Reduce Risk with the World’s First Complete Risk Mitigation Platform
Only complete solution for IoT, OT, and IoMT context-aware risk reduction, 180+ targeted fixes, and automatic IoT Patching.
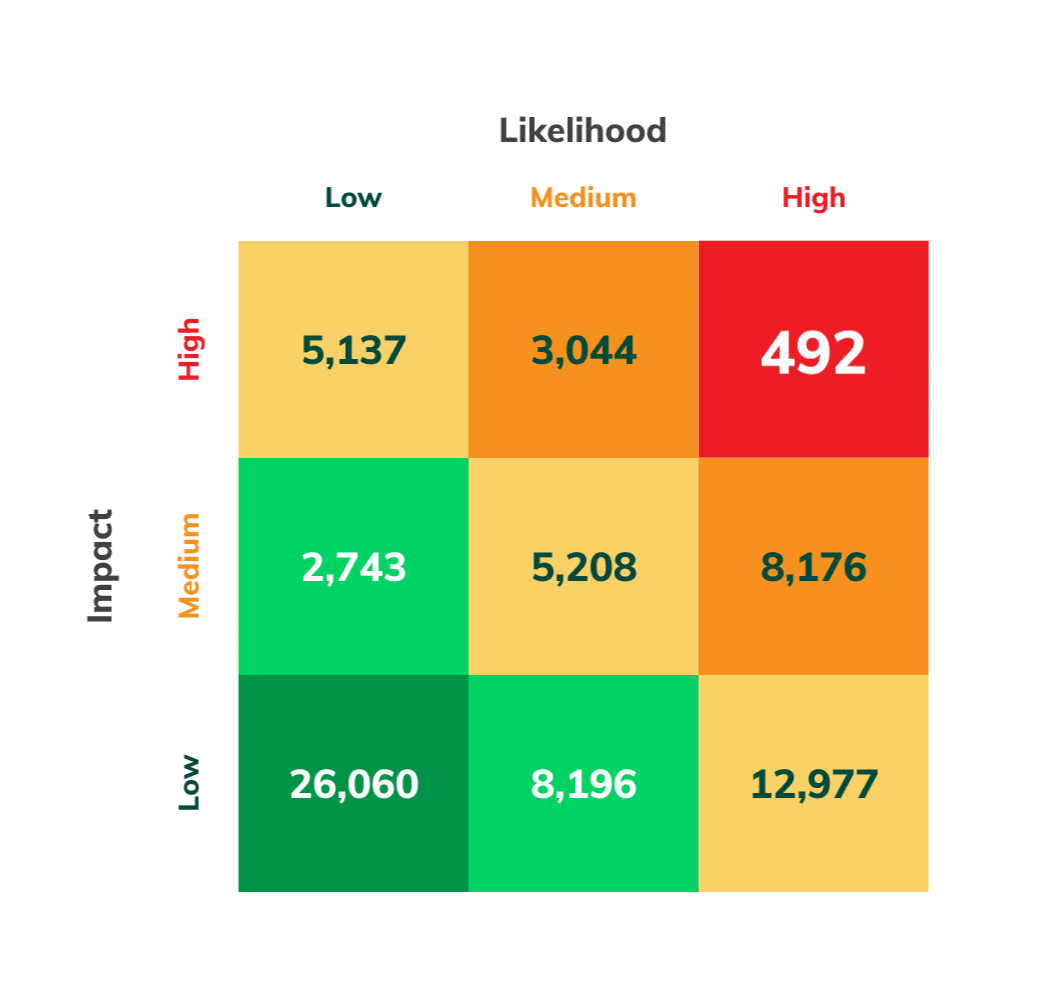