What’s Best to Do Next can be Calculated
Stop Doing the
Wrong Thing Next
Triaging Mitigation is Hard
Most security teams have too many fixes to execute, all at once. Determining what is best to do next – triage – is usually left to informal methods. Usually, there’s no single, clear metric that can be used to compare potential work.
Guesswork is Imprecise
The risk reduction from any fix requires understanding the role of the device, its current network configuration, and the real-world exploitability and severity of a vulnerability. That’s more than a human mind can process, let alone at the scale of IoT device quantities.
Poor Triage Choices are Costly
Sometimes what seems to be the next best action is not when it comes to risk reduction. Fixing the most recent severe vulnerability might not actually reduce risk due to newly increased exploitability of an older vulnerability. Rigorous analyses are necessary. Worse, when IoT devices are remote, it gets even more costly to choose the wrong fix first.
IoT Device Security in 2024:
The High Cost of Doing Nothing
Protecting the growing IoT architecture
in a complicated security environment
Quantified. Fast. Integrated
How Asimily’s IoT Risk Simulator Saves Time
Asimily’s Risk Simulator allows IoT security fixes to be modeled with a click. You’ll easily see the before and after, to see if that action was worth the time and effort for risk reduction. The simple 0-10 Risk Score has subcomponents to better understand why risk can be reduced.
