Grading a Phishing Scam Made on a Cybersecurity Org. No Gift Cards for You!

By Rajesh F. Krishnan, Head of Product Marketing, Asimily
This morning, I received my first phishing scam attempt as an employee of Asimily. Since this was right in the middle of breakfast, but before a morning coffee, they got me at my most tired and cranky. I wanted to spend more time drawing them out, but that coffee was calling me.
Here’s how I grade their phishing scam attempt. I’ll try not to improve their repertoire either.
Phishing Scam Research: A-
My phone number, employment status at Asimily, and name are all matters of public record via LinkedIn, Twitter, and some basic searching. Since that information is easy to get, it’s completely worthless for convincing me that a message sender is who they say they are. But, it’s necessary to try to establish credibility, so nice job on that.
The message below actually came on multiple personal phone numbers at the same time with the same message, which was implausible…but good timing. They must program these to go out with some geo-coding to hit people in their local mornings.
Phishing Scam Spelling: B+
As a gent with South Indian roots myself, it’s nice to see people making the effort to spell names correctly, so thank you for that scammers. Much appreciated. Frankly, if my name was much longer, I’d misspell it more than not (Also, thanks Dad for keeping my name shorter than yours – 22 letters).
Since I actually do know our CEO (and his real phone number which was not the one they used), I knew this was not his communication style. The capitalization and punctuation weren’t what I’d expect from him. If it was written very plainly, it still wouldn’t sound like him. Everyone has their own style, and they didn’t get his right.
Phishing Scam Messaging: B
Of course, the “I’m in a meeting ploy” is numero uno, so entirely expected. I did expect more creativity and was a bit disappointed. I’ll withhold my specific suggestions to not make the scammers’ jobs easier. Or maybe it’s ChatGPT doing their work for them by now…
And the “this is my personal #” response is likely a default from their script/decision tree. Good job on the area code – plausible. I think they knew the jig was up at that point and were throwing a hailmary in case I bought that line.
Their actual response times to my texts were consistent with their claim to need something “urgently”. Much of the battle is to get a victim to respond before they can think about the issue.
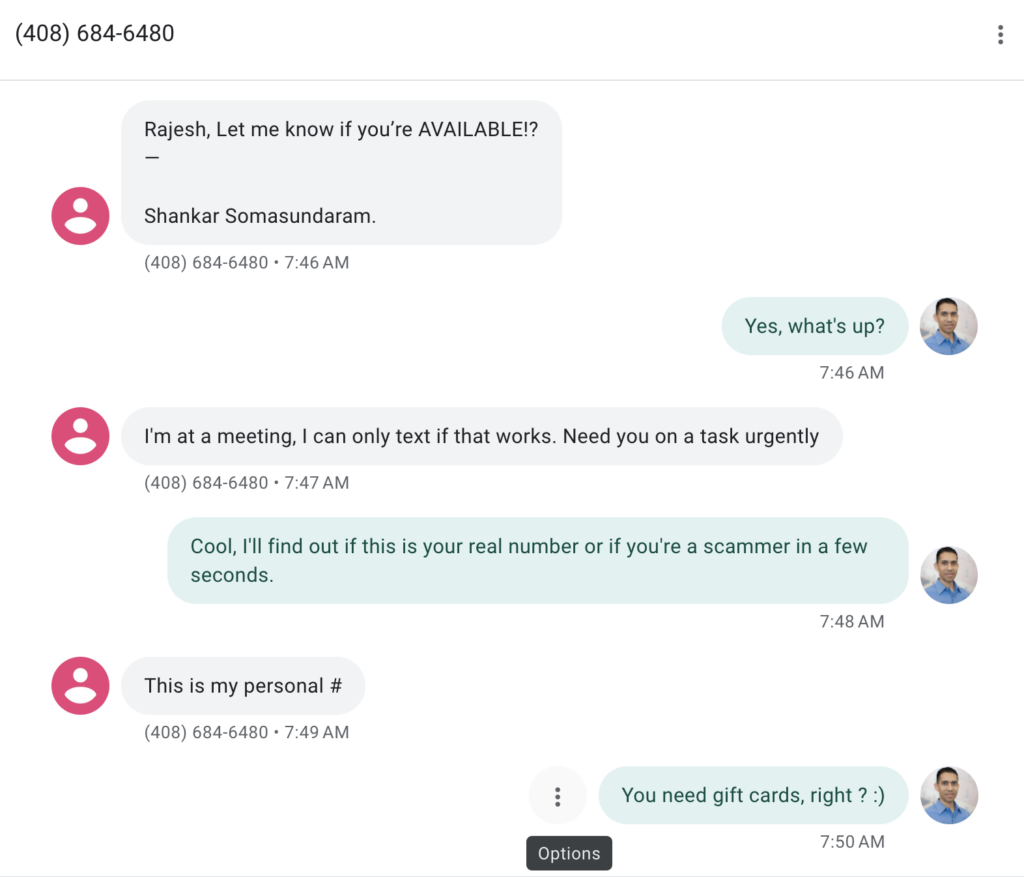
Fig. 1: The actual phishing attempt
Our exchange ended there and more importantly, I was able to get my coffee.
What can you do to protect your employees from such attempts?
Here are three ideas that scale whether you’re a large healthcare delivery organization (HDO) or a smaller, local hospital (or any other business for that matter).
- Let new employees know about prior phishing scam attempts; it shortens the time their brains will take to diagnose a phish as a phish.
- Self-phishing as a training exercise. Time the exercises to news events about your company to make them seem more plausible
- For CEOs and other senior leaders, periodically remind employees that you’ll NEVER make such urgent requests without authentication. That’s not even by voice anymore, with the improvements in deepfakes. Most CEOs have hours of publicly recorded messages that can be used to create a deepfake voice to scam employees and vendors.
Internally, I did share this information with the relevant people. This information was also duly reported to the Federal Trade Commission. I’ll applaud the FCC as well for taking steps to keep this away from consumers with their March 2023 release of their first rules against Scam Texting, requiring carriers to block the most blatantly fraudulent attempts at the network level
Finally, I don’t think this phone number will be in use for long; both my carrier and Google should have seen my spam flag and it should get blocked on their end pretty quickly.
Stay frosty!
Reduce Vulnerabilities 10x Faster with Half the Resources
Find out how our innovative risk remediation platform can help keep your organization’s resources safe, users protected, and IoT and IoMT assets secure.