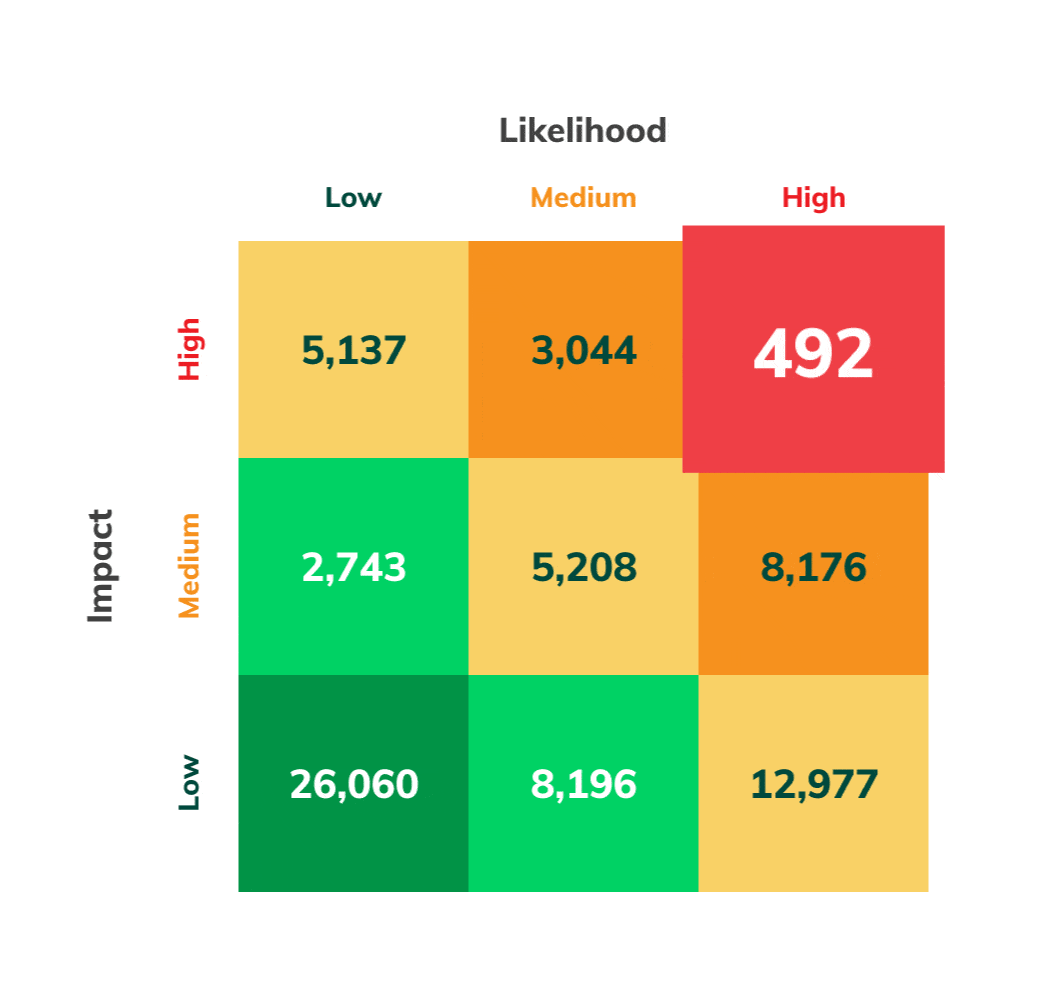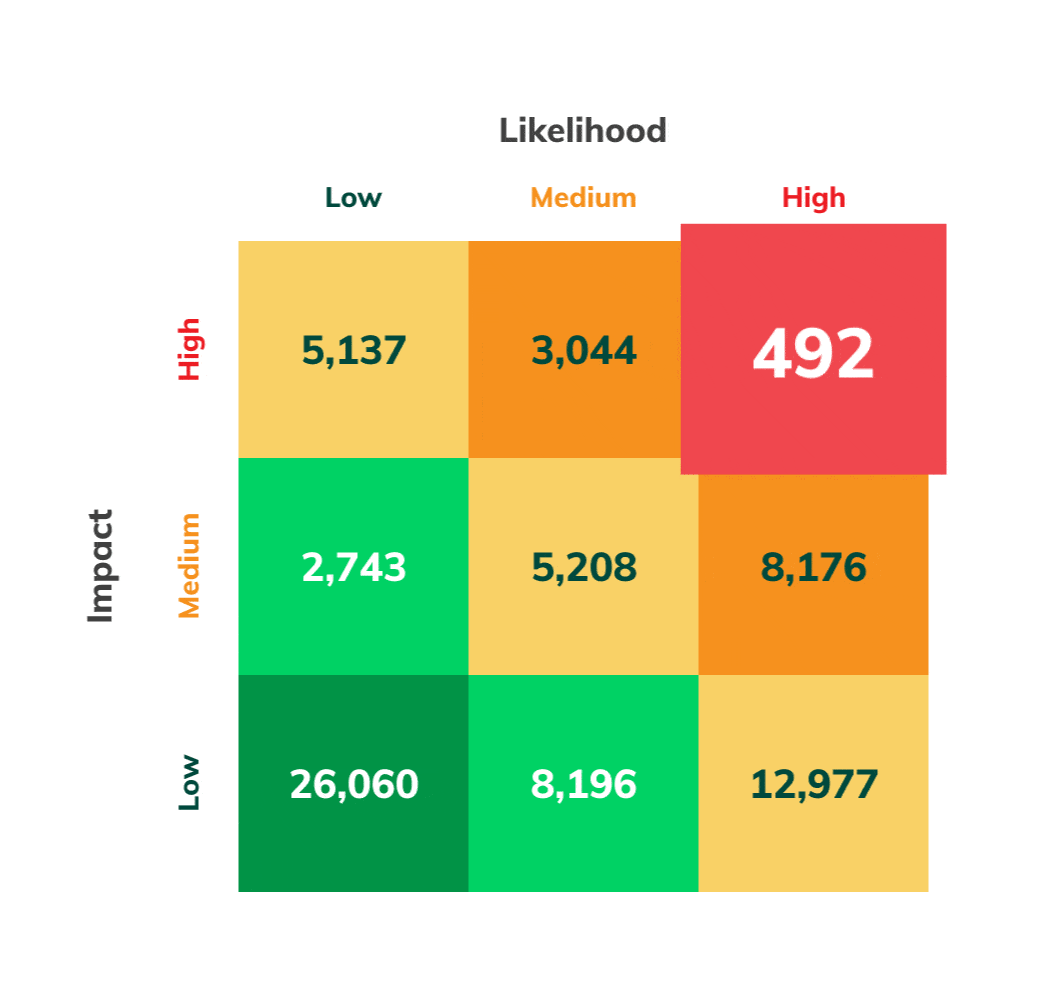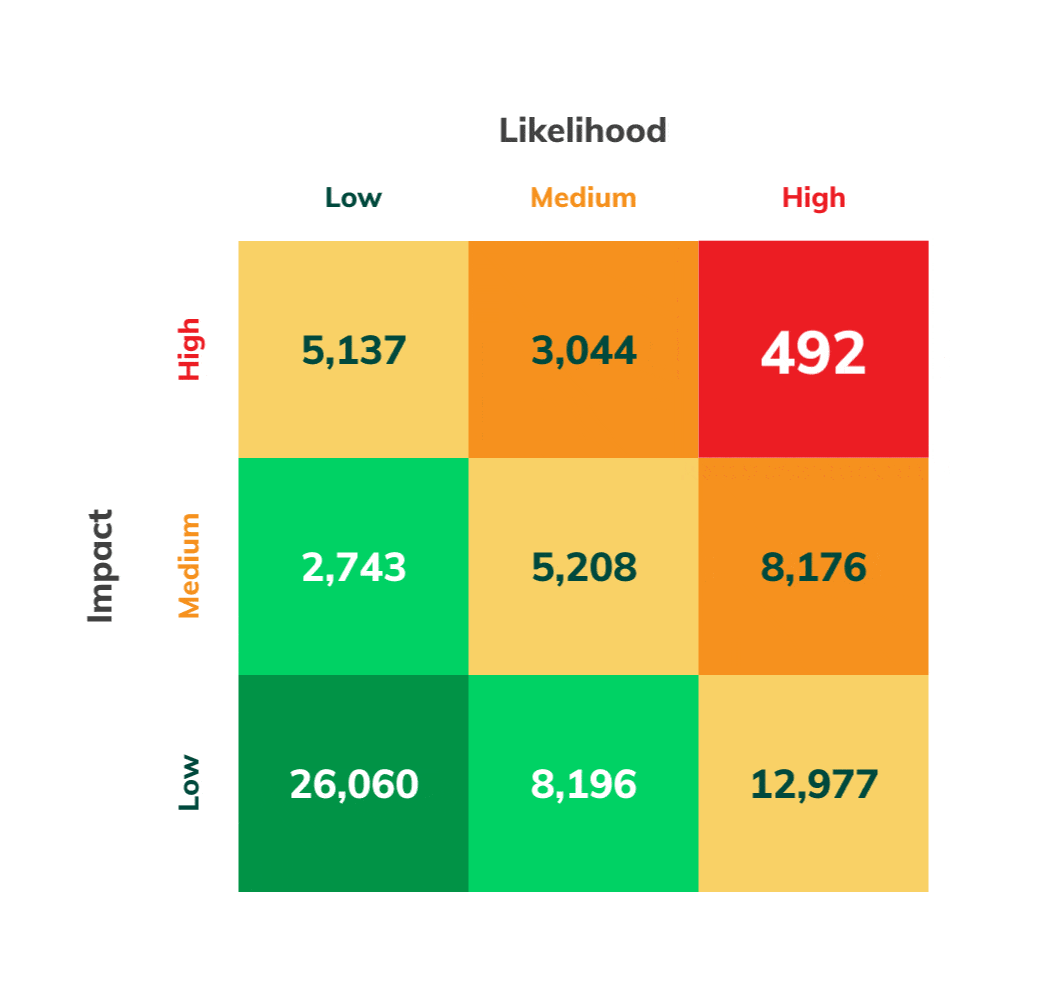

Risk Mitigation

Block Exploits From Succeeding
Your job is to reduce risk quickly. Asimily combines the most powerful techniques possible to stop attacks – enabling you to divert and block them – or patch a vulnerable device. With Asimily Labs analyzing each vulnerability, you gain evidence-backed mitigation steps as soon as you need them. The result: speedy risk reduction without the guesswork.