Quantified
Risk scores are precisely calculated based on all available information, even information that might not be known to security team members. That can include real-world exploitability of vulnerabilities, the importance of a device to the organization, or the presence of anomalies needing investigation.
Fast
Like a spreadsheet, the power of scenario analysis relied largely on speed. Being able to take a more secure scenario from imagination to simulation must happen in seconds, so many simulations can be run by an experienced operator. With a click, Risk Simulator does that.
Integrated
Device inventory, vulnerabilities, anomalies, threat intelligence, and more are all needed to have a holistic view of risk. That information is centralized with Asimily, to make its risk simulation easy to operate and use to save time and effort.
Forecast Risks to Better Avoid Them
With Asimily, foresight becomes your greatest ally. Envision, predict, and act with unparalleled confidence, and unlock a new era of proactive risk mitigation.
How it Works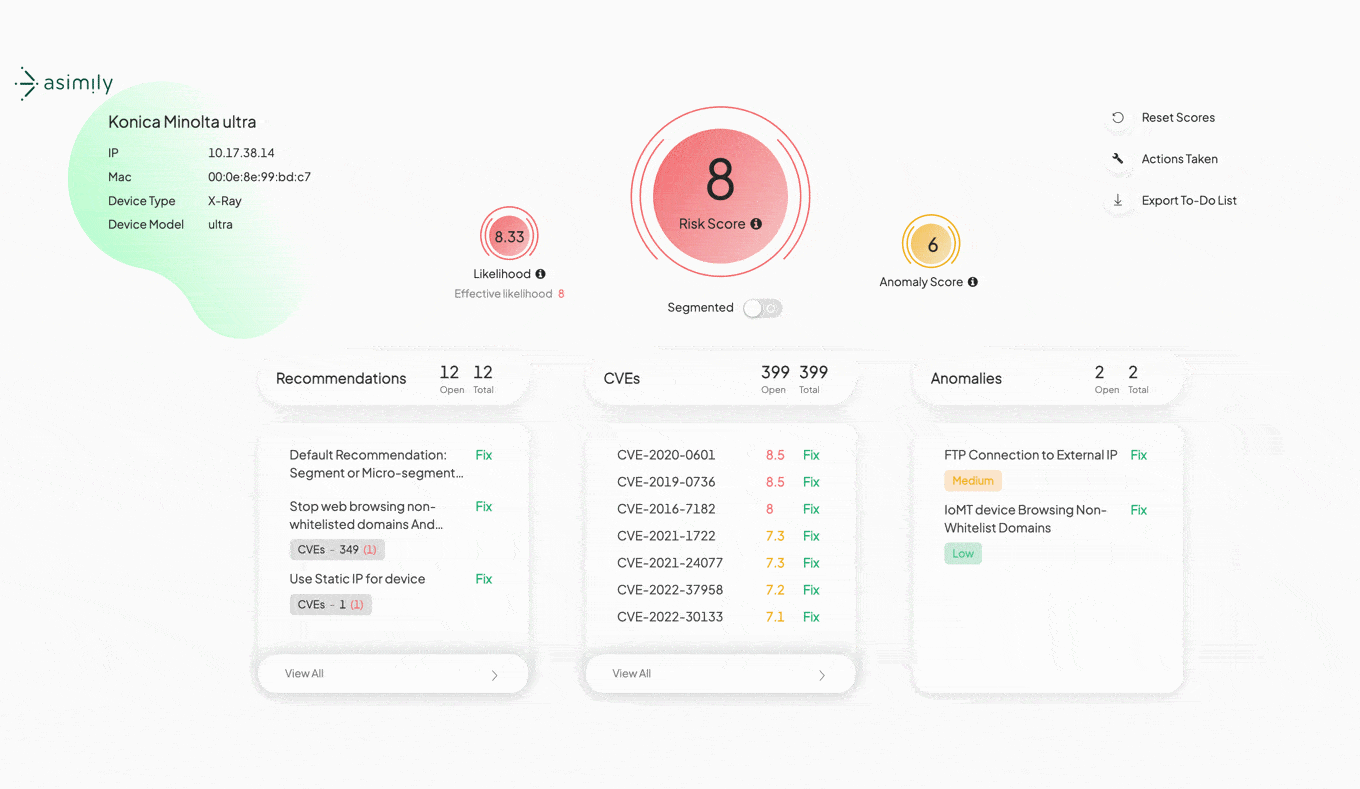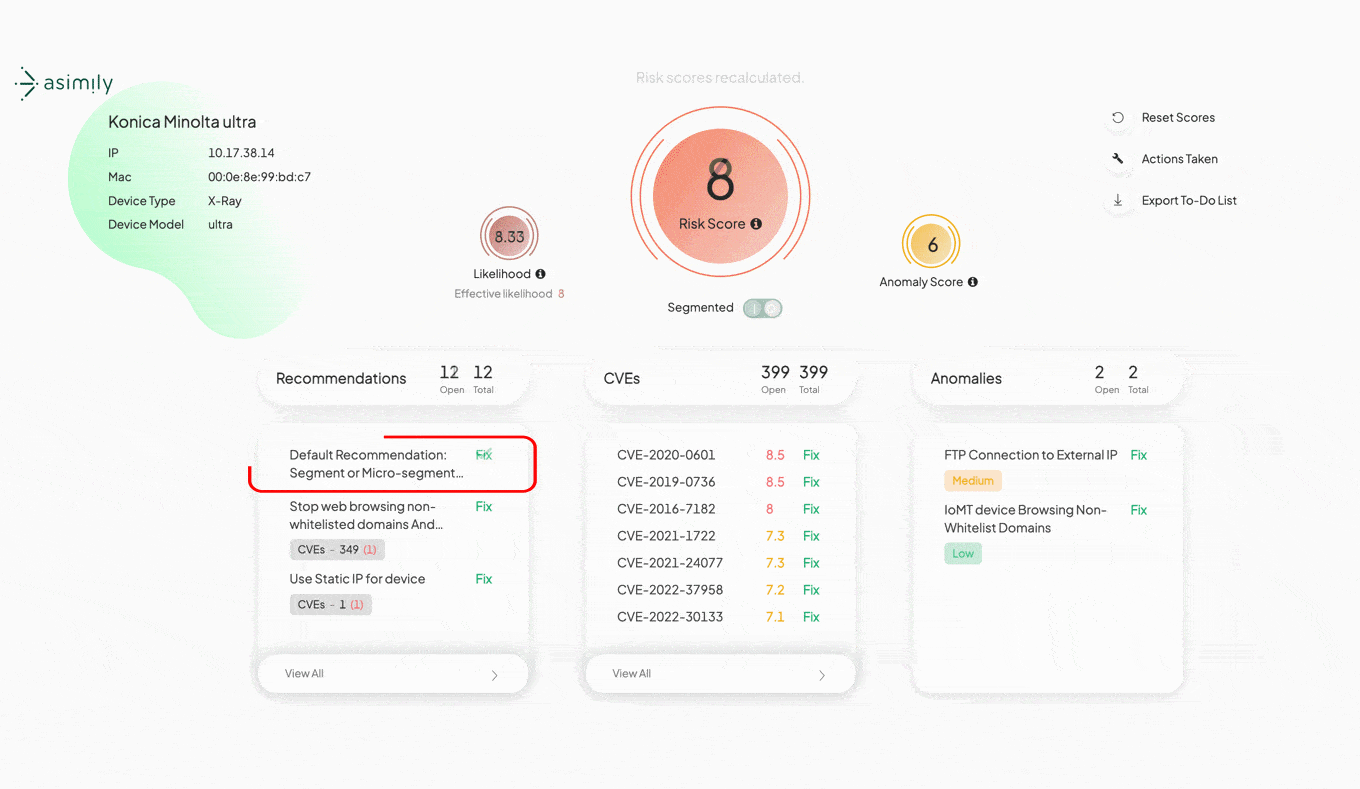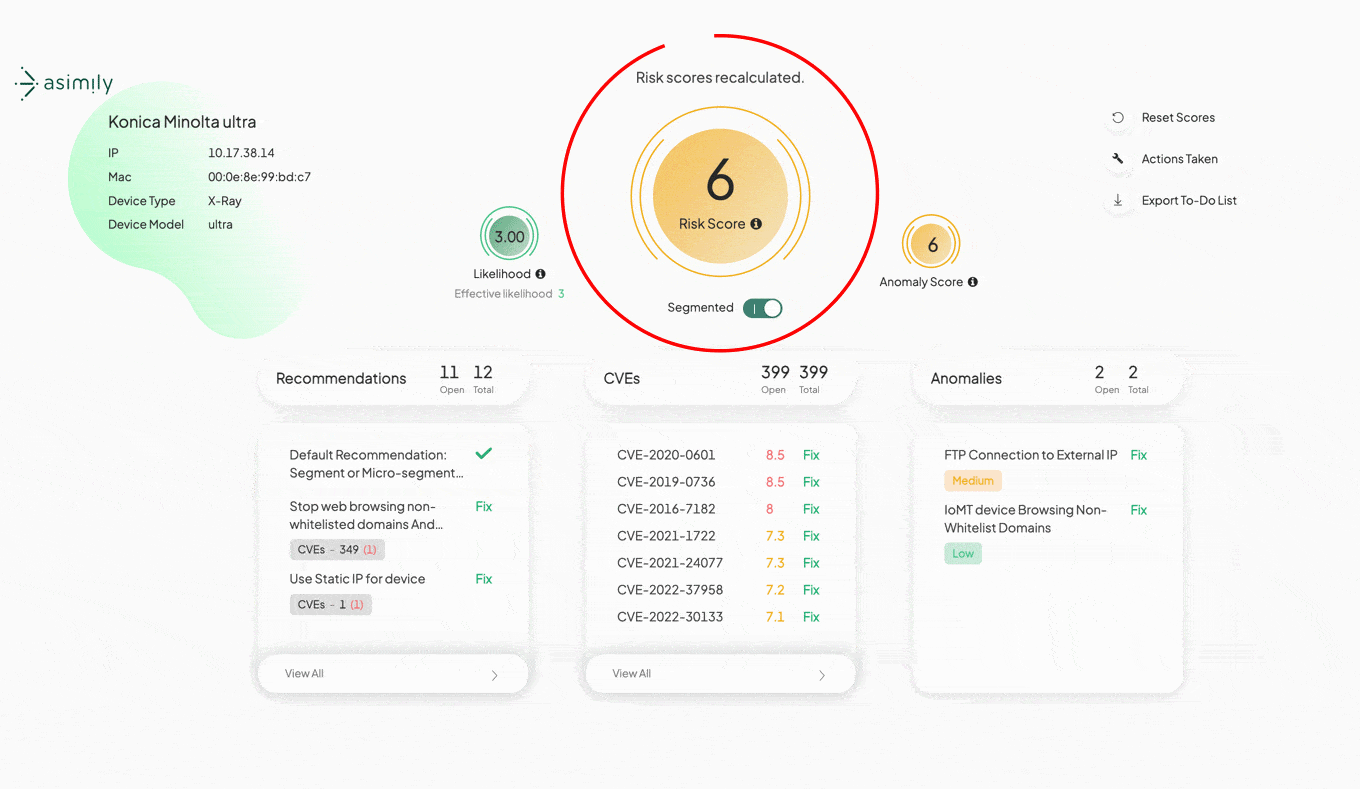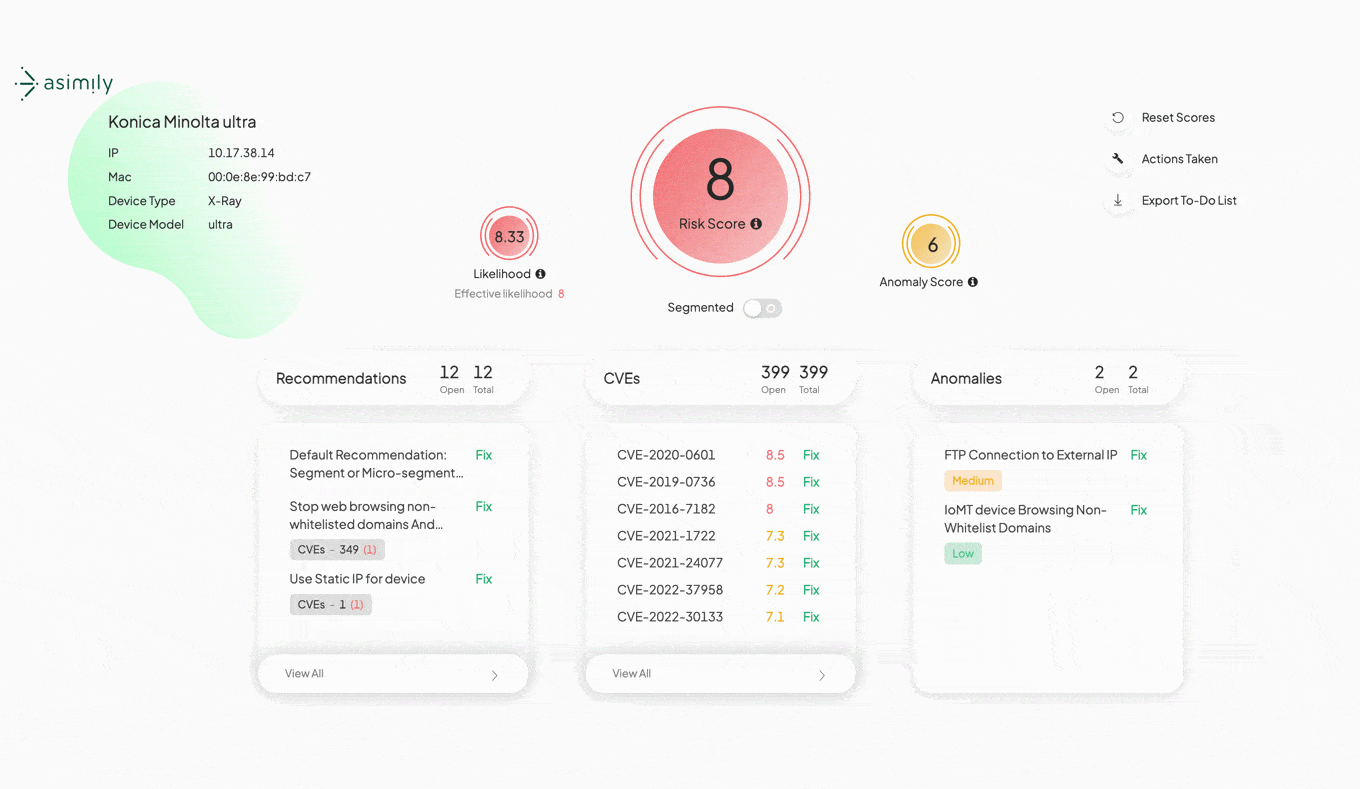
Shadow IoT: How Unmanaged Devices Put Companies at Risk
Shadow IT is a major business risk. Every new connected IoT hardware or software increases your attack surface. Learn how to secure your shadow IT devices.
Learn How






