The Hidden Costs of Data Collectors in IoT, OT, and IoMT Security

When monitoring sensitive OT (Operational Technology) and IoMT (Internet of Medical Things) equipment, organizations that leverage these technologies must be able to safely gather data from each device. This has always been difficult for these sensitive endpoints. Typically, IoMT and OT are monolithic units delivered by manufacturers, with no option to add software agents to aid defense and monitoring. OT and IoMT cannot risk unscheduled downtime, so active scanning that risks rendering these devices unusable (or worse for IoMT) is inadvisable.
To address this conundrum, many organizations leverage purpose-built security solutions for IoT, OT, and IoMT – aiming to reduce downtime while still effectively securing these devices. Every security vendor approaches this differently, however, in the tradeoff between cost, complexity, and data quality provided to the organization. While no one approach is perfect, some methods come with hidden costs, tradeoffs, and challenges that you need to be aware of before you decide to entrust the security of your connected device fleet.
The Challenge of Data Collection for Connected Devices
The great majority of manufacturers, hospitals, utilities, and other operators of OT, IoT, and IoMT face a challenge: how to safely gather data from each device without disrupting normal operations or incurring significant operational costs. Most organizations don’t architect their networks for packet capture and visibility as a primary goal, which can lead to challenges in discovering and securing these devices. For example, architecting a network to minimize switch costs or maximize simplicity can make it difficult for monitoring systems to have access to all the networking traffic they need. Many security vendors for IoT, OT, and IoMT have tried to solve this problem by always listening to network traffic from as close as possible to the data source, but this often requires the organization to use network sensors broadly, creating a costly, inefficient, and complicated deployment. The diagram below shows two possible ways of collecting data across these networks.
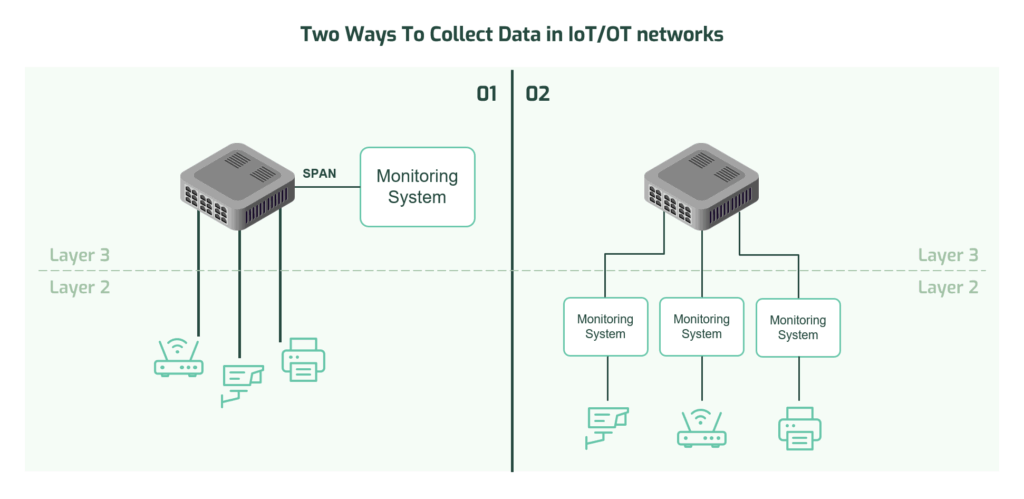
Different Approaches to Data Collection Result in Different Costs
To illustrate, let’s imagine a worst-case scenario for expensive data collection for IoMT and OT – where a one-size-fits-all approach to collectors can lead to an overpowered or underpowered deployment for the devices within an organization and their environments.
Let’s imagine that there’s a single, possibly hardened collector that is deployed regardless of network traffic, environment, or device type. With no flexibility in choice, the organization runs the risk of either deploying an overpowered collector that will incur higher upkeep costs or an underpowered collector that risks dropping packets from analysis*.
For this example, it may be more appropriate to have a less costly, simpler box, such as a sub-1U rack costing closer to a thousand dollars instead of potentially tens of thousands. These simpler collectors can be very suited for satellite offices and locations without heat, vibration, or access issues that benefit from a ruggedized form factor for OT data collection. And some “sites” have inherently small data collection potential, due to bandwidth constraints. Rolling stock, ships, and very remote locations all fall into this category.
The ideal solution for organizations is a flexible set of options for data collection throughout the network. For example, for deployments that require access to a core switch and a higher level of traffic, the collector connected to the SPAN port on that core switch will require high performance (CPU, throughput, and storage). Asimily offers six different options for collectors, tailored to an organization’s needs and environment, ensuring needs are appropriately and thoughtfully met for each organization.

Going Beyond the Box: Virtual Data Collection
Having both physical and virtual options for data collection adds even more flexibility. Some organizations have chosen to go the cloud-first route or operate in a hybrid model. As a result, they would prefer to deploy data collection in a virtual environment, such as a Virtual Machine or even a Container, rather than go through the complexity of adding more managed physical hardware to their environment. Collectors can be deployed in the cloud, if that is the source of monitored device traffic, or monitored devices can share their network activity to a cloud destination. Asimily offers both options, providing maximum flexibility and customizability for the organization.
Even with numerous options for data collectors, the placement of devices and the existing network architecture will partially dictate how many sensors are needed and where. Sensor deployment tends to bounce between Layer 3 (Network) and Layer 2 (Data Link) for most Asimily customers. Ideally, there’s enough bandwidth available to make 100% of device traffic available at Layer 3, where a powerful collector can be placed to centralize OT and IoMT (and IoT) traffic. Sometimes that’s not the case, and Layer 2 is the only place where a collector can be deployed to feed platforms like Asimily’s with the data needed to safely monitor and protect devices. Additionally, having too many collectors within the same deployment can happen when they are or must be pushed lower into the network, fully Layer 2 deployments, for example. Deploying only at Layer 2 tends to cost more, because more collectors are needed and the complexity is therefore increased. A flexible and tailored approach is especially helpful here to help mitigate cost – ensuring you’re not paying for a collector that is too powerful for the environment and organization’s needs.
Flexibility is Key: The Asimily Difference
Ultimately, the most important requirement organizations should seek is flexibility. All vendors in this space have a choice on how to optimize cost, complexity, and data quality. In vetting potential solutions for securing these devices, most organizations expect the upfront costs of the software and applicable services – but the hardware costs associated with inflexible Collector options can incur well after the initial deployment, once more information is available about the actual network topology and deployment needs.
Having virtual and multiple physical collector options, as in the case of Asimily, enables that flexibility for organizations. Asimily provides multiple options ranging from simple Containers to very high-performance physical collectors. All of this is to help our customers avoid hidden hardware and complexity costs when obtaining their IoT, OT, and IoMT risk reduction to stay ahead of attackers.
________________________________________________________________________________
*Admittedly, in many cases, having only some of the network traffic is sufficient. Getting most of a device’s traffic is enough to get the information necessary to identify and characterize the device for inventory and vulnerability management purposes.
Secure Every IoT Device.
Automatically.
Cyber threats move fast — so should you. Asimily gives instant inventory and smart, prioritized risk mitigation insights for every IoT, OT, and IoMT device — so you can take action before threats strike.