Get in TouchRisk Mitigation for IoT, OT, and IoMT devices
Secure Today, Secure for the Future
Block Attack Paths for Devices
Attackers need a specific path to successfully exploit vulnerable IT, IoT, OT, and IoMT. Asimily understands acceptable and unacceptable network traffic based on device type, network configuration, and function – combined with Asimily Labs’ enhanced vulnerability research. With easy-to-create segmentation rules orchestrated through existing NACs and firewalls, your network and its devices can be safer than ever.

Block Exploits from Succeeding
Asimily uses patented AI/ML techniques to analyze each vulnerability to learn how to stop the exploit that uses it. As long as device function is preserved, these fixes that do not effect device operation (such as blocking specific services) act as targeted segmentation to mitigate risk quickly and easily.

Patch the Right Device at the Right Time
Each risk that can be closed now is flagged for customers and ranked for urgency based on Asimily’s context-aware scoring. Asimily’s IoT Patching takes patching speed and efficiency to a new level – with automated, scheduled, and bulk options to close vulnerability windows faster than ever before.

Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.
Protecting Your Industry’s Unique Devices
Healthcare
Asimily provides the necessary tools to identify and address IoT vulnerabilities in healthcare, ensuring the protection of patient data without interrupting the delivery of critical care.
Discover MoreManufacturing
In an industry that relies heavily on IoT devices to drive automation, efficiency, and connectivity, Asimly can help. By ensuring the security of IoT devices, manufacturers can safeguard their intellectual property, prevent production disruptions, and maintain the trust of their customers and partners.
Discover MoreHigher Education
Educational institutions depend on interconnected devices to facilitate learning, research, and campus operations. Protect sensitive student and faculty data, maintain operational integrity, and foster a secure, productive academic environment with Asimily.
Discover MoreGovernment
Asimily equips government entities worldwide with the necessary tools to secure their IoT devices, protect critical infrastructure, and ensure data privacy. Defend against cyber threats and uphold public trust by proactively mitigating vulnerabilities.
Discover MoreLife Sciences
Where delicate research, development, and data exchange are ongoing, securing your IoT devices is a top priority. Proactively manage and mitigate vulnerabilities, reducing the risk of theft or loss of critical research and development efforts.
Discover MoreFrequently asked questions
Common types of IoT device vulnerabilities include weak or default passwords, outdated firmware or software, insufficient authentication mechanisms, insecure data transfer and storage, lack of device management, and poor physical security.
IoT device vulnerabilities can have significant consequences for your organization. They can lead to data breaches, unauthorized access to systems, disruption of operations, compromised privacy, financial losses, reputational damage, and even physical harm in certain cases.
Most organizations face more vulnerabilities than they have the resources to immediately address. Prioritization helps prevent potential exploits, reduces the risk of cyberattacks, ensures data privacy, and maintains the integrity and availability of IoT systems.
Assessment of risks should be conducted on a regular basis to keep pace with the evolving threat landscape. With exploits happening within hours after disclosure of a serious new vulnerability, organizations should expect to keep pace.






