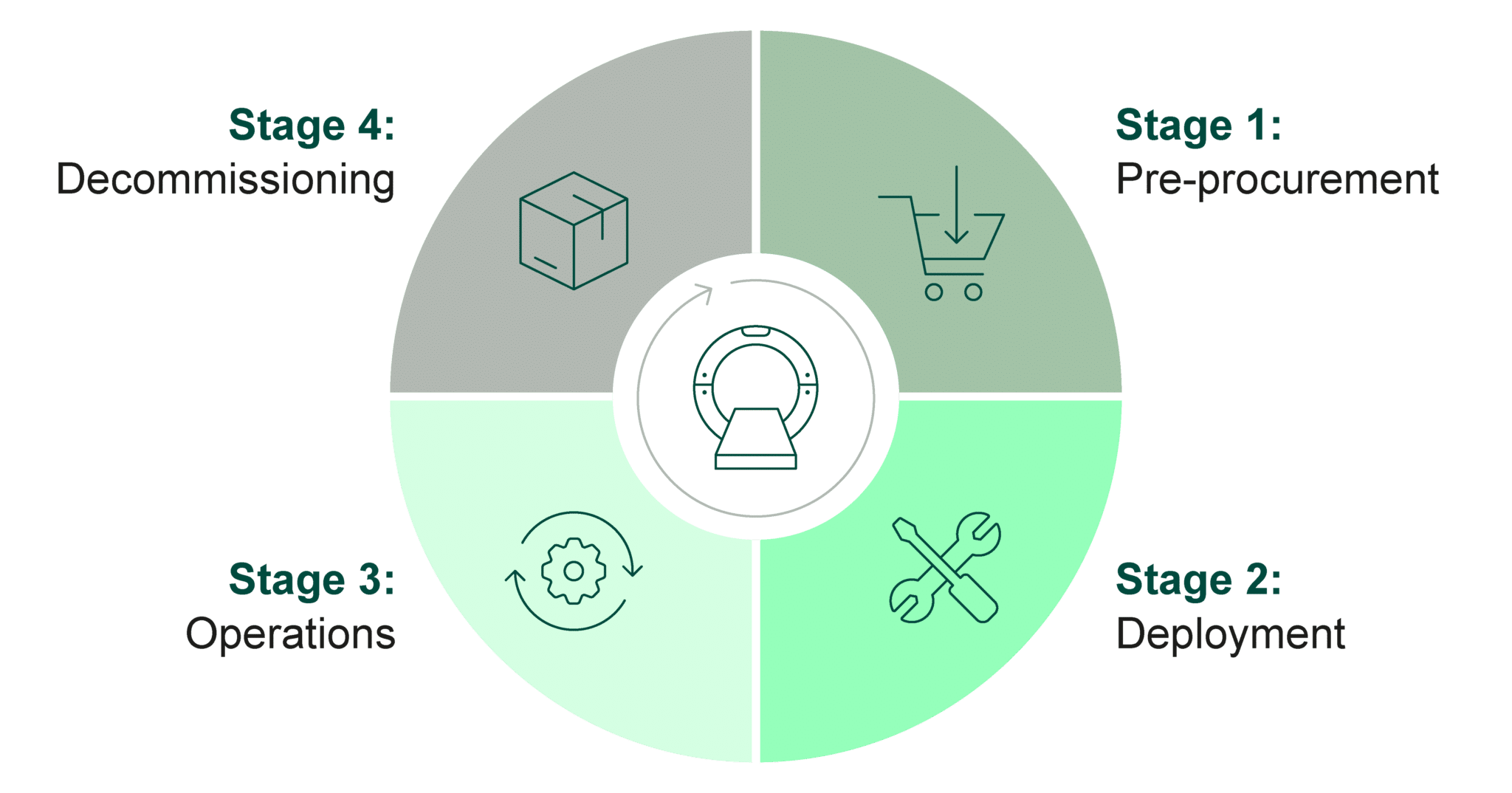
Risk Reduction through Innovative Technology & Customized Strategies
Asimily Risk Reduction Services Help You Scale Fast
Accelerate Operationalization
Blend product management, implementation experience, and data analytics to ensure seamless implementation, from phased rollout to scaling ongoing initiatives, including customized dashboards tailored to your risk reduction needs.
Build in-Product Collaboration
Swiftly address risky devices’ cybersecurity challenges by incorporating industry best practices for technology and process. Onsite HTM/CE/Biomed staff will be trained for product use, efficient protection of IoMT, and better reporting for compliance and other needs.
Proactively Remediate Risk
Utilize infrastructure, cybersecurity, and clinical operational experience to deliver evidence-based recommendations that facilitate risk reduction measures at the device and network levels.
Secure Better, Faster
One-Stop Shop for Reducing Risk
Tap into over two decades of cybersecurity, biomedical engineering, clinical engineering, design & development, and analytics experience to facilitate IoMT risk reduction.
IoMT Program Design
Leverage our expertise to design your IoMT cybersecurity transformation office – complete with a gap assessment, management action plan, executive & operational strategy, and more.
Enhance Training & Awareness
Leverage tailor-made workshops and training to enhance skills, and knowledge to foster cohesive adoption across your organization.
Integrated Support & Coordination
Prepare your team with vetted best practices and exercises that ensure cyber hygiene across the lifecycle of IoMT in your organization.
Flawless Program Implementation is Crucial to IoMT Security
A purpose-built IoMT platform can significantly increase visibility into connected devices and integrate into an HDO’s existing tech stack. However, effective and correct implementation is crucial to making the most out of this investment.
See Why
The Cost of Upgrading Connected IoMT Devices
Upgrading or replacing vulnerable IoMT devices to avoid the operational disruption of a cyber attack might be tempting, but can be a financially and operationally cumbersome endeavor. Learn how to future-proof your devices and secure the entire device lifecycle.
Learn More