Gain Complete Knowledge of all your IT, IoT, OT, and IoMT Devices
End “unmanaged” devices by finding them all


Device Visibility and Classification

Every Connected Device – Revealed and Protected
Gain a complete repository of IoT, OT, IoMT and IT devices while finding “unmanaged” devices. Protect devices during data gathering through a combination of passive, protocol-based, or API-based methods.
Get in TouchAutomated Inventory with Enriched Details
Your Entire Device Fleet Made Visible
Fast, Complete, and Safe Visibility
Asimily identifies devices safely based on their network traffic. With the industry’s best protocol analyzer, deep packet inspection (DPI), and AI/ML-based traffic analysis, Asimily finds and classifies each device into a family, along with all apps, services, and connections.
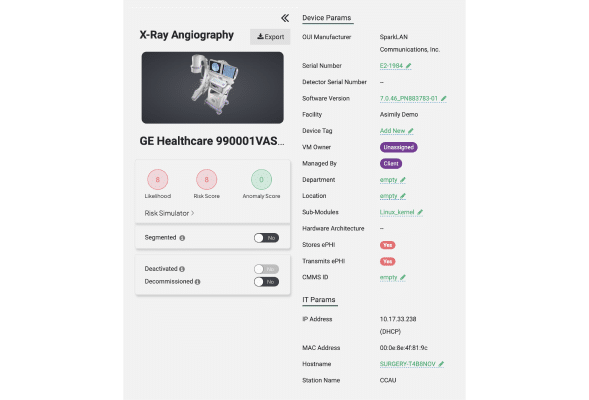
Single Source of Truth
Asimily gathers device information using passive-only or passive and active methods, depending on the monitored environment. Asimily also leverages other inventory sources – your CMDB, CMMS, and more – to provide a fast, complete inventory.

Enriched Inventory
Know each device’s metadata, configuration, components, applications and much, much more are with the device’s inventory record. Streamline auditing, reporting, configuration control, vulnerability detection and more.

Protocol Analyzer
The world’s best protocol analyzer does in days what used to take weeks. Quickly support any new or rare devices that are critical to your operation. Asimily supports your critical device infrastructure, now and in the future.

Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.
Protecting Your Industry’s Unique Devices
Healthcare
Asimily provides the necessary tools to identify and address IoT vulnerabilities in healthcare, ensuring the protection of patient data without interrupting the delivery of critical care.
Discover MoreManufacturing
In an industry that relies heavily on IoT devices to drive automation, efficiency, and connectivity, Asimly can help. By ensuring the security of IoT devices, manufacturers can safeguard their intellectual property, prevent production disruptions, and maintain the trust of their customers and partners.
Discover MoreHigher Education
Educational institutions depend on interconnected devices to facilitate learning, research, and campus operations. Protect sensitive student and faculty data, maintain operational integrity, and foster a secure, productive academic environment with Asimily.
Discover MoreGovernment
Asimily equips government entities worldwide with the necessary tools to secure their IoT devices, protect critical infrastructure, and ensure data privacy. Defend against cyber threats and uphold public trust by proactively mitigating vulnerabilities.
Discover MoreLife Sciences
Where delicate research, development, and data exchange are ongoing, securing your IoT devices is a top priority. Proactively manage and mitigate vulnerabilities, reducing the risk of theft or loss of critical research and development efforts.
Discover MoreFrequently Asked Questions
Inventory and visibility refers to the ability to have real-time visibility and accurate categorization of all hardware and software assets within an organization’s IT infrastructure. It involves maintaining a comprehensive inventory database, tracking asset details, and knowing the exact risk level and status of each asset at any given time.
Inventory and visibility are crucial for effective IoT asset management for several reasons: u003cbru003e1. Asset tracking: It allows organizations to safely determine the the status, risk levels, and usage of IoT devices, ensuring accountability and preventing shadow IT issues. u003cbru003e2. Compliance and licensing: Inventory visibility enables organizations to track software licenses, ensuring compliance with licensing agreements and avoiding legal risks associated with unauthorized software usage. u003cbru003e3. Budget optimization: By having accurate visibility into connected devices, organizations can optimize procurement, avoid over-purchasing, and make informed decisions regarding asset lifecycle management. u003cbru003e4. Incident response: When incidents occur, having inventory visibility enables organizations to quickly identify affected assets, assess the impact, and respond promptly.
IT asset management (ITAM) refers to the set of practices and processes used by organizations to track, manage, and optimize their IT assets throughout their lifecycle. It involves activities such as inventory management, asset tracking, software license management, maintenance scheduling, and financial planning related to IT assets.
1. Cost savings: By effectively managing assets, organizations can avoid unnecessary purchases, optimize maintenance costs, and extend the useful life of assets. u003cbru003e 2. Compliance and risk mitigation: IT asset management ensures compliance with software licensing agreements, reduces the risk of security incidents, and helps organizations demonstrate readiness for regulatory bodies.u003cbru003e 3. Improved productivity: Efficient asset management leads to better asset utilization, reduced downtime, faster incident response, and improved overall productivity. u003cbru003e 4. Enhanced decision-making: Accurate data and insights from IT asset management enable informed decision-making regarding technology investments, upgrades, and decommissioning.
Inventory and visibility and IT asset management enhance security by: u003cbru003e 1. Identifying vulnerabilities: Having a complete inventory of IoT devices helps organizations identify vulnerabilities and security risks associated with outdated or unsupported hardware or software. u003cbru003e2. Patch management: Accurate inventory visibility enables prompt application of security patches and updates for vulnerable assets, minimizing the risk of exploitation.u003cbru003e3. Incident response: Inventory visibility allows quick identification of compromised assets during security incidents, facilitating timely assessment and appropriate remedial actions.u003cbru003e 4. Access control: Accurate asset tracking enables effective access controls, ensuring that only authorized personnel can interact with specific assets, reducing the risk of unauthorized access or data breaches.






